Focus Friday: TPRM Insights On PAN-OS, PostgreSQL, and Apache Airflow Vulnerabilities
Written by: Ferdi Gül
This week’s Focus Friday blog delves into critical vulnerabilities affecting widely used systems: PAN-OS, Apache Airflow, and PostgreSQL. These vulnerabilities, ranging from authentication bypass and privilege escalation to sensitive data exposure and arbitrary code execution, highlight the evolving threat landscape faced by organizations worldwide. From a Third-Party Risk Management (TPRM) perspective, understanding these vulnerabilities and their implications is vital for maintaining a robust security posture across the supply chain. In this blog, we explore the technical details, potential impacts, and how Black Kite’s FocusTags™ empower organizations to respond effectively to these threats.
CVE-2024-0012 and CVE-2024-9474: PAN-OS Authentication Bypass and Privilege Escalation Vulnerabilities
What Are the PAN-OS Authentication Bypass and Privilege Escalation Vulnerabilities?
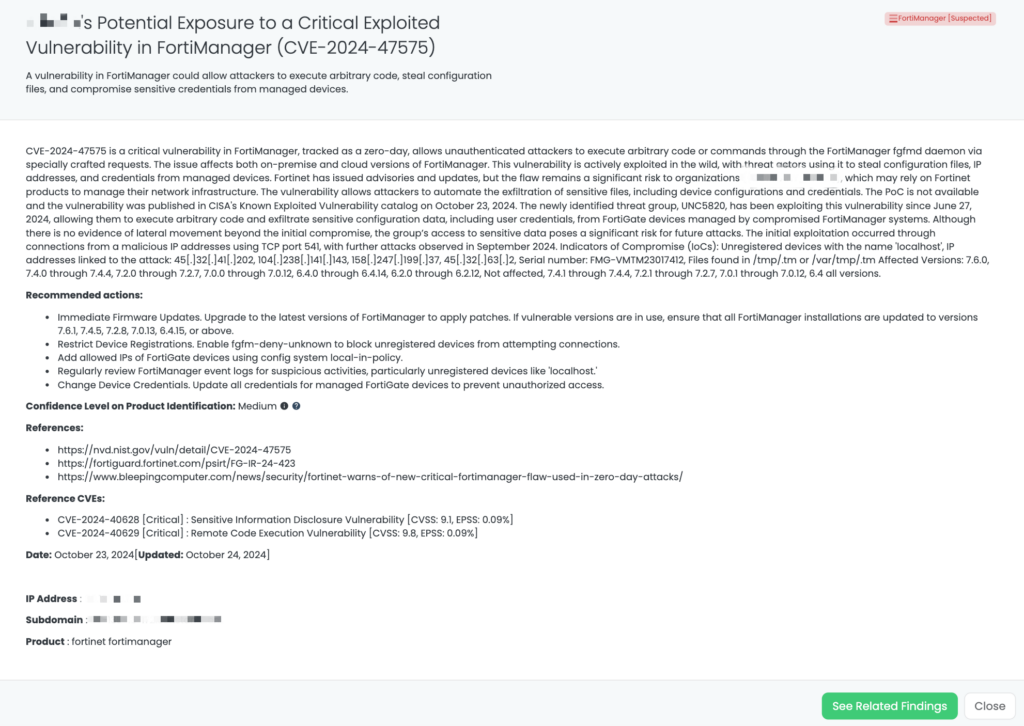
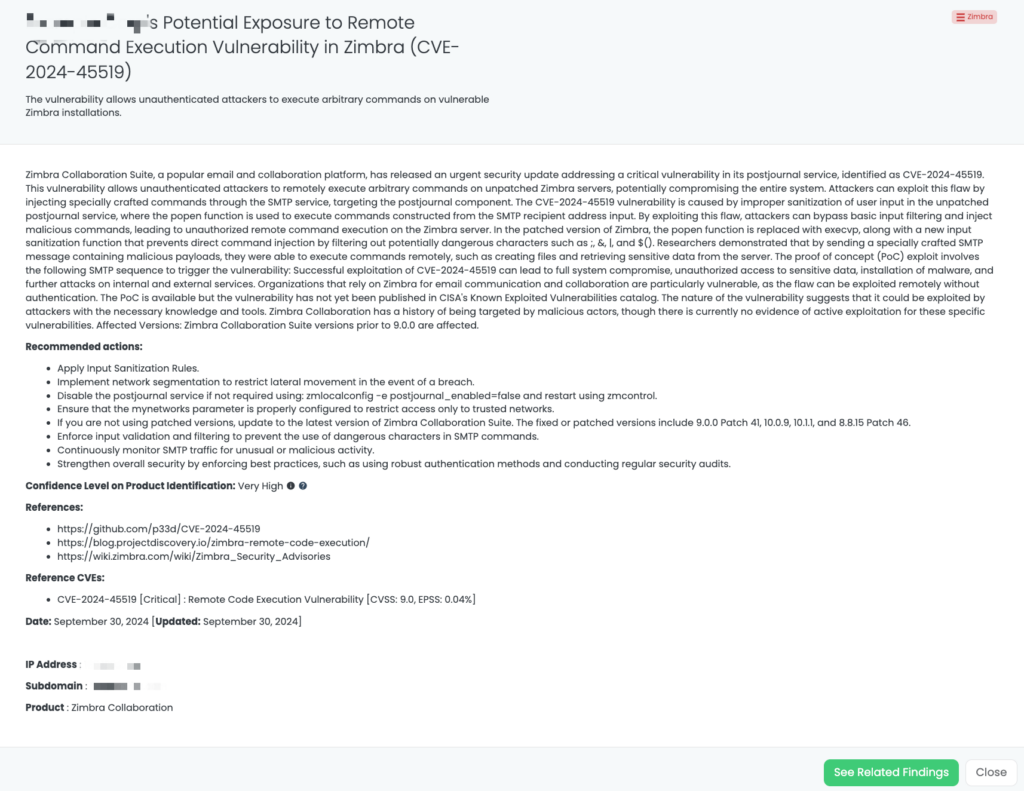
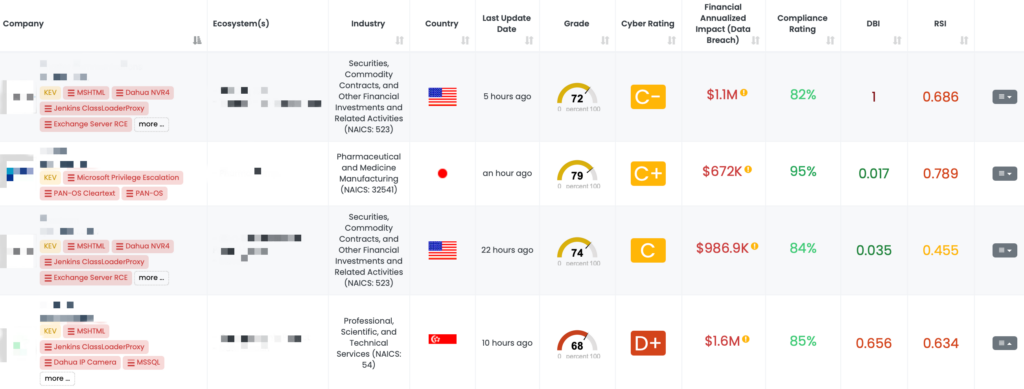
CVE-2024-0012 is a critical authentication bypass vulnerability in PAN-OS, published on November 18, 2024. This flaw allows unauthenticated attackers with network access to the management web interface to gain administrative privileges. Exploitation enables tampering with configurations, executing administrative actions, and leveraging other vulnerabilities such as CVE-2024-9474. The vulnerability has a CVSS score of 9.3 and is actively exploited.
