It takes two: The 2025 Sophos Active Adversary Report





































Authorities in India today arrested the alleged co-founder of Garantex, a cryptocurrency exchange sanctioned by the U.S. government in 2022 for facilitating tens of billions of dollars in money laundering by transnational criminal and cybercriminal organizations. Sources close to the investigation told KrebsOnSecurity the Lithuanian national Aleksej Besciokov, 46, was apprehended while vacationing on the coast of India with his family.

Aleksej Bešciokov, “proforg,” “iram”. Image: U.S. Secret Service.
On March 7, the U.S. Department of Justice (DOJ) unsealed an indictment against Besciokov and the other alleged co-founder of Garantex, Aleksandr Mira Serda, 40, a Russian national living in the United Arab Emirates.
Launched in 2019, Garantex was first sanctioned by the U.S. Treasury Office of Foreign Assets Control in April 2022 for receiving hundreds of millions in criminal proceeds, including funds used to facilitate hacking, ransomware, terrorism and drug trafficking. Since those penalties were levied, Garantex has processed more than $60 billion, according to the blockchain analysis company Elliptic.
“Garantex has been used in sanctions evasion by Russian elites, as well as to launder proceeds of crime including ransomware, darknet market trade and thefts attributed to North Korea’s Lazarus Group,” Elliptic wrote in a blog post. “Garantex has also been implicated in enabling Russian oligarchs to move their wealth out of the country, following the invasion of Ukraine.”
The DOJ alleges Besciokov was Garantex’s primary technical administrator and responsible for obtaining and maintaining critical Garantex infrastructure, as well as reviewing and approving transactions. Mira Serda is allegedly Garantex’s co-founder and chief commercial officer.
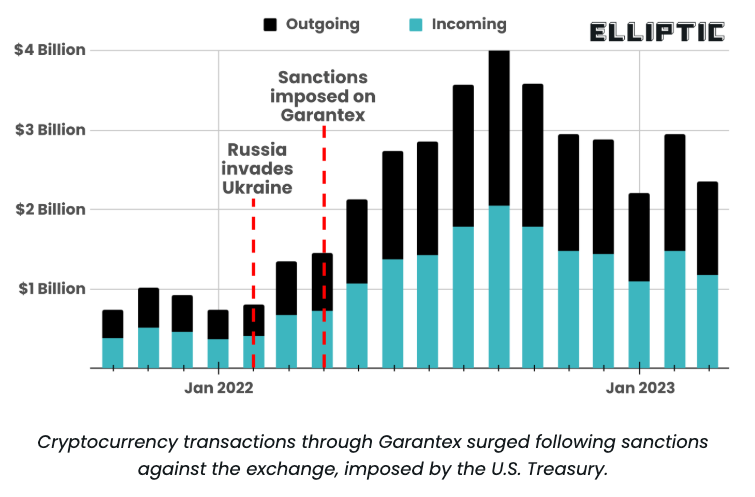
Image: elliptic.co
In conjunction with the release of the indictments, German and Finnish law enforcement seized servers hosting Garantex’s operations. A “most wanted” notice published by the U.S. Secret Service states that U.S. authorities separately obtained earlier copies of Garantex’s servers, including customer and accounting databases. Federal investigators say they also froze over $26 million in funds used to facilitate Garantex’s money laundering activities.
Besciokov was arrested within the past 24 hours while vacationing with his family in Varkala, a major coastal city in the southwest Indian state of Kerala. An officer with the local police department in Varkala confirmed Besciokov’s arrest, and said the suspect will appear in a Delhi court on March 14 to face charges.

Varkala Beach in Kerala, India. Image: Shutterstock, Dmitry Rukhlenko.
The DOJ’s indictment says Besciokov went by the hacker handle “proforg.” This nickname corresponds to the administrator of a 20-year-old Russian language forum dedicated to nudity and crudity called “udaff.”
Besciokov and Mira Serda are each charged with one count of conspiracy to commit money laundering, which carries a maximum sentence of 20 years in prison. Besciokov is also charged with one count of conspiracy to violate the International Economic Emergency Powers Act—which also carries a maximum sentence of 20 years in person—and with conspiracy to operate an unlicensed money transmitting business, which carries a maximum sentence of five years in prison.
Bylin: Jeffrey Wheatman, Senior Vice President, Cyber Risk Strategist
Cybersecurity teams are always on alert for the next attack, but the most dangerous threats are often the ones no one sees coming.
Silent breaches — often unnoticed vulnerabilities within third-party networks — are becoming one of the most pervasive cybersecurity challenges. While the rise of interconnected IT ecosystems has fueled efficiency, it’s also created entry points for attackers that often go undetected until it’s too late.
As organizations rely more on third-party suppliers, cloud services, and digital infrastructure, they are increasingly vulnerable to risks beyond their direct control. In Black Kite’s 2025 Third-Party Breach Report, we took a closer look into the most significant breaches of 2024 to shed light on the silent breach phenomenon, including why it’s so hard to detect these threats and how you can mitigate them in the year ahead.
