DragonForce targets rivals in a play for dominance










































































































































A 23-year-old Scottish man thought to be a member of the prolific Scattered Spider cybercrime group was extradited last week from Spain to the United States, where he is facing charges of wire fraud, conspiracy and identity theft. U.S. prosecutors allege Tyler Robert Buchanan and co-conspirators hacked into dozens of companies in the United States and abroad, and that he personally controlled more than $26 million stolen from victims.
Scattered Spider is a loosely affiliated criminal hacking group whose members have broken into and stolen data from some of the world’s largest technology companies. Buchanan was arrested in Spain last year on a warrant from the FBI, which wanted him in connection with a series of SMS-based phishing attacks in the summer of 2022 that led to intrusions at Twilio, LastPass, DoorDash, Mailchimp, and many other tech firms.

Tyler Buchanan, being escorted by Spanish police at the airport in Palma de Mallorca in June 2024.
As first reported by KrebsOnSecurity, Buchanan (a.k.a. “tylerb”) fled the United Kingdom in February 2023, after a rival cybercrime gang hired thugs to invade his home, assault his mother, and threaten to burn him with a blowtorch unless he gave up the keys to his cryptocurrency wallet. Buchanan was arrested in June 2024 at the airport in Palma de Mallorca while trying to board a flight to Italy. His extradition to the United States was first reported last week by Bloomberg.
Members of Scattered Spider have been tied to the 2023 ransomware attacks against MGM and Caesars casinos in Las Vegas, but it remains unclear whether Buchanan was implicated in that incident. The Justice Department’s complaint against Buchanan makes no mention of the 2023 ransomware attack.
Rather, the investigation into Buchanan appears to center on the SMS phishing campaigns from 2022, and on SIM-swapping attacks that siphoned funds from individual cryptocurrency investors. In a SIM-swapping attack, crooks transfer the target’s phone number to a device they control and intercept any text messages or phone calls to the victim’s device — including one-time passcodes for authentication and password reset links sent via SMS.
In August 2022, KrebsOnSecurity reviewed data harvested in a months-long cybercrime campaign by Scattered Spider involving countless SMS-based phishing attacks against employees at major corporations. The security firm Group-IB called them by a different name — 0ktapus, because the group typically spoofed the identity provider Okta in their phishing messages to employees at targeted firms.
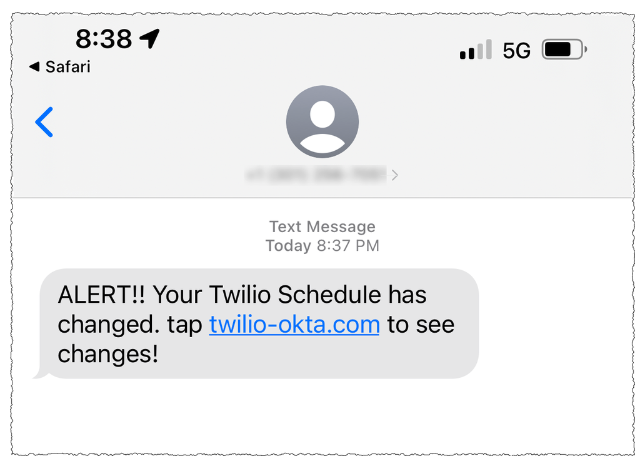
A Scattered Spider/0Ktapus SMS phishing lure sent to Twilio employees in 2022.
The complaint against Buchanan (PDF) says the FBI tied him to the 2022 SMS phishing attacks after discovering the same username and email address was used to register numerous Okta-themed phishing domains seen in the campaign. The domain registrar NameCheap found that less than a month before the phishing spree, the account that registered those domains logged in from an Internet address in the U.K. FBI investigators said the Scottish police told them the address was leased to Buchanan from January 26, 2022 to November 7, 2022.