CVE-2024-9474 is a medium-severity privilege escalation vulnerability in PAN-OS, also published on November 18, 2024. This flaw enables attackers with administrative access to escalate their privileges to root level, leading to complete system compromise. It has a CVSS score of 6.9 and is actively exploited in the wild.
Both vulnerabilities have been listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog on November 18, 2024.
Why Should TPRM Professionals Be Concerned About CVE-2024-0012 and CVE-2024-9474?
PAN-OS is a critical component of enterprise network security. Exploitation of these vulnerabilities poses severe risks, including:
- Compromised administrative control: Attackers can bypass authentication and escalate privileges to root level, allowing full control over firewalls and related systems.
- Data breaches: Sensitive data and configurations may be accessed or modified.
- Lateral movement: Attackers can use compromised systems to launch further attacks, threatening the entire network.
For TPRM professionals, vendors utilizing PAN-OS could become entry points for malicious activity, necessitating immediate evaluation and action.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-0012 and CVE-2024-9474?
To assess the vendor’s mitigation efforts for these vulnerabilities, ask:
- Have you upgraded all PAN-OS devices to patched versions (10.2.12-h2, 11.0.6-h1, 11.1.5-h1, or 11.2.4-h1 or later)?
- Have you restricted management interface access to trusted internal IP addresses and avoided exposing it to the internet as a precaution against the exploitation of CVE-2024-0012 and CVE-2024-9474?
- Are you using Palo Alto Networks Threat Prevention capabilities to block attack signatures for these vulnerabilities including Threat IDs 95746, 95747, 95752, 95753, 95759, and 95763?
- Can you confirm if you have implemented the recommended actions such as continuously monitoring network traffic for unusual activity and securing management access with a jump box or other hardened mechanisms to prevent exploitation of CVE-2024-0012 and CVE-2024-9474?
Remediation Recommendations for Vendors Affected by CVE-2024-0012 and CVE-2024-9474
Vendors should take the following actions to mitigate these vulnerabilities:
- Upgrade PAN-OS: Install versions 10.2.12-h2, 11.0.6-h1, 11.1.5-h1, or 11.2.4-h1 or later.
- Restrict Access: Limit management web interface access to trusted internal IPs and avoid exposing it to the internet.
- Enable Threat Prevention: Use Palo Alto Networks Threat IDs (e.g., 95746, 95747) to block known attack vectors.
- Monitor Activity: Regularly review logs for unusual administrative actions or traffic patterns.
- Implement Role-Based Controls: Restrict root-level access to essential administrative users only.
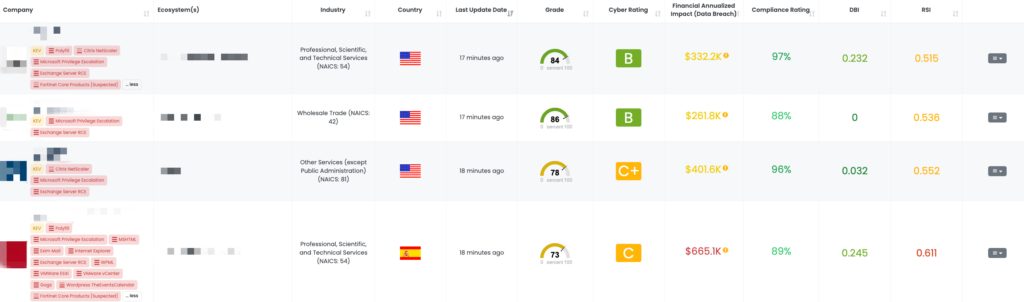
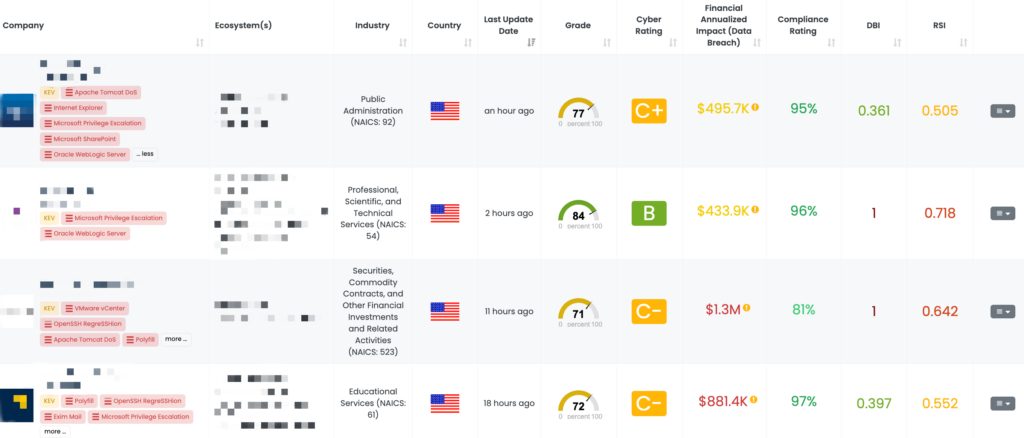
How Can TPRM Professionals Leverage Black Kite for CVE-2024-0012 and CVE-2024-9474?
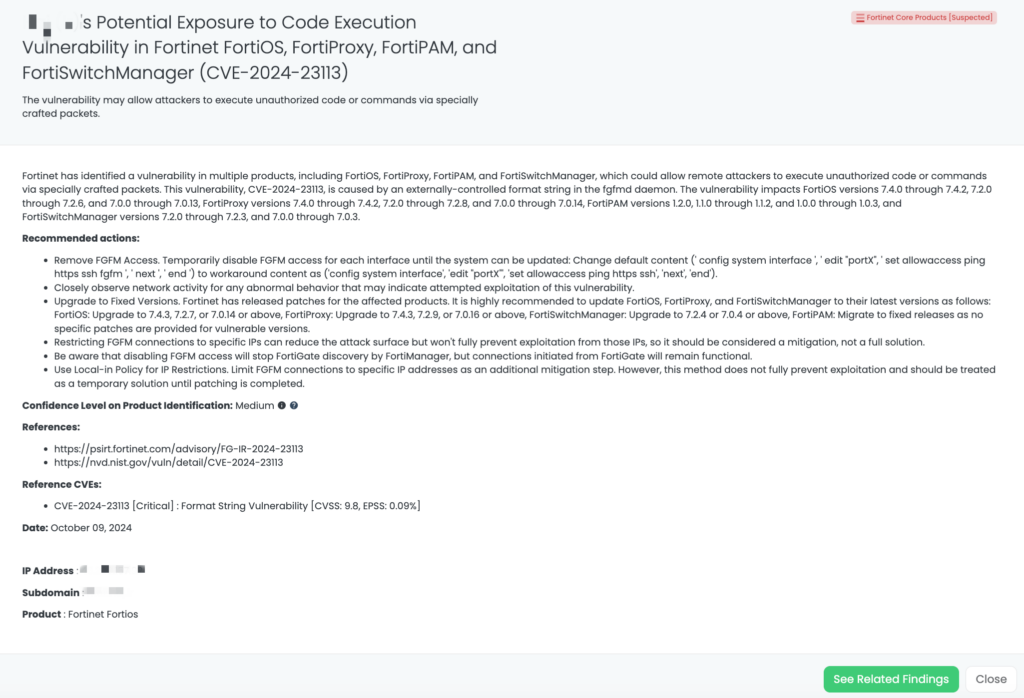
Black Kite’s FocusTag™ for these vulnerabilities, published on November 19, 2024 (with updates on November 20, 2024), provides TPRM professionals with critical insights, including:
- Identification of affected vendors: Black Kite helps pinpoint vendors with potential exposure to these vulnerabilities.
- Detailed asset information: This includes IP addresses and subdomains associated with the vulnerabilities.