Silent breaches are particularly dangerous because they don’t just impact one company — they cascade through entire industries and supply chains, amplifying the damage. Several high-profile incidents from 2024 illustrate just how far-reaching these threats can be:
These incidents highlight the systemic nature of silent breaches, where vulnerabilities in one organization can quickly lead to widespread disruptions. But what makes these breaches so hard to detect and contain? The answer lies in the complexity of modern supply chains and IT ecosystems.
A perfect storm of fragmented ownership, hidden dependencies, and supply chain blind spots has made silent breaches easy to miss — and even harder to stop.
Organizations often struggle with governance when it comes to third-party risk, with responsibility often split between security, procurement, and supply chain teams. The lack of clear ownership means risks frequently slip through the cracks, allowing vulnerabilities to remain unchecked.
Many organizations also underestimate the impact of concentration and cascading risk in their third-party ecosystems. Over-reliance on a single vendor creates a single point of failure that can decimate operations if that vendor is compromised. A breach in one organization can also ripple silently through multiple layers of third, fourth, or even fifth parties before anyone realizes the exposure.
Visibility into third-party cyber risk is another major issue. Most organizations have a rough estimate of how many partners they work with, but the actual number is almost always higher. Without complete visibility into how each vendor manages risk, companies are left guessing about their exposure. When a breach occurs, they don’t know who to contact or how to mitigate the damage, leading to significant operational and financial consequences.
Most organizations aren’t prepared for silent breaches, catching them flat-footed when one occurs. That leads to a range of serious consequences, including:
Regulations like GDPR, HIPAA, and the Digital Operational Resilience Act (DORA) are attempting to close the gaps that enable silent breaches by enforcing stricter risk management standards. DORA, in particular — which recently came into effect in the EU — explicitly recognizes third-party risk and places increased focus on critical service providers, expanding reporting obligations and resilience testing requirements to these providers.
Silent breaches aren’t going away, and compliance alone won’t protect organizations from third-party risks. Organizations must take proactive steps to strengthen resilience across their entire third-party ecosystem. Here’s how cybersecurity leaders can take action in 2025:
Lets look at each strategy in greater detail.
Before organizations can tackle third-party risk, they must first establish a structured governance framework. This framework should identify who assesses vendor risks, how security expectations are enforced, and what escalation procedures exist when risks emerge.
This step also requires bringing all key stakeholders to the table to ensure a shared understanding of third-party dependencies. Security leaders must frame risk in business terms, making it clear how a vendor’s cybersecurity weaknesses could disrupt operations. Black Kite’s FocusTags™ and Cyber Risk Quantification provide CISOs with the data they need to drive these conversations, helping quantify vendor risk and prioritize mitigation efforts based on real business impact.
Rather than seeing vendors as adversaries, organizations need to focus on creating strong, collaborative relationships. Organizations must move beyond static security questionnaires and engage in ongoing conversations about risk.
Cybersecurity expectations should be explicitly written into vendor contracts. Instead of generic security demands, organizations should provide vendors with precise data on vulnerabilities and step-by-step remediation guidance. Tools like Black Kite Bridge™ help streamline this process by eliminating communication gaps and enabling organizations to easily share actionable intelligence with vendors.
Continuous monitoring provides the real-time intelligence needed to track vendor security posture and respond before threats escalate. Instead of starting from scratch when a new zero-day vulnerability is announced, you can instantly pinpoint which third parties are exposed and act accordingly.
Black Kite’s FocusTags™ help organizations continuously assess risks, while the Supply Chain Module maps dependencies and monitors vendor ecosystems for potential disruptions and single points of failure.
Stopping silent breaches requires a shift from reactive responses to proactive vulnerability management. Black Kite’s Ransomware Susceptibility Index® (RSI™) is a powerful tool to uncover the likelihood of an attack across third-party vendors, helping develop effective remediation steps ahead of time.
Updating your approach to compliance gap analysis can also reduce the administrative load on both sides. Traditional security assessments overwhelm vendors with long, generic questionnaires that often fail to capture real risks. Black Kite’s AI-powered compliance gap analysis replaces these questionnaires, analyzing vendor security frameworks to pinpoint compliance gaps. Instead of answering hundreds of irrelevant questions, vendors receive a tailored set of questions, ensuring they focus on the most pressing security improvements.
Real resilience comes from collaboration — both internal and external. Compliance mandates like DORA and the NIST Cybersecurity Framework provide a solid starting point, but security leaders must go beyond regulatory checkboxes.
Strengthening internal alignment is the first step, ensuring security, risk, and procurement teams work together. From there, expanding collaboration externally is critical to staying ahead of evolving threats. Industry-specific groups like ISACs (Information Sharing and Analysis Centers) foster intelligence-sharing and collective defense, while cross-industry collaboration initiatives like ISSA and CISOs Connect™ help security leaders anticipate emerging risks.
Vendors must also be part of this equation. Encouraging them to participate in collaborative initiatives and using tools like Black Kite Bridge™ can help engage vendors in the threat intelligence process, strengthening security partnerships.
Silent breaches might have dominated 2024’s cyber threat landscape, but they don’t have to define the future. The hard lessons from these attacks offer a blueprint for resilience. By taking a proactive approach — strengthening governance, improving vendor collaboration, and continuously monitoring for hidden risks — organizations can turn the tide against silent breaches in 2025.