Authorities seized at least 20 digital devices when they raided Buchanan’s residence, and on one of those devices they found usernames and passwords for employees of three different companies targeted in the phishing campaign.
“The FBI’s investigation to date has gathered evidence showing that Buchanan and his co-conspirators targeted at least 45 companies in the United States and abroad, including Canada, India, and the United Kingdom,” the FBI complaint reads. “One of Buchanan’s devices contained a screenshot of Telegram messages between an account known to be used by Buchanan and other unidentified co-conspirators discussing dividing up the proceeds of SIM swapping.”
U.S. prosecutors allege that records obtained from Discord showed the same U.K. Internet address was used to operate a Discord account that specified a cryptocurrency wallet when asking another user to send funds. The complaint says the publicly available transaction history for that payment address shows approximately 391 bitcoin was transferred in and out of this address between October 2022 and
February 2023; 391 bitcoin is presently worth more than $26 million.
In November 2024, federal prosecutors in Los Angeles unsealed criminal charges against Buchanan and four other alleged Scattered Spider members, including Ahmed Elbadawy, 23, of College Station, Texas; Joel Evans, 25, of Jacksonville, North Carolina; Evans Osiebo, 20, of Dallas; and Noah Urban, 20, of Palm Coast, Florida. KrebsOnSecurity reported last year that another suspected Scattered Spider member — a 17-year-old from the United Kingdom — was arrested as part of a joint investigation with the FBI into the MGM hack.
Mr. Buchanan’s court-appointed attorney did not respond to a request for comment. The accused faces charges of wire fraud conspiracy, conspiracy to obtain information by computer for private financial gain, and aggravated identity theft. Convictions on the latter charge carry a minimum sentence of two years in prison.
Documents from the U.S. District Court for the Central District of California indicate Buchanan is being held without bail pending trial. A preliminary hearing in the case is slated for May 6.
May 2025 was a busy month in the world of cybersecurity news, and not in a good way! The massive Marks and Spencer cyber attack continued to make headlines almost every other day. Read all about the new twists and turns in the M&S cybersecurity saga in our Updated Marks and Spencer Cyber Attack Timeline.
A massive cyber-attack on retail giant Marks and Spencer leads to postponed deliveries, halted online transactions, and frozen gift card processing. A large-scale phishing campaign compromises corporate email marketing accounts at Mailchimp, SendGrid, HubSpot, Mailgun, and Zoho. Car Rental Giant Hertz begins notifying customers of a massive breach of data.
And all of this is just the tip of the iceberg when it comes to the major cyber attacks, ransomware attacks and data breaches of April 2025.
Written by: Ferdi Gül
This Week’s Emerging Third-Party Risks in Email Infrastructure and Web Frameworks
Welcome to this week’s edition of Focus Friday, where we provide timely insights into high-profile vulnerabilities from a Third-Party Risk Management (TPRM) lens. In today’s interconnected environment, vulnerabilities affecting one vendor’s technology stack can ripple across entire ecosystems—disrupting operations, compromising sensitive data, and escalating vendor risk exposure.
This week’s FocusTags™ spotlight several notable vulnerabilities with direct implications for organizations relying on third-party software for communication infrastructure and web application delivery. We begin with Zimbra’s CalendarInvite XSS vulnerability, already being exploited by APT28; then examine DrayTek Vigor gateway devices, which are being recruited into botnets due to a critical OS command injection flaw. We also review a newly disclosed privilege escalation vulnerability in Atlassian Jira Data Center, which allows low-privilege users to act with higher-privilege permissions, threatening issue tracking and service management workflows. In addition, we cover a Denial-of-Service vulnerability in Tornado Web Server that threatens application availability, and an actively exploited zero-day XSS vulnerability in MDaemon Email Server, used for credential theft and mailbox compromise.
Each of these incidents highlights the urgency of identifying and remediating vulnerabilities—not just internally, but across your third-party network. This blog helps TPRM professionals do exactly that.