- Streamlined prioritization: Professionals can focus their efforts on vendors with the highest risk exposure, ensuring efficient remediation.
CVE-2024-10979: PostgreSQL Arbitrary Code Execution Vulnerability
What is the PostgreSQL Arbitrary Code Execution Vulnerability?
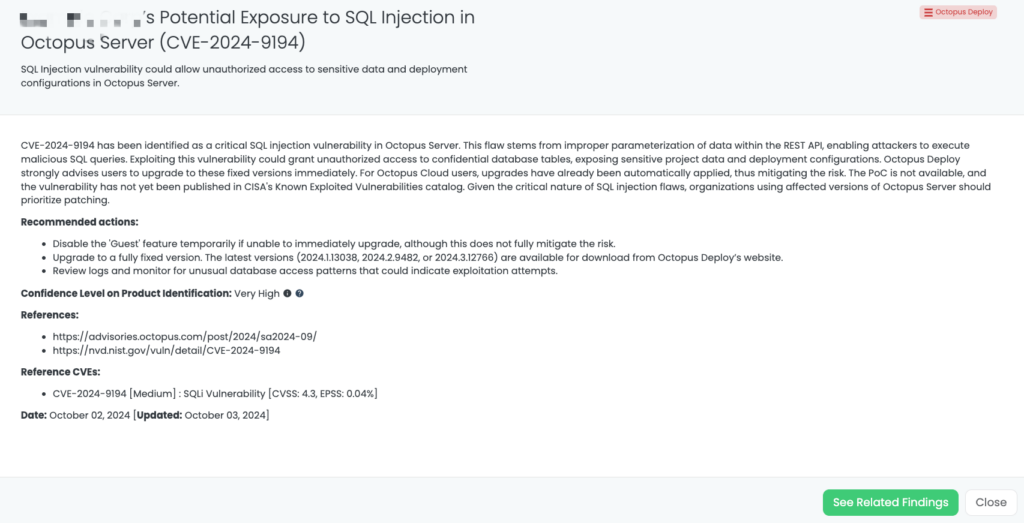
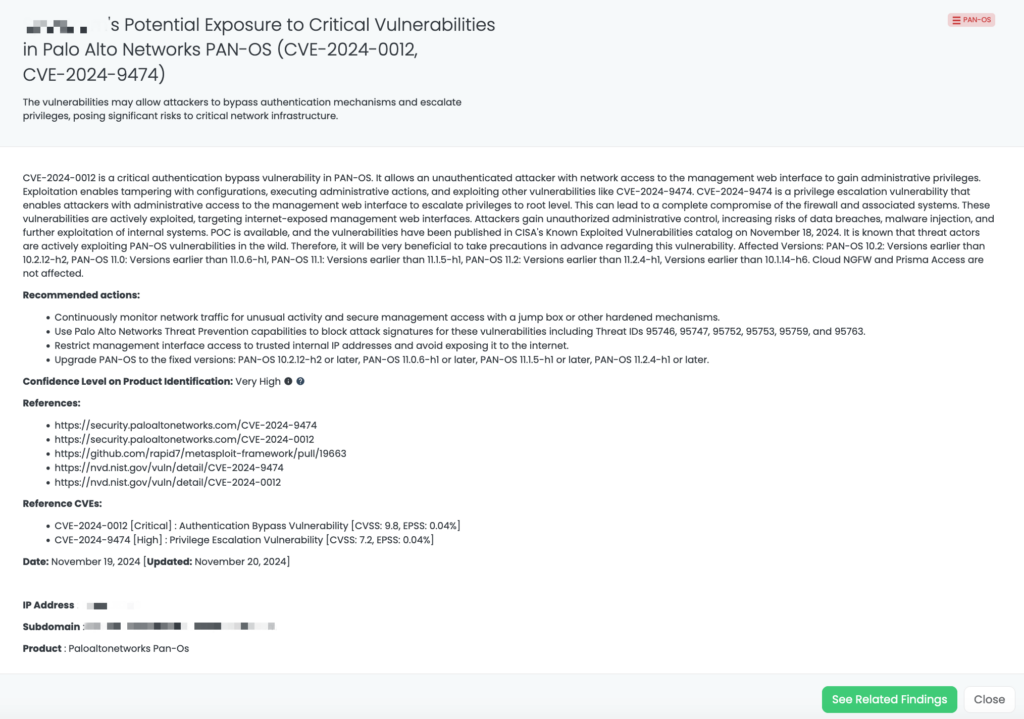
CVE-2024-10979 is a high-severity vulnerability in PostgreSQL’s PL/Perl procedural language, identified on November 14, 2024. This flaw allows unprivileged database users to manipulate environment variables, such as PATH, potentially leading to arbitrary code execution. The vulnerability has a CVSS score of 8.8. As of now, there is no evidence of active exploitation in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why Should TPRM Professionals Be Concerned About CVE-2024-10979?
PostgreSQL is a widely used relational database management system across various industries. A vulnerability that permits arbitrary code execution poses significant risks, including unauthorized access to sensitive data, system compromise, and potential lateral movement within an organization’s network. For Third-Party Risk Management (TPRM) professionals, this vulnerability is particularly concerning when vendors utilize PostgreSQL in their operations, as it could lead to compromised data integrity and confidentiality.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-10979?
To assess the impact of this vulnerability on your vendors, consider asking the following questions:
- Have you identified any instances where unprivileged users have manipulated environment variables in your PostgreSQL deployments?
- What measures have you implemented to prevent unauthorized access to environment variables within your PostgreSQL databases?
- Have you applied the necessary patches or updates to address CVE-2024-10979 in your PostgreSQL installations?
- What steps have you taken to monitor and detect potential exploitation attempts related to this vulnerability?
Remediation Recommendations for Vendors Affected by CVE-2024-10979
Vendors should take the following actions to mitigate the risks associated with this vulnerability:
- Upgrade PostgreSQL: Update to the latest fixed versions: 17.1, 16.5, 15.9, 14.14, 13.17, or 12.21.
- Restrict Environment Variable Access: Limit unprivileged users’ ability to interact with environment variables in the database.
- Implement Strong Access Controls: Enforce strict privilege management policies to minimize risks from unauthorized access.
- Monitor for Exploitation Indicators: Review logs and monitor system activity for unusual database queries or environment variable changes.
How Can TPRM Professionals Leverage Black Kite for CVE-2024-10979?
Black Kite published the FocusTag™ for CVE-2024-10979 on November 19, 2024. TPRM professionals can utilize this FocusTag to identify vendors potentially affected by this vulnerability. Black Kite’s platform offers detailed insights, including the specific assets (IP addresses and subdomains) associated with the vulnerable versions of PostgreSQL within a vendor’s infrastructure. This information enables organizations to prioritize their risk assessments and remediation efforts effectively. By leveraging Black Kite’s intelligence, TPRM professionals can streamline their processes, reduce the scope of vendor inquiries, and focus on those most at risk, thereby enhancing the overall security posture of their supply chain.
CVE-2024-45784: Apache Airflow Vulnerability Exposes Sensitive Data in Logs
What is the Apache Airflow Vulnerability CVE-2024-45784?