Read the 2025 Third-Party Breach Report for more insights to avoid the next silent breach.
Dig into our full 2025 Third Party Breach Report: The Silent Breach: How Third Parties Became the Biggest Cyber Threat in 2024 – accessible instantly, no download required.
The post The Silent Breach: Why Third Parties Are Cybersecurity’s Greatest Hidden Threat appeared first on Black Kite.
Byline: Ekrem Selcuk Celik, Cybersecurity Researcher at Black Kite
Welcome to the January 2025 ransomware update, where we highlight the latest trends, threat actors, and developments in the ransomware ecosystem to keep CISOs and third-party risk managers informed and prepared.
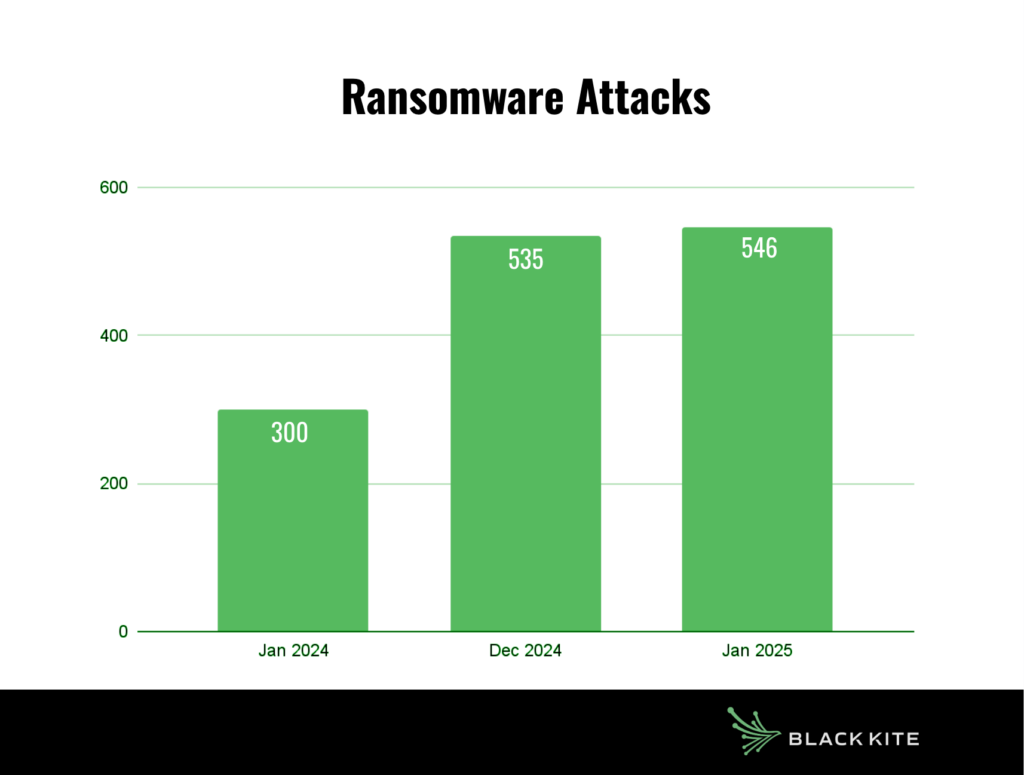
The Black Kite Research & Intelligence Team (BRITE) tracked 546 ransomware incidents in January 2025, marking a sharp increase compared to January 2024, which saw approximately 300 cases. This significant rise indicates that ransomware activity is escalating at an alarming pace. Among these incidents, 274 were recorded in the United States, 32 in Canada, 23 in the United Kingdom, and 18 in France.
Manufacturing was the most targeted sector, followed by technical services. Closing out December with 535 cases, ransomware groups have historically shown a tendency to slow down at the beginning of the year. However, this year is proving to be an exception.