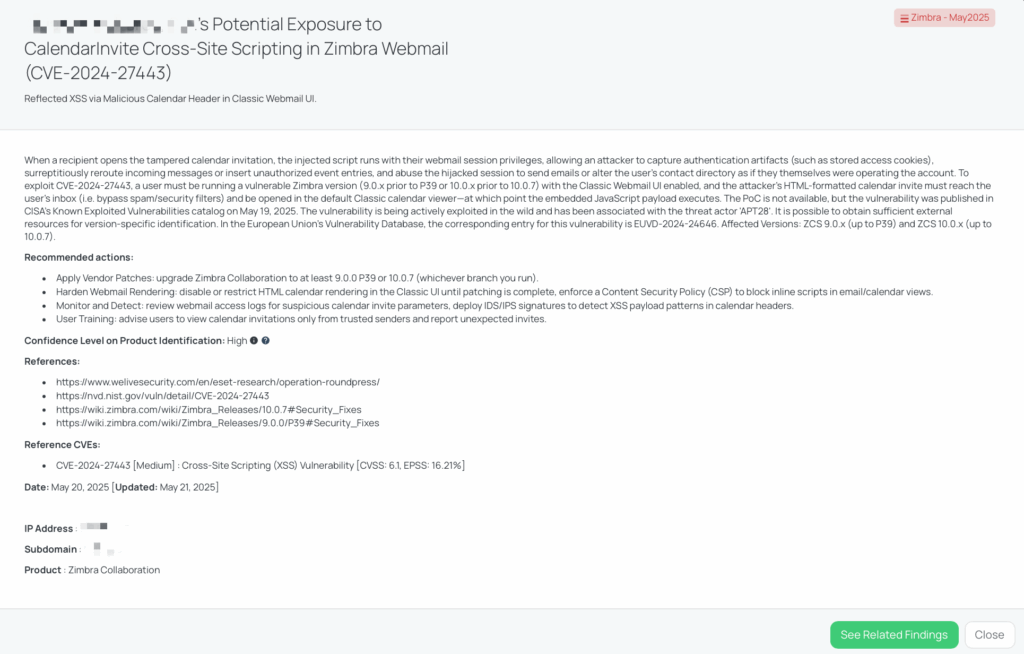
CVE-2024-27443 is a medium-severity reflected Cross-Site Scripting (XSS) vulnerability affecting Zimbra Collaboration Suite (ZCS) versions 9.0.x (prior to Patch 39) and 10.0.x (prior to 10.0.7). The flaw resides in the Classic Webmail UI’s CalendarInvite feature, where the X-Zimbra-Calendar-Intended-For email header is improperly sanitized. This allows attackers to inject malicious JavaScript into calendar invitations.
When a user opens a crafted calendar invite in the Classic UI, the embedded script executes within their webmail session, potentially enabling attackers to:
The vulnerability has a CVSS v3.1 score of 6.1 (Medium) and an EPSS score of 16.22%. It was patched on March 1, 2024, but was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025, indicating active exploitation in the wild. Notably, the Sednit group (also known as APT28) has been linked to exploiting this vulnerability as part of Operation RoundPress, targeting governmental and defense entities in Eastern Europe and beyond.
Zimbra is widely used for enterprise email and calendar services. A compromise of its webmail interface can lead to unauthorized access to sensitive communications and data. The exploitation of CVE-2024-27443 allows attackers to impersonate users, exfiltrate confidential information, and potentially pivot to other systems within the organization.Given the association with APT28, a state-sponsored threat actor, the risk extends to espionage and targeted attacks against critical sectors.