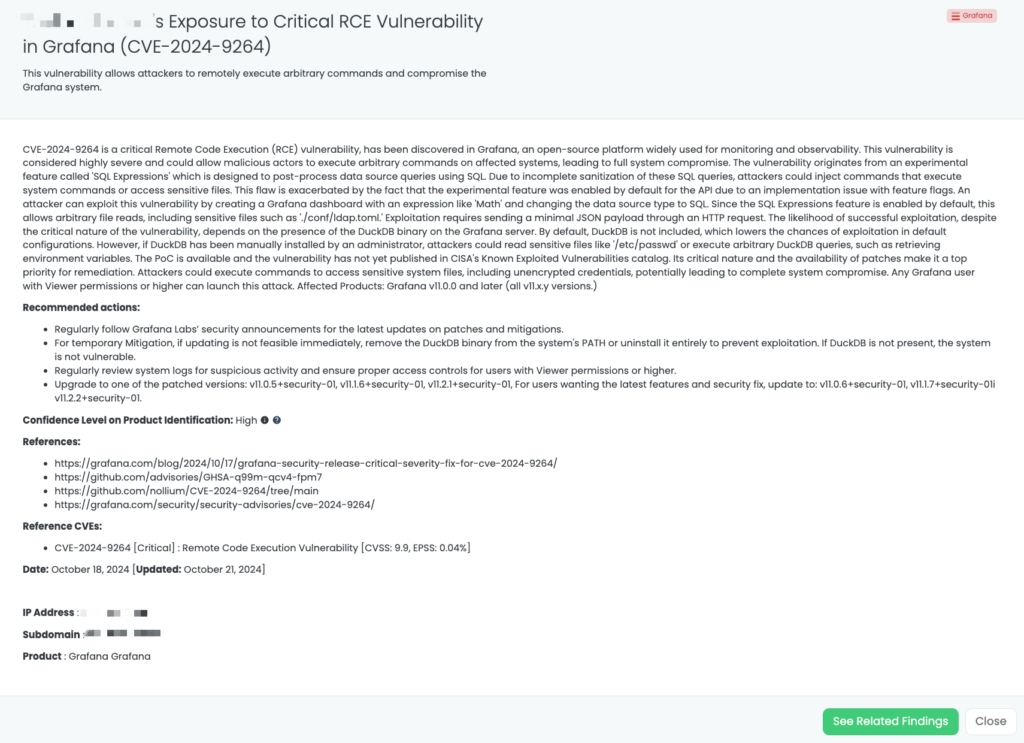
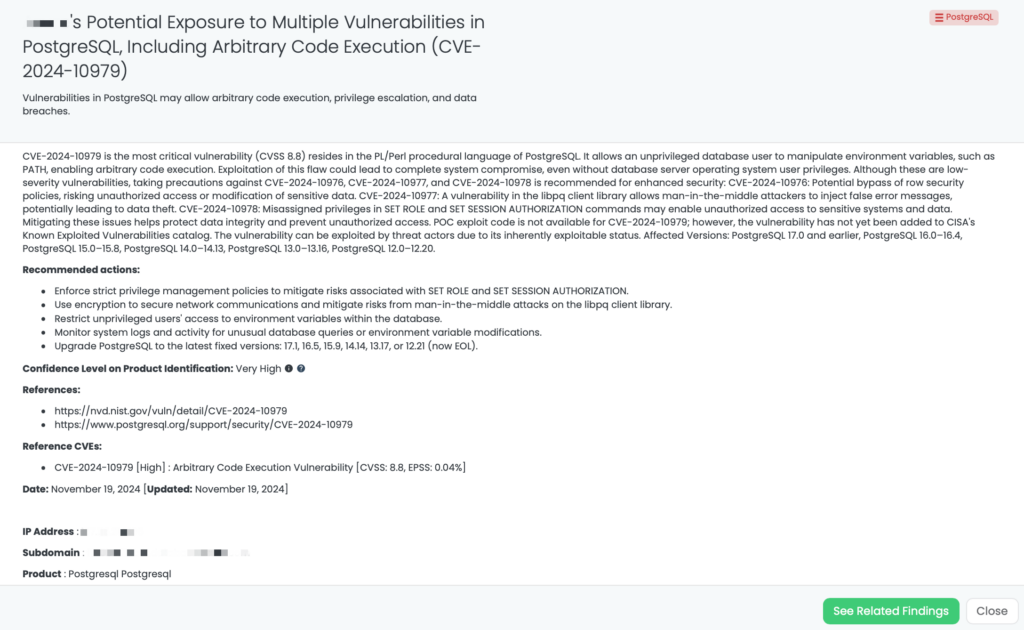
CVE-2024-45784 is a high-severity vulnerability in Apache Airflow versions prior to 2.10.3, with a CVSS score of 7.5. Discovered on November 16, 2024, this flaw arises from the platform’s failure to mask sensitive configuration values in task logs. This oversight allows Directed Acyclic Graph (DAG) authors to inadvertently or deliberately log sensitive information, such as API keys and database credentials. If unauthorized individuals access these logs, they could exploit the exposed data to compromise the security of the Airflow deployment. As of now, there is no evidence of active exploitation in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why Should TPRM Professionals Be Concerned About CVE-2024-45784?
Apache Airflow is widely used for orchestrating complex workflows across various industries. A vulnerability that exposes sensitive configuration data poses significant risks, including unauthorized access to critical systems, data breaches, and potential lateral movement within an organization’s network. For Third-Party Risk Management (TPRM) professionals, this vulnerability is particularly concerning when vendors utilize Airflow in their operations, as it could lead to compromised data integrity and confidentiality.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-45784?
To assess the impact of this vulnerability on your vendors, consider asking the following questions:
- Have you identified any instances where sensitive configuration variables were logged in your Airflow task logs?
- What measures have you implemented to prevent unauthorized access to Airflow logs? Have you implemented strict access controls for logs and enabled role-based access to sensitive Airflow components as recommended to address the vulnerability?
- Have you rotated any credentials or secrets that were potentially exposed due to this vulnerability?
- Have you educated your Directed Acyclic Graph (DAG) authors to avoid logging sensitive information in workflows, and have you rotated any credentials or secrets found in logs as part of your response to the Apache Airflow vulnerability?
Remediation Recommendations for Vendors Affected by CVE-2024-45784
Vendors should take the following actions to mitigate the risks associated with this vulnerability:
- Upgrade Airflow: Update to version 2.10.3 or the latest release to ensure sensitive configuration variables are masked in task logs.
- Audit Logs: Review existing task logs for any exposed secrets and update them as necessary.
- Credential Rotation: Rotate any credentials or secrets identified in logs to prevent unauthorized access.
- Access Controls: Enforce strict access controls for logs and implement role-based access for sensitive Airflow components.
- DAG Author Education: Provide guidelines and training to DAG authors to minimize the logging of sensitive information in workflows.
How Can TPRM Professionals Leverage Black Kite for CVE-2024-45784?
Black Kite published the FocusTag™ for CVE-2024-45784 on November 18, 2024. TPRM professionals can utilize this FocusTag to identify vendors potentially affected by this vulnerability. Black Kite’s platform offers detailed insights, including the specific assets (IP addresses and subdomains) associated with the vulnerable versions of Apache Airflow within a vendor’s infrastructure. This information enables organizations to prioritize their risk assessments and remediation efforts effectively. By leveraging Black Kite’s intelligence, TPRM professionals can streamline their processes, reduce the scope of vendor inquiries, and focus on those most at risk, thereby enhancing the overall security posture of their supply chain.