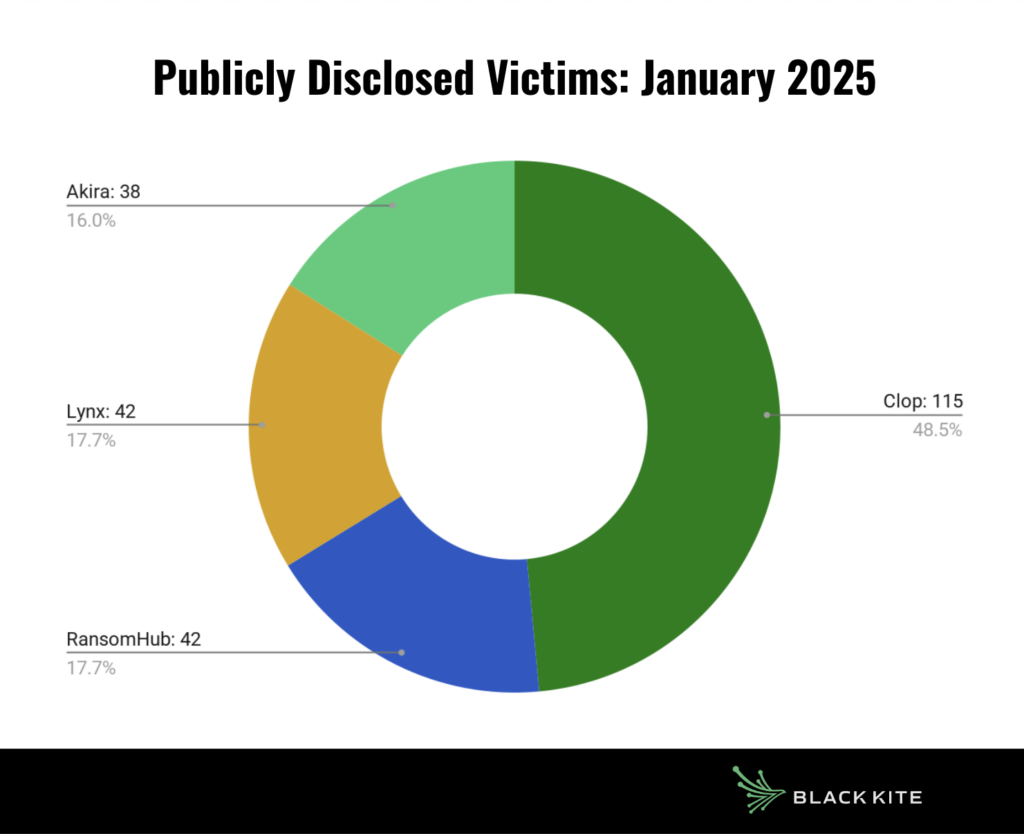
The Clop ransomware group took the lead in January 2025 by a significant margin with 115 publicly disclosed victims. As usual, RansomHub remained among the top-ranking groups with 42 victims. One of the most notable groups this month was Lynx, which saw a major surge with 42 victims in January. They were followed by the Akira group, which recorded 38 victims.
Nearly all of the 115 Clop attacks were linked to the CLEO vulnerability, continuing the momentum from Clop’s December disclosures. Initially, only 50 victims were expected, but as the group continues to release names in alphabetical order, the final number could reach 500.
Among these 115 victims, the United States was the most affected, with 79 cases, followed by Canada with 12 and the Netherlands with 4.
In terms of industry impact among these attacks, the manufacturing sector suffered the highest number of attacks, with 34 victims. It was followed by the transportation sector with 18 victims, the information technology sector with 17, and the technical services sector with 14.
Two years ago, during the MoveIT disclosures, Clop was at the center of global media attention. Now, despite its high ransomware activity, the group seems to be struggling to capture the same level of interest. They kept postponing victim disclosures, which was unusual for them, and then starting sharing victims in a different way to seek attention. Whether this signals Clop’s waning influence or a shift in public perception remains to be seen, but one thing is certain: the group appears increasingly frustrated by the lack of attention.
FunkSec continued its aggressive expansion in January, making headlines with its unconventional tactics:
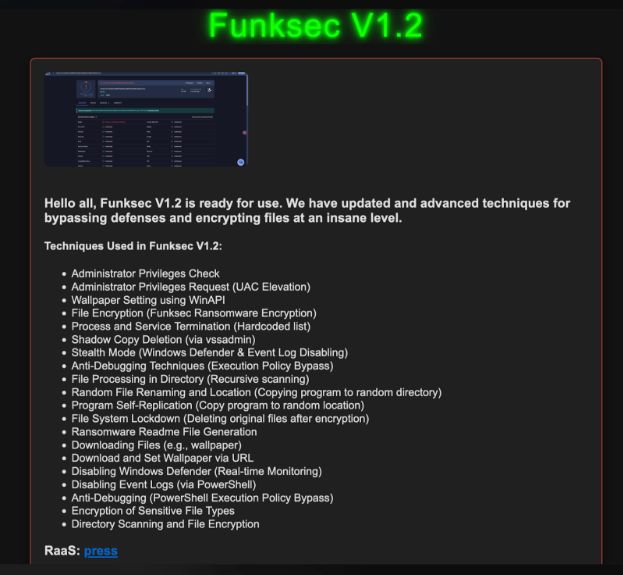
Key takeaways from their recent interview:
FunkSec’s erratic yet calculated moves make them one of the most unpredictable actors in the ransomware ecosystem. Their expansion beyond traditional ransomware operations suggests a broader ambition that could redefine the threat landscape.
A new leak site emerged in January claiming to be affiliated with Babuk, publishing 60 alleged victims. While this sparked speculation that the notorious ransomware group had returned, our analysis revealed that most of the disclosed victims had already been published by FunkSec, RansomHub, and LockBit.
Shortly after the site gained traction, access was restricted, leaving its authenticity in question. Whether this marks the actual return of Babuk or merely an opportunistic attempt to capitalize on the name remains unclear.
Ransomware groups continue to surface at an increasing rate, and the rise of Ransomware-as-a-Service (RaaS) is undoubtedly fueling this trend. However, despite this growth, these groups seem to do little more than mimic each other. Many simply replicate existing leak sites, making it increasingly difficult to track them as they blur into one another.