Black Kite has issued the “Zimbra – May2025” FocusTag, providing high-confidence intelligence on vendors potentially exposed to CVE-2024-27443. This tag includes detailed information such as affected assets, IP addresses, and subdomains associated with vulnerable Zimbra deployments. By utilizing this FocusTag, TPRM professionals can:
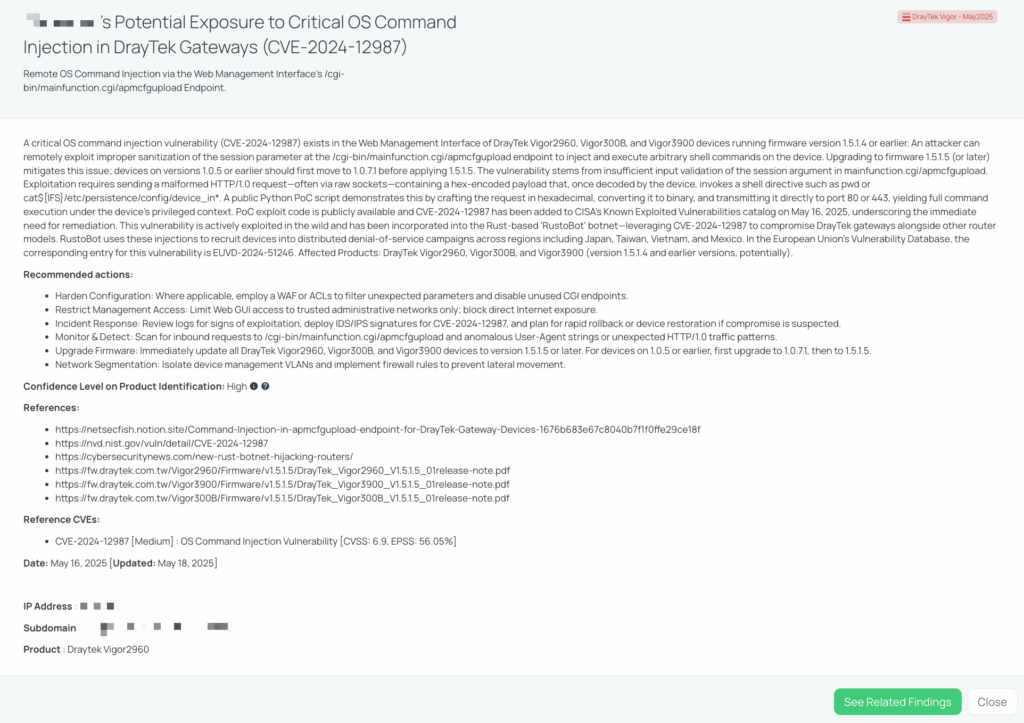
CVE-2024-12987 is a critical OS command injection vulnerability affecting DrayTek Vigor2960, Vigor300B, and Vigor3900 routers running firmware version 1.5.1.4 or earlier. The flaw resides in the Web Management Interface’s /cgi-bin/mainfunction.cgi/apmcfgupload endpoint, where improper sanitization of the session parameter allows remote attackers to inject and execute arbitrary shell commands.
An attacker can exploit this vulnerability by sending a specially crafted HTTP/1.0 request with a hex-encoded payload to the vulnerable endpoint, resulting in command execution with elevated privileges. A public proof-of-concept (PoC) script demonstrates this exploitation method.
The vulnerability has a CVSS v3.1 score of 9.8 (Critical) and an EPSS score of 56.05%. It was added to CISA’s Known Exploited Vulnerabilities catalog on May 16, 2025, indicating active exploitation in the wild. Notably, the Rust-based botnet “RustoBot” leverages this vulnerability to compromise DrayTek gateways, recruiting them into distributed denial-of-service (DDoS) campaigns across regions including Japan, Taiwan, Vietnam, and Mexico.
DrayTek Vigor devices are commonly used as network gateways in enterprise environments. A compromise of these devices can lead to unauthorized access to internal networks, data exfiltration, and service disruptions. The exploitation of CVE-2024-12987 allows attackers to execute arbitrary commands, potentially leading to full device compromise and lateral movement within the network. Given the active exploitation by botnets like RustoBot, the risk extends to participation in large-scale DDoS attacks, amplifying the potential impact on both the compromised organization and external targets.