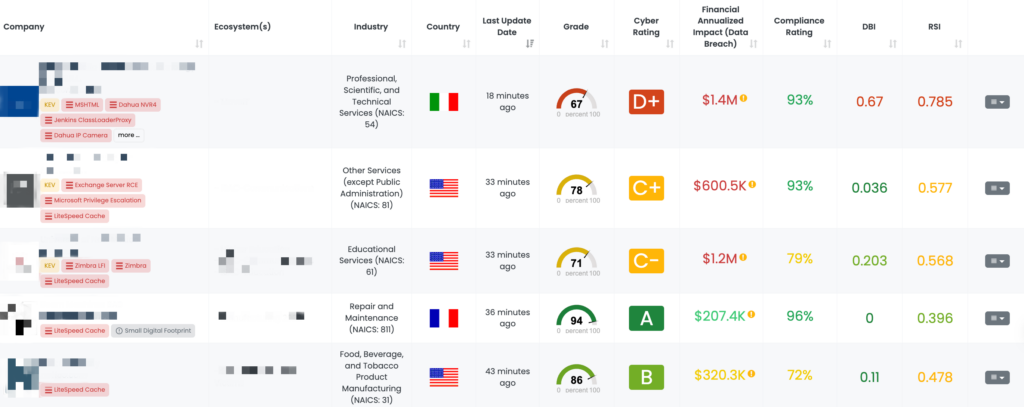
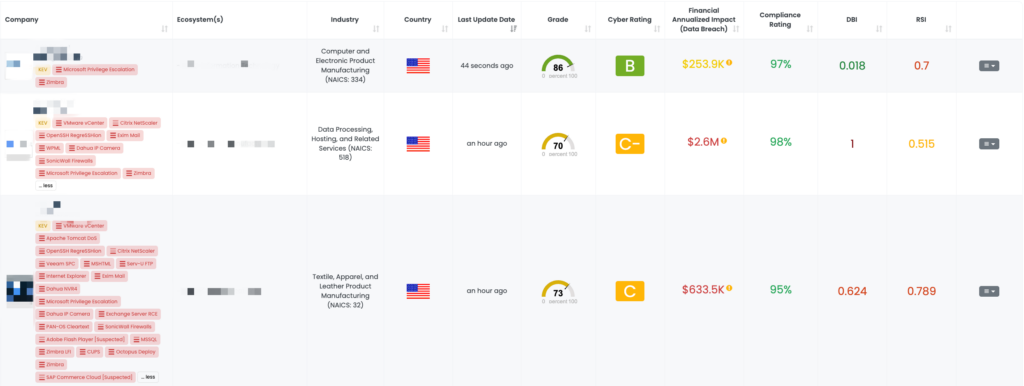
Maximizing TPRM Efficiency with Black Kite’s FocusTags™
Black Kite’s FocusTags™ redefine how organizations approach Third-Party Risk Management (TPRM) by providing actionable insights into the latest vulnerabilities, such as those affecting PAN-OS, PostgreSQL, and Apache Airflow. Here’s how these innovative tools can enhance TPRM strategies:
- Real-Time Threat Identification: FocusTags™ allow organizations to quickly pinpoint vendors impacted by critical vulnerabilities, enabling immediate action to mitigate risks.
- Strategic Risk Management: By combining vulnerability severity and vendor criticality, these tags help prioritize efforts where they are needed most.
- Enhanced Vendor Communication: FocusTags™ facilitates targeted and informed discussions with vendors, addressing their specific security challenges and exposures.
- Comprehensive Risk Visibility: Providing a panoramic view of the threat landscape, FocusTags™ enable TPRM teams to build stronger and more adaptive security ecosystems.
In an era of increasing cyber threats, Black Kite’s FocusTags™ offer an indispensable resource for managing third-party risks effectively and proactively. By transforming complex cyber threat data into clear, actionable intelligence, they empower organizations to safeguard their supply chains with confidence.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- PAN-OS: CVE-2024-0012, CVE-2024-9474, Authentication Bypass Vulnerability and Privilege Escalation Vulnerability in Palo Alto’s PAN-OS.
- PostgreSQL: CVE-2024-10979, Arbitrary Code Execution Vulnerability in PostgreSQL.
- Apache Airflow: CVE-2024-45784, Debug Messages Revealing Unnecessary Information in Apache Airflow.
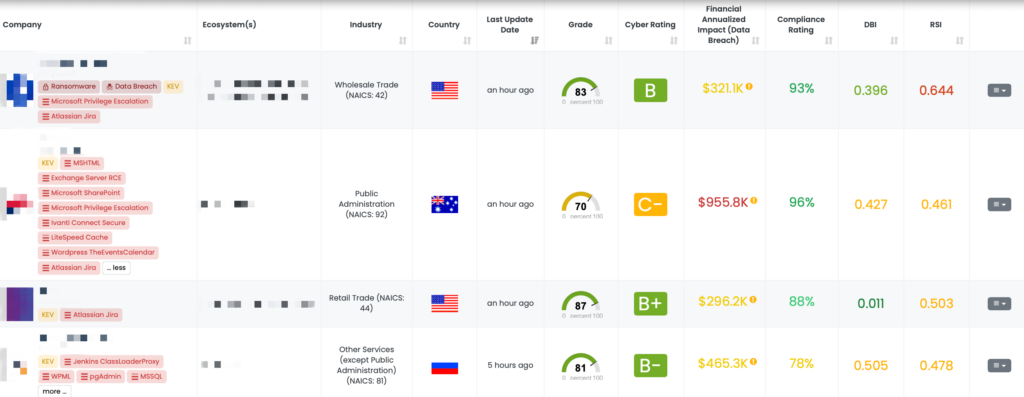
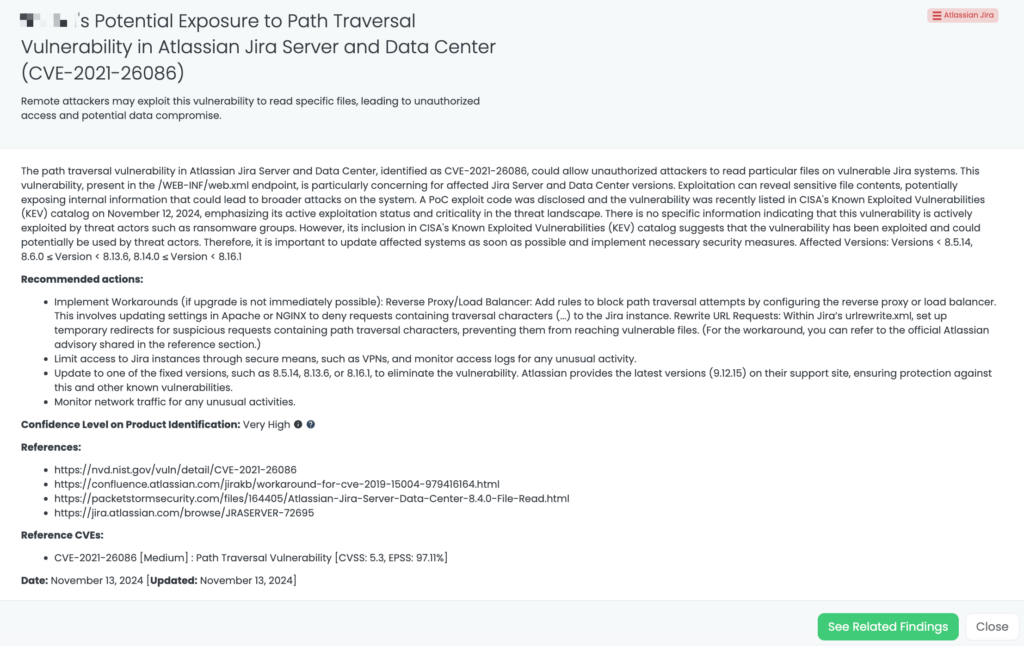
- Atlassian Jira: CVE-2021-26086, Path Traversal Vulnerability in Atlassian Jira Server and Data Center.
- Ivanti Connect Secure: CVE-2024-9420, CVE-2024-47906, CVE-2024-38655, CVE-2024-38656, CVE-2024-39710, CVE-2024-11007, CVE-2024-11006, CVE-2024-11005, and CVE-2024-11004, Use-After-Free, Stack-Based Buffer Overflow, Argument Injection, and Reflected XSS Vulnerabilities in Ivanti Connect Secure.