In previous years, such copycat behavior was less common, but now it’s becoming the norm. This shift strongly suggests that experienced cybercriminals are being replaced by younger, less-skilled actors. As a result, while the number of ransomware groups grows, innovation within the ecosystem seems to be stagnating.
While ransomware attacks surged in 2024, total ransom payments dropped by 35%, amounting to $813.55 million. Companies are increasingly adopting robust cybersecurity measures, improving backup strategies, and benefiting from law enforcement crackdowns on cybercriminals.
Notably, the international operation “Operation Cronos” disrupted LockBit’s infrastructure, demonstrating the growing impact of coordinated cybercrime enforcement. However, despite these advancements, ransomware groups are evolving their tactics, becoming more aggressive in their extortion methods.
In response, the UK government is considering stricter regulations, including:
Authorities believe these measures will curb ransomware groups’ financial streams and act as a deterrent. If enacted, these regulations could reshape how organizations respond to ransomware threats.
January 2025 set a record-breaking pace for ransomware incidents.
For cybersecurity teams, 2025 is already shaping up to be one of the most challenging years yet. Black Kite’s Ransomware Susceptibility Index® (RSITM) offers a proactive approach by assessing the likelihood of a ransomware attack throughout the third-party ecosystem. By leveraging RSI, risk managers can identify high-risk vendors before an attack strikes, prioritize remediation efforts, and ultimately safeguard their organizations against the escalating threat.
Stay tuned for more monthly Ransomware Reviews on our blog and LinkedIn Newsletter.
Dig into our full 2025 Third Party Breach Report: The Silent Breach: How Third Parties Became the Biggest Cyber Threat in 2024 – accessible instantly, no download required.
The post Ransomware Review January 2025: Clop’s CLEO Exploit Fuels a Record Month appeared first on Black Kite.
Written by: Ferdi Gül
In this week’s Focus Friday, we examine high-impact vulnerabilities affecting Palo Alto Networks PAN-OS, Ivanti Connect Secure, Zimbra Collaboration, and Cacti, all of which pose significant third-party risk concerns. These vulnerabilities range from remote code execution (RCE) flaws to SQL injection attacks that could lead to data breaches, system takeovers, and supply chain risks.
Organizations relying on network security appliances, email collaboration tools, and monitoring frameworks must take proactive measures to assess their exposure and secure their vendor ecosystem against these threats. In this blog, we provide an in-depth Third-Party Risk Management (TPRM) perspective, detailing how these vulnerabilities could impact vendor security postures and what questions security teams should ask to mitigate risks.
Additionally, we highlight how Black Kite’s FocusTags™ provide real-time insights into vendor exposure, helping organizations prioritize remediation efforts and streamline their risk management processes.

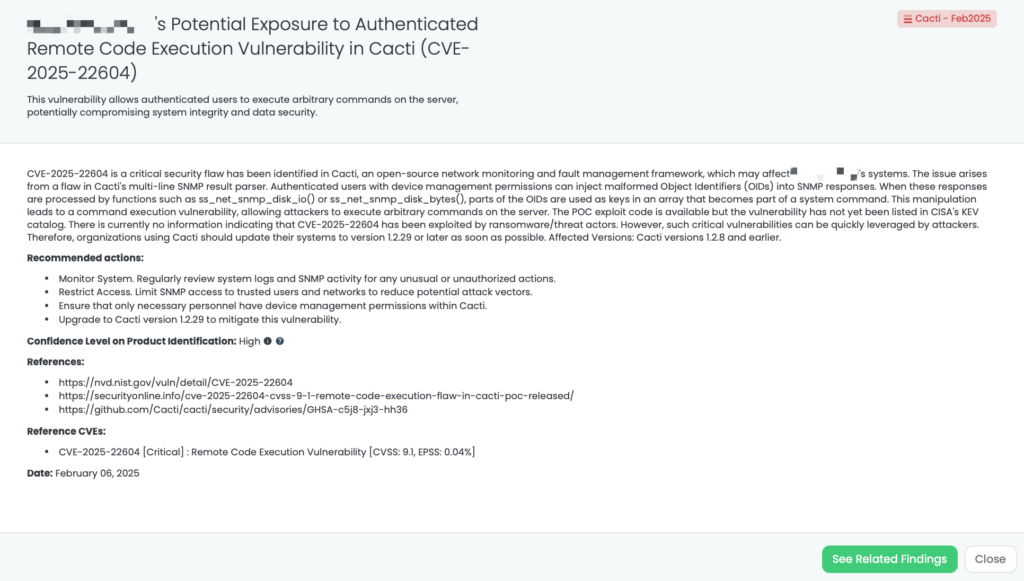
Two high-severity vulnerabilities have been identified in Palo Alto Networks PAN-OS, affecting network security devices:
Both vulnerabilities were published on February 12, 2025. One proof-of-concept exploit is available on github.com. There is no evidence of active exploitation or inclusion in CISA’s KEV catalog at this time. However, PAN-OS vulnerabilities have been targeted in the past, making proactive mitigation crucial.
Third-party risk management (TPRM) professionals should be concerned due to the critical role of PAN-OS in enterprise cybersecurity.
For vendors relying on PAN-OS for perimeter security, exploitation of these vulnerabilities could lead to network-wide security breaches, data exposure, and compromised firewall configurations.