Black Kite has issued the “DrayTek Vigor – May2025” FocusTag, providing high-confidence intelligence on vendors potentially exposed to CVE-2024-12987. This tag includes detailed information such as affected assets, IP addresses, and subdomains associated with vulnerable DrayTek deployments. By utilizing this FocusTag, TPRM professionals can:
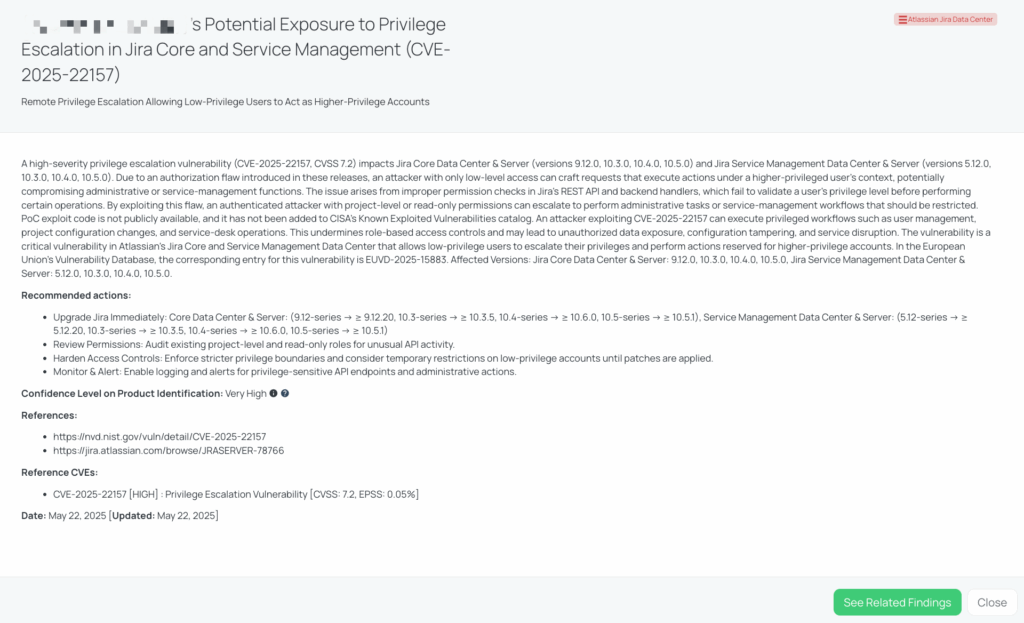
CVE-2025-22157 is a high-severity privilege escalation vulnerability affecting Atlassian Jira Core and Jira Service Management Data Center and Server editions. This flaw allows authenticated users with low-level permissions to perform actions under higher-privileged accounts by exploiting improper permission checks in Jira’s REST API and backend handlers. The vulnerability was introduced in versions 9.12.0, 10.3.0, 10.4.0, and 10.5.0 of Jira Core, and versions 5.12.0, 10.3.0, 10.4.0, and 10.5.0 of Jira Service Management.
With a CVSS score of 7.2 and an EPSS score of 0.05%, this vulnerability poses a significant risk, allowing attackers to compromise administrative functions, alter project configurations, and disrupt service-desk operations. As of now, there is no public PoC exploit code, and the vulnerability has not been added to CISA’s Known Exploited Vulnerabilities catalog.
Jira Data Center is widely used for project management, issue tracking, and service management across various industries. A privilege escalation vulnerability in such a critical system can lead to unauthorized access to sensitive data, disruption of workflows, and potential compliance violations. Third-party vendors using vulnerable versions of Jira may inadvertently expose your organization to these risks.
Black Kite published the FocusTag for CVE-2025-22157 on May 22, 2025. This tag enables TPRM professionals to identify third-party vendors that may be affected by this vulnerability. By providing asset information such as IP addresses and subdomains, Black Kite allows for a more precise assessment of potential risks within your supply chain. Utilizing this information, you can prioritize remediation efforts, engage in informed discussions with vendors, and enhance your organization’s overall cybersecurity posture.