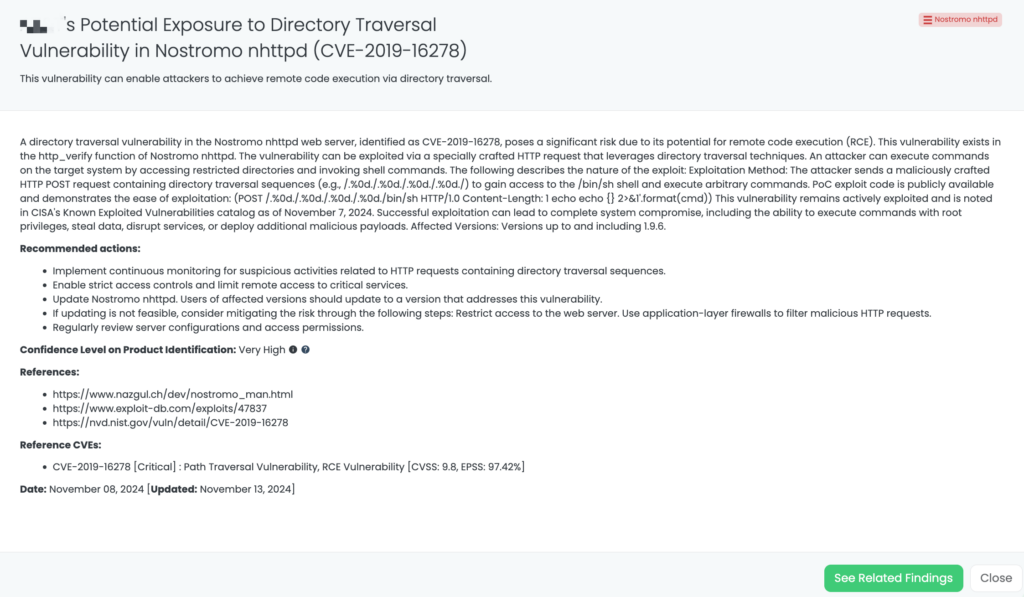
- Nostromo nhttpd: CVE-2019-16278, Path Traversal Vulnerability, RCE Vulnerability in Nostromo nhttpd.
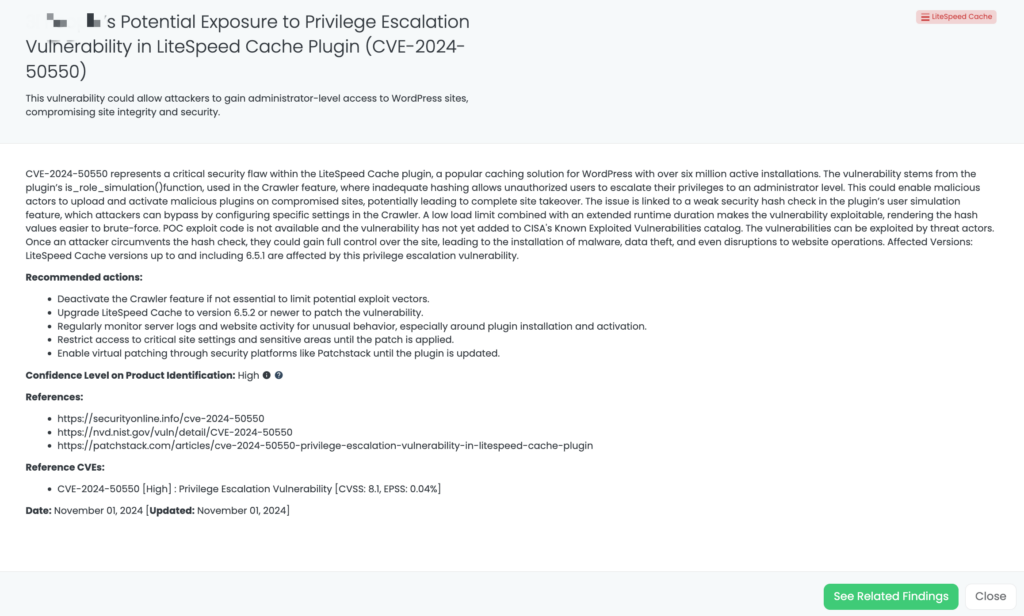
- LiteSpeed Cache: CVE-2024-50550, Privilege Escalation Vulnerability iin LiteSpeed Cache plugin.
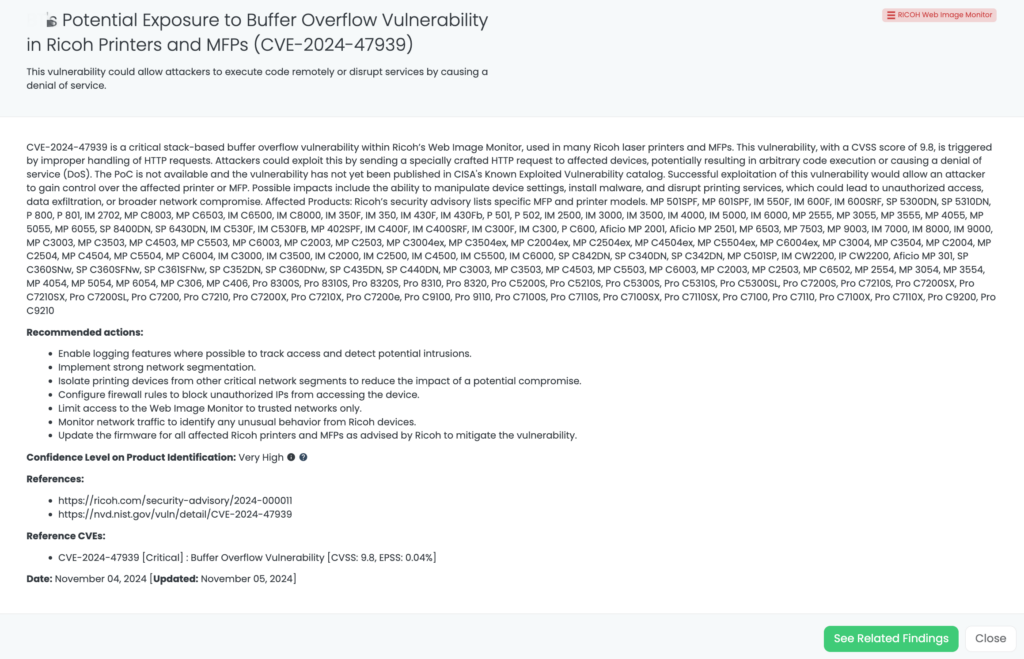
- RICOH Web Image Monitor: CVE-2024-47939, Buffer Overflow Vulnerability in RICOH Web Image Monitor.
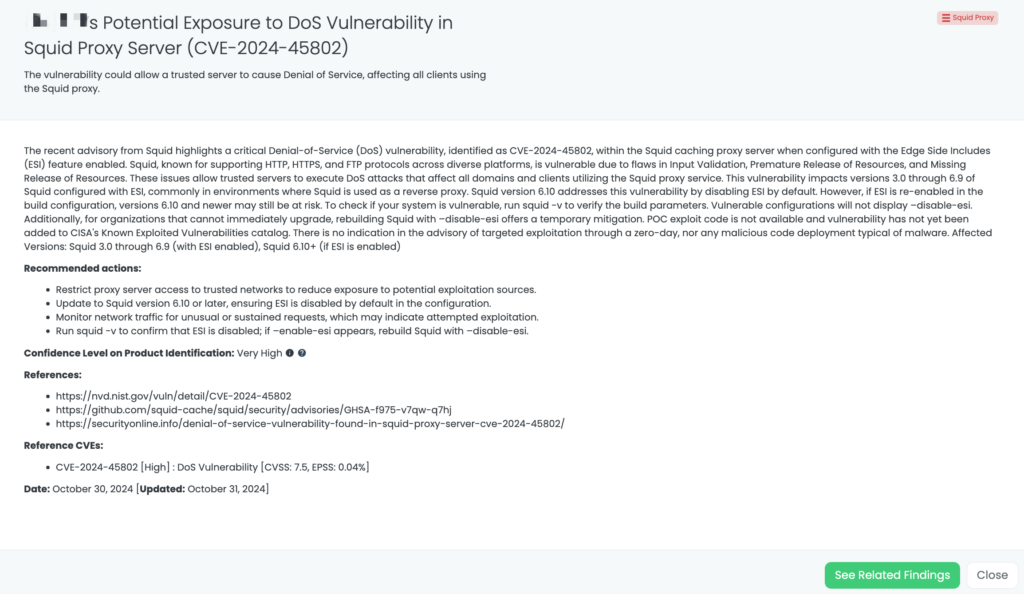
- Squid Proxy: CVE-2024-45802, DoS Vulnerability in Squid Proxy Servers.
