Reading view
The Danger of IP Volatility, (Sat, Feb 15th)
What do I mean by “IP volatility”? Today, many organizations use cloud services and micro-services. In such environments, IP addresses assigned to virtual machines or services can often be volatile, meaning they can change or be reassigned to other organizations or users. This presents a risk for services relying on static IPs for security configurations and may introduce impersonation or data leakage issues.
This morning, I was setting up a new environment. I got a new IP address assigned by my hosting company and deployed a classic configuration: a reverse-proxy redirecting to many web services and generating Let’s Encrypt certificates.
Once the reverse proxy was in place, I started to deploy more services but detected some activity in the log (always keep an eye on your logs!) and saw this:
{"level":"debug","time":"2025-02-15T06:22:33Z","caller":"github.com/traefik/traefik/v3/pkg/tls/tlsmanager.go:228","message":"Serving default certificate for request: \"postmaster.xxxxxxxx.hu\""}
{"level":"debug","time":"2025-02-15T06:46:36Z","caller":"github.com/traefik/traefik/v3/pkg/tls/tlsmanager.go:228","message":"Serving default certificate for request: \"pop3.xxxxxxxx.hu\""}
{"level":"debug","time":"2025-02-15T07:04:16Z","caller":"github.com/traefik/traefik/v3/pkg/tls/tlsmanager.go:228","message":"Serving default certificate for request: \”xxxxxxxx.hu\""}
A quick DNS request confirmed that these hosts are resolving to my newly assigned IP!
Worse, this organization seems to still be using POP3, and a user (or a script) is still trying to fetch emails using this protocol!
Some tips:
- When you move to another hosting solution, update your DNS records
- Cleanup your DNS zones and remove unwanted entries
- Use mechanisms to preserve your IP addresses (like “Elastic IPs” provided by AWS)
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
Fake BSOD Delivered by Malicious Python Script, (Fri, Feb 14th)
I found a Python script that implements a funny anti-analysis trick. The script has a low score on VT (4/59) (SHA256:d716c2edbcdb76c6a6d31b21f154fee7e0f8613617078b69da69c8f4867c9534)[1]. This sample attracted my attention because it uses the tkinter[2] library. This library is used to create graphical user interfaces (GUIs). It provides tools to create windows, dialogs, buttons, labels, text fields, and other interactive elements, allowing developers to build desktop applications with visual interfaces in Python. Most Python scripts are intended to be executed from a command line. That's why I consider this library as a good sign of suspicious behavior (It does not mean that all Python scripts using this library are malicious!)
While reviewing the script, a variable contains an interesting piece of text:
info = "\nA problem has been detected and windows has been shut down to prevent damage\nto your computer ... (removed) ..."
The interesting piece of code is here:
root = tk.Tk()
root.configure(background="dark blue")
ex = Example(root)
w, h = root.winfo_screenwidth(), root.winfo_screenheight()
root.overrideredirect(1)
root.geometry("%dx%d+0+0" % (w, h))
root.wm_attributes("-topmost", 1)
root.mainloop()
The attribute "-topmost" set to "1" or "TRUE" will make the window remain open on top of all windows. The window will also be created to fill the screen without any control elements to close or resize it. When the script is executed, you will get this screen:
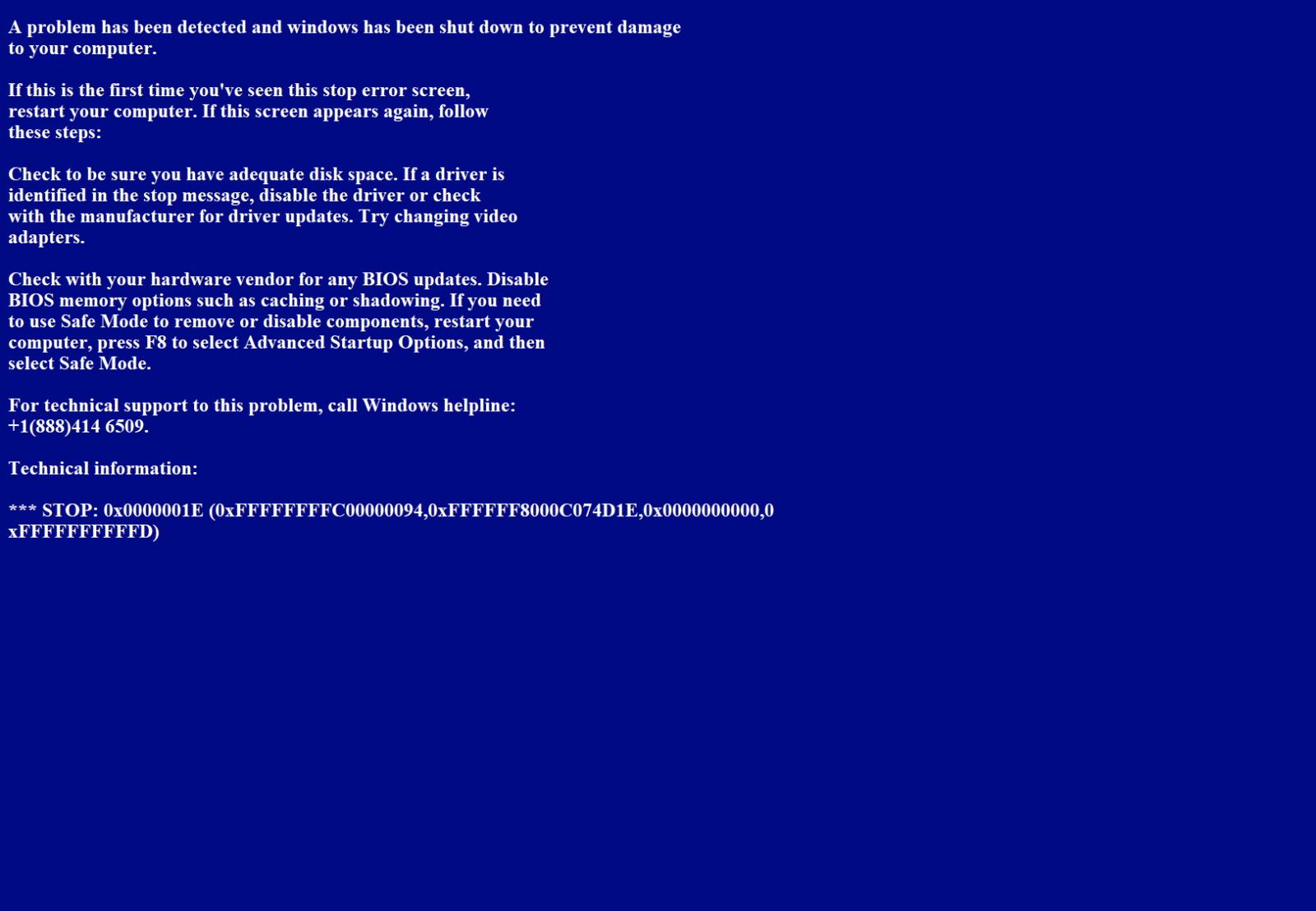
To be honest, that's not the best BSOD ("Blue Screen of Death") that I saw... but it's a nice trick to annoy the victim or slow down (a bit) the analysis of the file.
[1] https://www.virustotal.com/gui/file/d716c2edbcdb76c6a6d31b21f154fee7e0f8613617078b69da69c8f4867c9534/detection
[2] https://docs.python.org/3/library/tkinter.html
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key