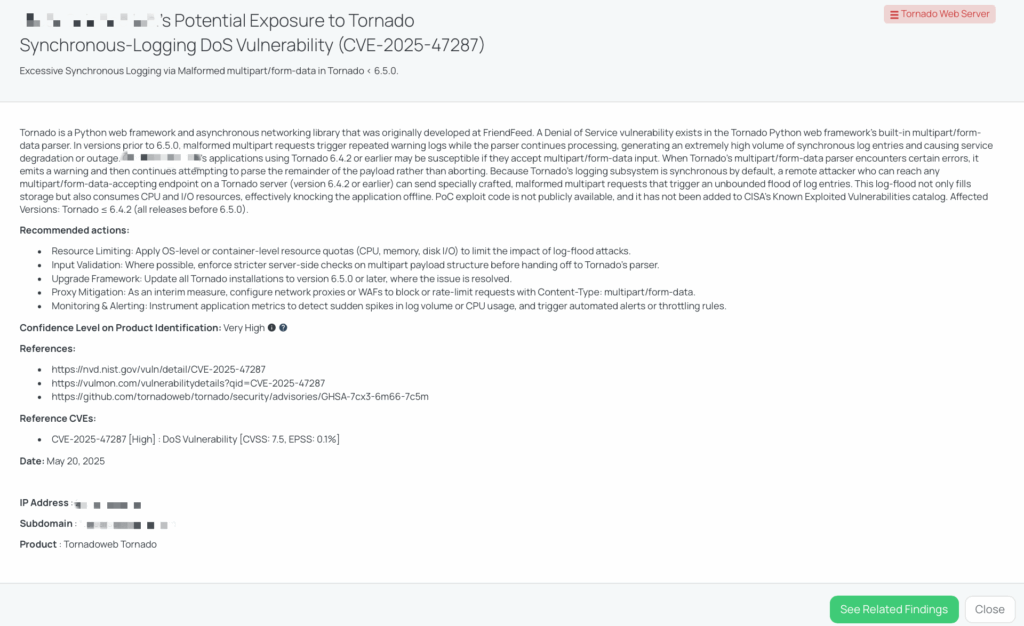
CVE-2025-47287 is a high-severity Denial-of-Service (DoS) vulnerability affecting Tornado, a Python-based asynchronous web framework and networking library. The vulnerability arises from the way Tornado’s built-in multipart/form-data parser handles malformed inputs. In affected versions (all releases prior to 6.5.0), if the parser encounters certain structural issues in multipart requests, it logs a warning message but continues attempting to parse the rest of the request.
Because Tornado’s logging system operates synchronously by default, an attacker can remotely send a malformed multipart request to any vulnerable endpoint. This causes the application to generate a large volume of log entries, rapidly consuming disk space, CPU, and I/O resources. The attack does not require authentication or complex exploitation, and the affected parser is enabled by default.
This vulnerability carries a CVSS score of 7.5 (High) and an EPSS score of 0.10%. It was publicly disclosed on May 15, 2025, through GitHub’s security advisory system. There is no evidence of exploitation in the wild, and the issue has not been added to CISA’s Known Exploited Vulnerabilities catalog. Likewise, CISA has not issued an advisory regarding this vulnerability at this time.
While the vulnerability does not provide direct access to sensitive data or remote code execution capabilities, it poses a significant threat to service availability, which can have downstream effects on any integrated or dependent systems. Organizations using Tornado in public-facing APIs or web applications may experience partial or complete outages if targeted with malformed multipart/form-data payloads.
From a third-party risk management (TPRM) perspective, vendors who use Tornado in production environments without proper traffic filtering or resource limits may unknowingly expose critical services to denial-of-service scenarios. If such services are part of an enterprise’s supply chain—such as SaaS products or integration providers—disruptions may cascade into the organization’s own operations, undermining continuity and performance expectations.
Vendors who maintain Tornado-based systems should take the following technical steps to mitigate risk:
Black Kite published the Tornado Web Server FocusTag on May 20, 2025, in response to the disclosure of CVE-2025-47287. This tag enables TPRM professionals to identify vendors potentially running vulnerable versions of Tornado, especially those with public-facing services that may accept multipart/form-data inputs.
The FocusTag offers very high confidence in product identification and includes granular intelligence such as subdomain and IP address visibility, helping organizations zero in on real exposure rather than issuing broad-based surveys. Operationalizing this tag allows risk teams to prioritize follow-ups with only the vendors that are relevant to this incident, saving time and reducing unnecessary noise in communication workflows.
The tag is set to expire on August 31, 2025, unless new developments warrant an update. Black Kite’s ability to tie internet-facing telemetry to software versioning ensures that customers receive actionable third-party insights rather than generic alerts.