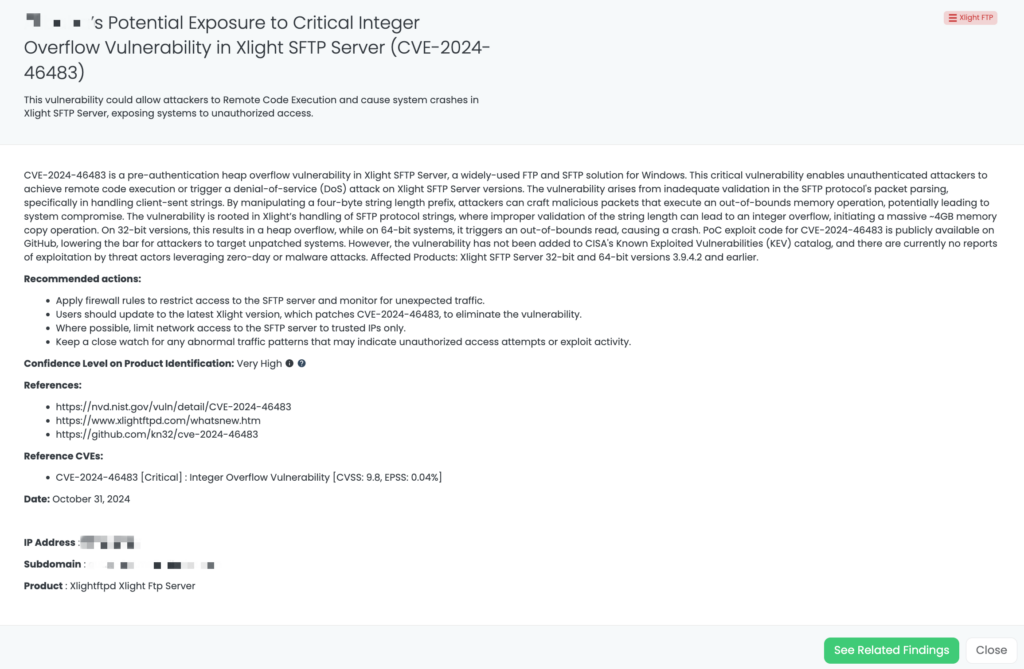
- XLight FTP: CVE-2024-46483, Integer Overflow and RCE Vulnerabilities in XLight FTP Servers.
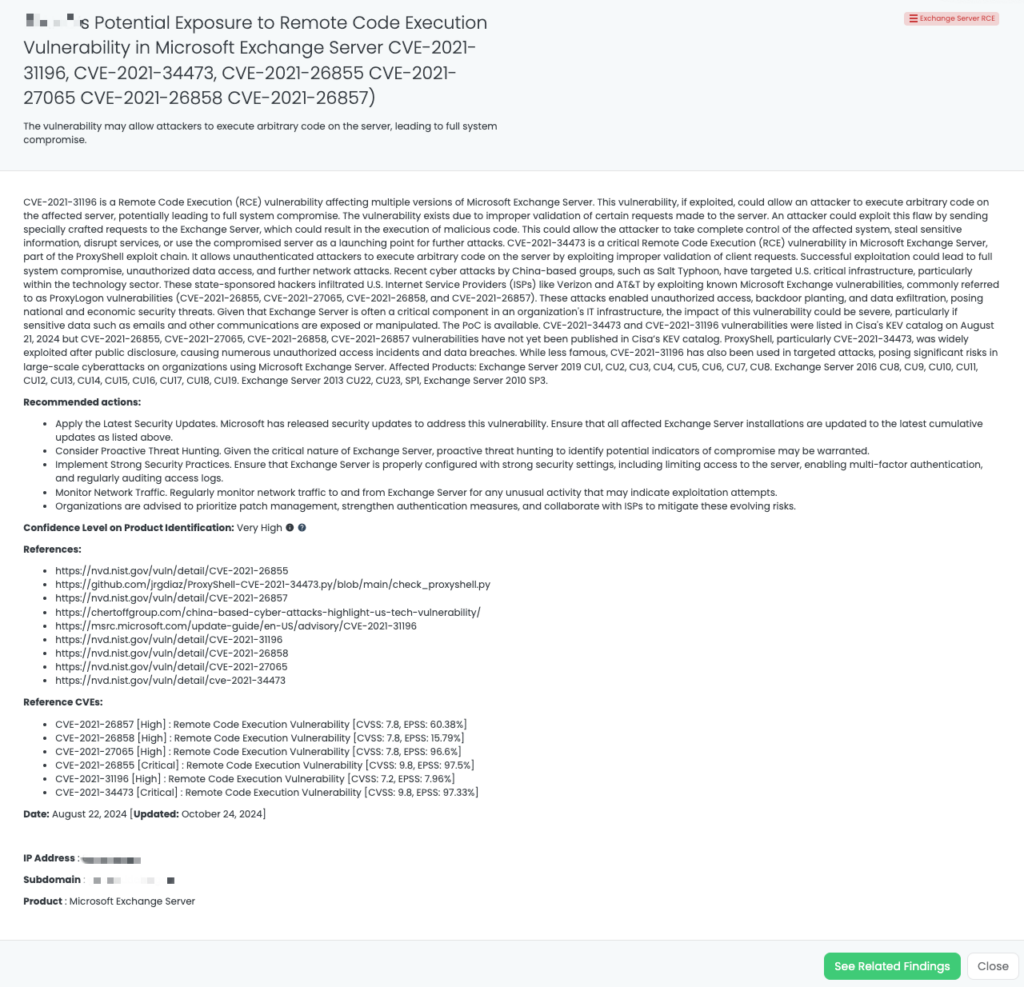
- Exchange Server RCE: CVE-2021-26855, CVE-2021-27065, CVE-2021-26858, CVE-2021-26857, Remote Code Execution Vulnerability in Exchange Server.
- FortiManager: CVE-2024-47575, Missing Authentication Vulnerability in FortiManager.
- Grafana: CVE-2024-9264, Remote Code Execution Vulnerability in Grafana.