To assess vendor exposure, TPRM professionals should ask:
To mitigate the risk associated with these vulnerabilities, vendors should:
✔ Upgrade PAN-OS to patched versions:
✔ Update OpenConfig plugin to version 2.1.2 or later (if enabled).
✔ Restrict management interface access to trusted internal IPs only.
✔ Disable the OpenConfig plugin if not in use to reduce the attack surface.
✔ Monitor system logs for unusual access or command execution activity.
✔ Apply Palo Alto Networks’ Threat Prevention rules to block potential exploits (Threat IDs 510000, 510001).
Black Kite has tagged this issue as “PAN-OS – Feb2025” with a VERY HIGH confidence level.
The FocusTag™ was published on February 13, 2025, allowing TPRM teams to take proactive measures before potential exploitation.
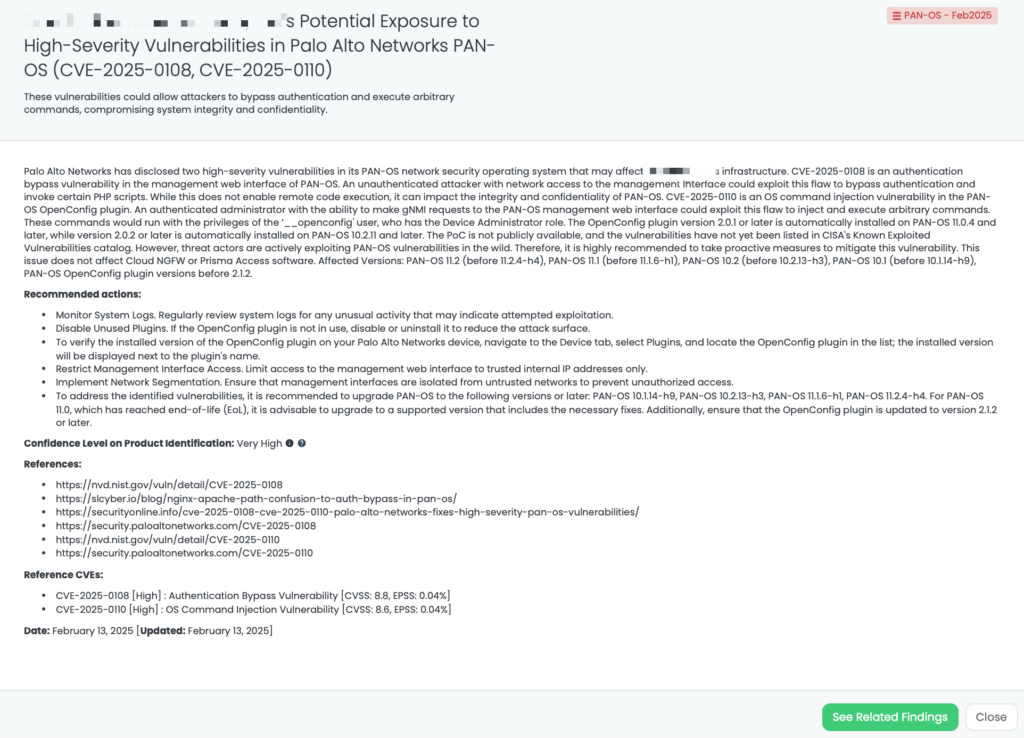
Multiple critical vulnerabilities have been identified in Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) products:
These vulnerabilities were publicly disclosed on February 11, 2025. As of now, there is no evidence of active exploitation in the wild, and they have not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog. Other vulnerabilities to be mindful of include CVE-2024-12058 (arbitrary file read), CVE-2024-13842 (sensitive data exposure), and CVE-2024-13843 (cleartext storage of sensitive information), which, despite their lower CVSS scores, should still be carefully considered.
Third-Party Risk Management (TPRM) professionals should be concerned due to the following reasons:
To assess vendor exposure, TPRM professionals should inquire:
To mitigate the risks associated with these vulnerabilities, vendors should:
✔ Update to Patched Versions:
✔ Restrict Administrative Privileges:
✔ Implement Multi-Factor Authentication (MFA):
✔ Monitor System Logs:
✔ Apply Security Best Practices:
Black Kite has tagged these vulnerabilities under “Ivanti Connect Secure – Feb2025” with a HIGH confidence level.