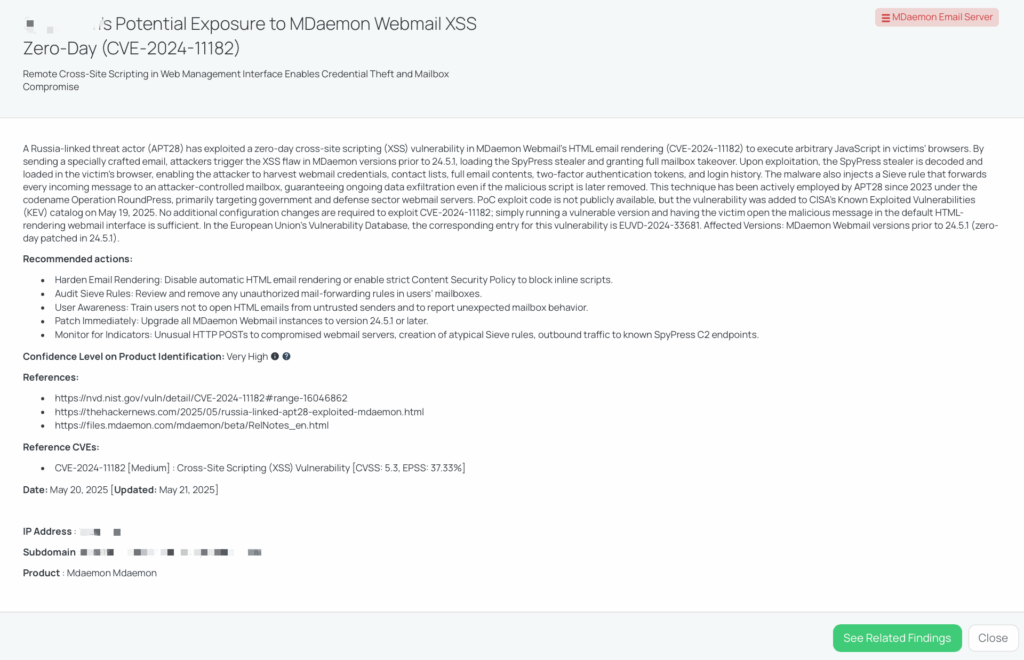
CVE-2024-11182 is a medium-severity cross-site scripting (XSS) vulnerability affecting MDaemon Email Server versions prior to 24.5.1. The flaw resides in the webmail interface’s HTML email rendering component, where improper sanitization allows attackers to inject malicious JavaScript code via specially crafted emails. This vulnerability enables remote attackers to execute arbitrary scripts in the context of the user’s browser session, potentially leading to credential theft and unauthorized access to sensitive information.
The vulnerability has a CVSS score of 6.1 and an EPSS score of 37.33%. It was actively exploited as a zero-day by the Russia-linked threat actor APT28 (also known as Fancy Bear or Sednit) in a campaign dubbed “Operation RoundPress,” targeting government and defense sector webmail servers. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024-11182 to its Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025, highlighting its active exploitation in the wild.
MDaemon Email Server is widely used by organizations for email communication. Exploitation of CVE-2024-11182 can lead to unauthorized access to email accounts, exposure of sensitive communications, and potential lateral movement within an organization’s network. For third-party risk management (TPRM) professionals, this vulnerability poses significant concerns:
To assess the risk associated with this vulnerability, TPRM professionals should inquire:
Vendors utilizing MDaemon Email Server should take the following actions:
Black Kite provides visibility into third-party vulnerabilities, including CVE-2024-11182. By utilizing Black Kite’s platform, TPRM professionals can:
When high-impact vulnerabilities like those found in Zimbra, DrayTek Vigor, Atlassian Jira Data Center, Tornado, and MDaemon emerge, time is of the essence. Black Kite’s FocusTags™ offer organizations a strategic advantage by transforming complex threat data into actionable intelligence—enabling faster, more focused responses to third-party exposure.
Here’s how FocusTags™ enhance your TPRM program:
By operationalizing Black Kite’s FocusTags™, TPRM professionals can cut through the noise and quickly narrow their focus to the vendors that truly require attention—enhancing resilience in an ever-evolving threat landscape.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
The post Focus Friday: TPRM Insights into Zimbra, Draytek Vigor, Atlassian Jira Data Center, Tornado, and MDaemon Vulnerabilities appeared first on Black Kite.
Written by: Ferhat Dikbiyik, Chief Research & Intelligence Officer
With over 40,000 vulnerabilities disclosed last year—a 38% jump from the year prior—the real challenge for third-party risk management (TPRM) professionals isn’t knowing which risks exist. It’s knowing which ones to act on and how—a task made particularly difficult when managing risk across hundreds of vendors.