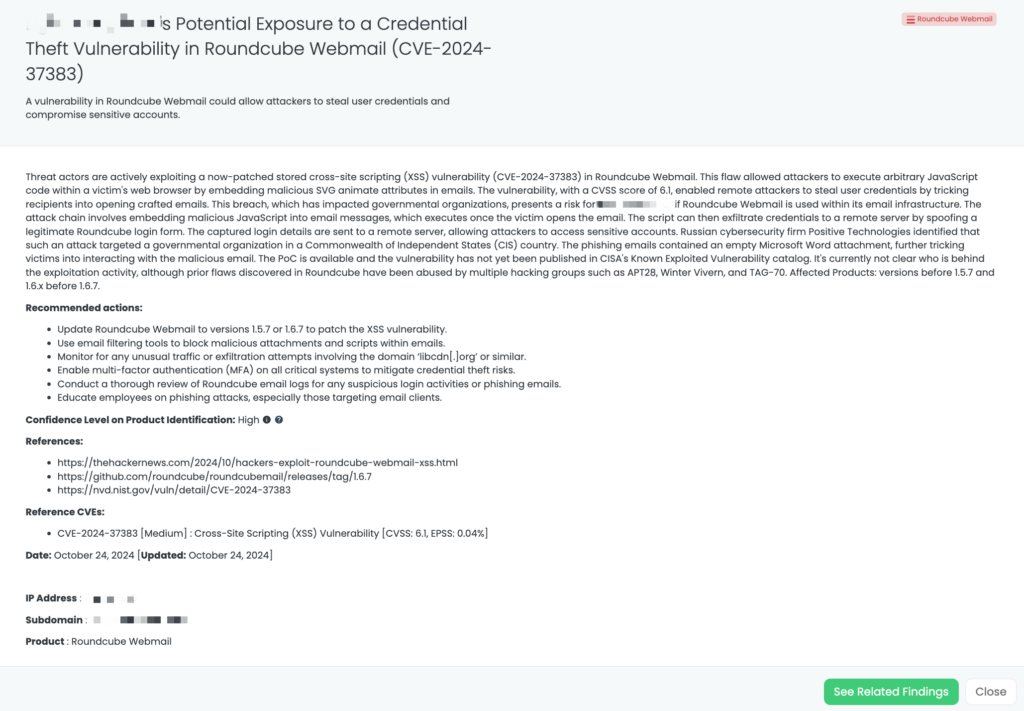
- Roundcube Webmail: CVE-2024-37383, Cross-Site Scripting (XSS) Vulnerability in Roundcube Webmail.
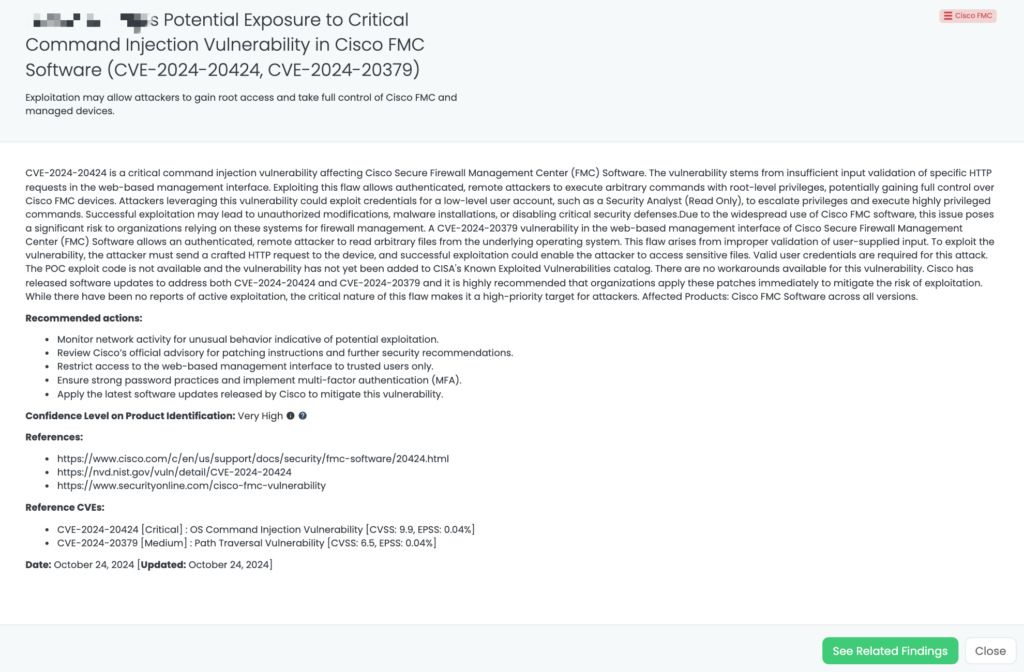
- Cisco FMC: CVE-2024-20424, Command Injection Vulnerability in Cisco Secure Firewall Management Center.
- Oracle WebLogic Server: CVE-2024-21216, Remote Code Execution Vulnerability in Oracle WebLogic Server.
- GitHub Enterprise: CVE-2024-9487, SAML SSO Authentication Bypass Vulnerability in GitHub Enterprise Server.
- Fortinet Core Products: CVE-2024-23113, Format String Vulnerability in FortiOS, FortiPAM, FortiProxy, and FortiWeb.
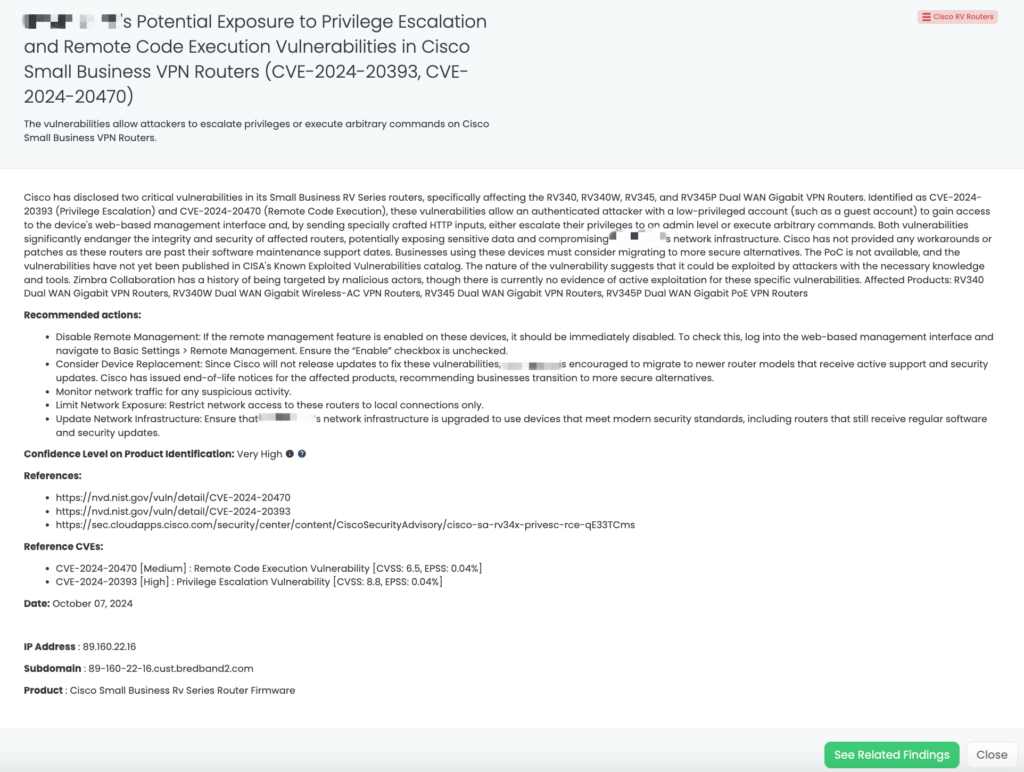
- Cisco RV Routers: CVE-2024-20393, CVE-2024-20470, Privilege Escalation and RCE Vulnerability in RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-0012
https://nvd.nist.gov/vuln/detail/CVE-2024-9474
https://security.paloaltonetworks.com/CVE-2024-0012
https://security.paloaltonetworks.com/CVE-2024-9474
https://nvd.nist.gov/vuln/detail/CVE-2024-10979
https://www.postgresql.org/support/security/CVE-2024-10979
https://github.com/apache/airflow/pull/43040
https://lists.apache.org/thread/k2jm55jztlbmk4zrlh10syvq3n57hl4h
The post Focus Friday: TPRM Insights On PAN-OS, PostgreSQL, and Apache Airflow Vulnerabilities appeared first on Black Kite.