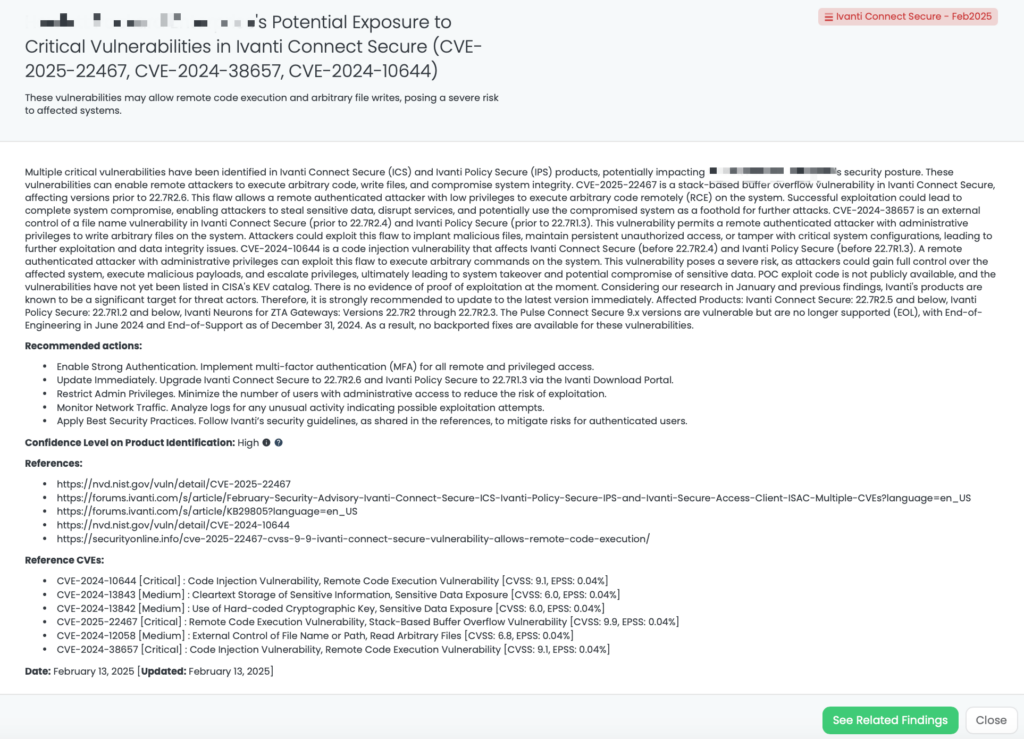
Zimbra Collaboration (formerly known as Zimbra Collaboration Suite or ZCS) is an open-source and commercial groupware email platform. It includes features such as email, calendaring, contacts, task management, instant messaging, and file sharing, designed for enterprises, government institutions, and service providers.
CVE-2025-25064 is a critical SQL injection vulnerability affecting Zimbra Collaboration versions 10.0.x prior to 10.0.12 and 10.1.x prior to 10.1.4. This flaw arises from insufficient sanitization of user-supplied parameters in the ZimbraSync Service SOAP endpoint. Authenticated attackers can exploit this vulnerability by manipulating specific request parameters to inject arbitrary SQL queries, potentially allowing unauthorized retrieval of email metadata and other sensitive information. The vulnerability has a CVSS score of 9.8, indicating its critical severity, and an EPSS score of 0.05%. It was publicly disclosed on February 9, 2025. As of now, there is no evidence of active exploitation in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities catalog.
Third-Party Risk Management (TPRM) professionals should be concerned about CVE-2025-25064 due to its potential impact on email security. Zimbra Collaboration is widely used by organizations for email and collaboration services. Exploitation of this vulnerability could allow attackers to access sensitive email metadata, leading to unauthorized disclosure of confidential information. If a vendor utilizes vulnerable Zimbra Collaboration products, their compromised systems could serve as entry points for attackers, resulting in data breaches and disruptions that may affect connected organizations.
To assess and mitigate risks associated with this vulnerability, TPRM professionals should inquire:
Vendors using affected Zimbra Collaboration products should:
Black Kite has proactively addressed this issue by publishing the “Zimbra – Feb2025” FocusTag™ on February 11, 2025. This tag enables TPRM professionals to identify vendors potentially affected by CVE-2025-25064. By providing detailed asset information, including IP addresses and subdomains associated with the compromised devices, Black Kite empowers organizations to assess and mitigate risks efficiently. This actionable intelligence allows for targeted inquiries and remediation efforts, ensuring a robust third-party risk management strategy.
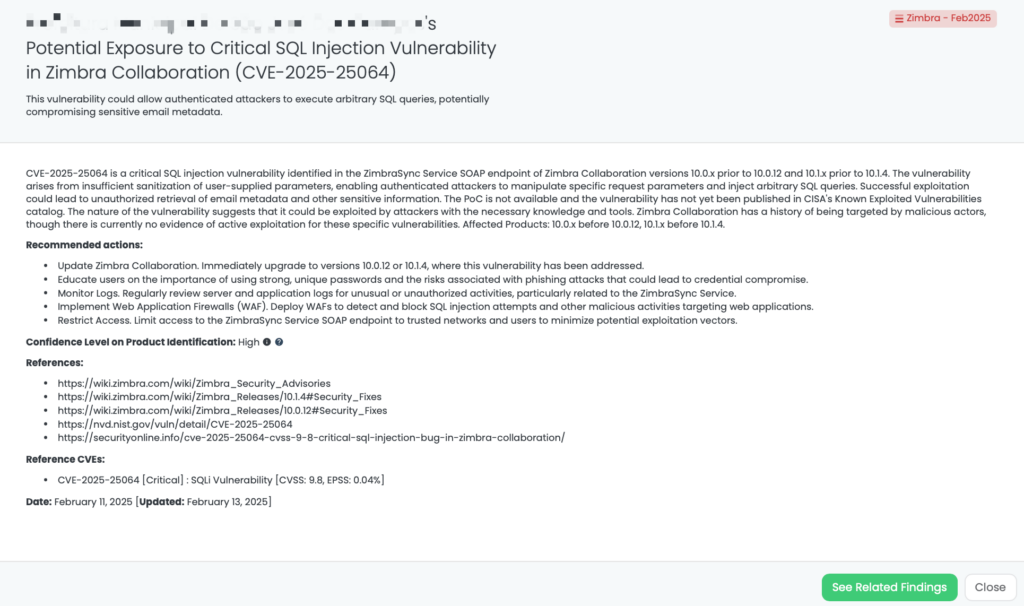
Cacti is an open-source network monitoring and graphing tool designed to collect, store, and visualize performance data for IT infrastructure. It is widely used by network administrators and IT professionals to monitor network devices, servers, and applications in real time.
CVE-2025-22604 is a critical security flaw in Cacti, an open-source network monitoring and fault management framework. This vulnerability allows authenticated users with device management permissions to execute arbitrary commands on the server by injecting malformed Object Identifiers (OIDs) into SNMP responses. When processed by functions like ss_net_snmp_disk_io() or ss_net_snmp_disk_bytes(), parts of these OIDs are used as keys in an array that becomes part of a system command, leading to remote code execution (RCE). The vulnerability has a CVSS score of 9.1. It was publicly disclosed on January 26, 2025. There is no evidence of proof of exploitation at the moment.
Third-Party Risk Management (TPRM) professionals should be concerned about CVE-2025-22604 because Cacti is widely used by organizations to monitor network performance and availability. A successful exploit of this vulnerability could allow attackers to execute arbitrary commands on the server, potentially compromising system integrity and data security. This could lead to unauthorized access to sensitive information, disruption of network monitoring capabilities, and further exploitation within the organization’s network. Given the critical nature of this vulnerability and the availability of proof-of-concept exploit code, it is imperative for organizations to assess their exposure and ensure that their vendors have addressed this issue.
To assess the risk associated with this vulnerability, TPRM professionals should consider asking vendors the following questions:
Vendors should take the following actions to remediate the risk associated with CVE-2025-22604:
Black Kite has published a FocusTag™ titled “Cacti – Feb2025” to help organizations identify potential exposure to CVE-2025-22604. TPRM professionals can utilize this tag to assess their vendors’ risk related to this vulnerability. By leveraging Black Kite’s platform, professionals can identify vendors using vulnerable versions of Cacti and take proactive steps to mitigate potential risks. This includes obtaining asset information such as IP addresses and subdomains associated with the vendors’ systems, which is crucial for effective risk assessment and management.
With high-profile vulnerabilities such as PAN-OS authentication bypass (CVE-2025-0108), Ivanti Connect Secure RCE (CVE-2025-22467), Zimbra SQL injection (CVE-2025-25064), and Cacti remote code execution (CVE-2025-22604), organizations must rapidly assess third-party security risks to prevent cascading impacts. Black Kite’s FocusTags™ enable security teams to efficiently identify, analyze, and mitigate these threats by offering:
✅ Real-Time Risk Identification – Instant visibility into which vendors are affected by the latest vulnerabilities, allowing organizations to take immediate action.
✅ Risk Prioritization – Insights into vendor importance and vulnerability severity, helping security teams allocate resources effectively.
✅ Informed Vendor Engagement – Targeted discussions with vendors about their security measures and remediation strategies for identified vulnerabilities.
✅ Comprehensive Security Posture Enhancement – A holistic view of third-party risks, enabling organizations to make data-driven security decisions.
By leveraging Black Kite’s FocusTags™, organizations can stay ahead of evolving cyber threats, ensuring proactive risk mitigation in their third-party ecosystems. These tags provide critical intelligence, transforming complex vulnerability data into actionable insights for better vendor security management.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
https://nvd.nist.gov/vuln/detail/CVE-2025-0108
https://nvd.nist.gov/vuln/detail/CVE-2025-0110
https://security.paloaltonetworks.com/CVE-2025-0108
https://security.paloaltonetworks.com/CVE-2025-0110
https://slcyber.io/blog/nginx-apache-path-confusion-to-auth-bypass-in-pan-os
https://forums.ivanti.com/s/article/KB29805?language=en_US
https://nvd.nist.gov/vuln/detail/CVE-2025-22467
https://nvd.nist.gov/vuln/detail/CVE-2024-10644
https://wiki.zimbra.com/wiki/Zimbra_Releases/10.0.12#Security_Fixes
https://wiki.zimbra.com/wiki/Zimbra_Releases/10.1.4#Security_Fixes
https://wiki.zimbra.com/wiki/Zimbra_Security_Advisories
https://nvd.nist.gov/vuln/detail/CVE-2025-25064
https://nvd.nist.gov/vuln/detail/CVE-2025-22604
https://github.com/Cacti/cacti/security/advisories/GHSA-c5j8-jxj3-hh36
https://securityonline.info/cve-2025-22604-cvss-9-1-remote-code-execution-flaw-in-cacti-poc-released
The post Focus Friday: Addressing Third-Party Risks in PAN-OS, Ivanti Connect Secure, Zimbra, and Cacti Vulnerabilities appeared first on Black Kite.