In Part 1 of our series, I introduced a three-dimensional approach to cybersecurity vulnerability management in TPRM—detailed in our 2025 Supply Chain Vulnerability Report—to help teams prioritize vulnerabilities in the supply chain based on severity, exploitability, and exposure. This dramatically narrows the field from tens of thousands of Common Vulnerabilities & Exposures (CVEs) to a much more manageable number.
But identifying risk is only half of the process. Acting on it is the other half.
In this second video, I walk through how TPRM teams can operationalize vulnerability intelligence, moving beyond theoretical prioritization to real-world application. Using tools like Black Kite’s FocusTags™, teams can gain clear visibility into which vulnerabilities are most urgent, which vendors might be exposed, and what steps to take for remediation.
View this video on YouTube.
A vulnerability’s CVSS score can clue you into potential severity, while its EPSS score can help predict the likelihood of exploitation. But neither tells the full story. Some vulnerabilities look dangerous on paper but are rarely exploited, while others fly under the radar until they become the entry point for a major breach.
Black Kite’s FocusTags help security teams tell the difference, surfacing the CVEs that are highly likely to be exploited, regardless of their severity level. It does this by layering in real-world signals that indicate whether bad actors are likely to attack.
Analyzing these risk factors, FocusTags help TPRM teams detect not just the most severe vulnerabilities, but also the ones most likely to be weaponized. Instead of reacting to every “critical” CVE, teams can focus on the ones that pose the greatest risk to their supply chain.
Most TPRM programs still depend on slow, reactive processes—waiting for vendor disclosures, following up on questionnaires, and hoping for timely responses. But the gap between disclosure and exploitation is shrinking fast: In 2021, attackers took 42 days on average to exploit a new CVE. By 2023, that window dropped to just 5 days.
When exploitation moves that quickly, speed matters.
FocusTags enable a more proactive approach, helping security teams shift from passive monitoring to active risk hunting. Through Black Kite’s Risk Intelligence page, teams can identify which vendors are likely exposed, track changes in exposure over time, and access vendor-specific guidance to drive faster remediation.
To make action even more precise, we recently introduced Vulnerability Intelligence Briefs (VIBs) which offer detailed views of each CVE and where they are found in our customers’ supply chains. Think of them like baseball cards, but for vulnerabilities: each one gives you the essential stats you need to understand the risk and act fast.
If a CVE affects a vendor in your ecosystem, the brief tells you who’s likely running it and what questions to ask to confirm and resolve it. With these insights, you can act early, armed with the data needed to initiate informed, targeted vendor outreach.
Third-party risk management isn’t about chasing every vulnerability—it’s about knowing which ones warrant your attention and moving quickly. And that requires more than static scores or vendor questionnaires.
As exploitation timelines shrink and supply chains become more complex, security teams need context on which they can act. Tools like FocusTags help meet that need, highlighting the vulnerabilities that require immediate attention due to exposure, exploitability, and third-party risk.
This kind of actionable vulnerability assessment is what defines the future of TPRM. By understanding attacker behavior, identifying vendor exposure, and prioritizing action based on real-world signals, security teams can move beyond reactive patching and toward a more strategic defense of their third-party ecosystem.
Read the full 2025 Supply Chain Vulnerability Report for more insights on how to apply vulnerability intelligence across your vendor ecosystem.
Read our full 2025 Supply Chain Vulnerability Report: Navigating a New Era of Managing Vulnerability Risk in Third Parties – accessible instantly, no download required.
The post How to Implement Vulnerability Management in TPRM appeared first on Black Kite.
Written by: Ferdi Gül
Welcome to this week’s Focus Friday, where we delve into high-profile incidents from a Third-Party Risk Management (TPRM) perspective. This week, we’re focusing on vulnerabilities discovered in Ivanti’s Endpoint Manager Mobile (EPMM). Specifically, we’ll address two critical flaws, CVE-2025-4427 (Authentication Bypass) and CVE-2025-4428 (Remote Code Execution), which, when exploited together, allow unauthenticated attackers to bypass authentication and execute arbitrary code remotely on affected systems. These vulnerabilities, if left unchecked, could pose a serious threat to organizations using Ivanti EPMM for mobile device management. Read on to explore the details and how Black Kite’s FocusTags™ can assist in managing the associated risks.
Ivanti Endpoint Manager Mobile (EPMM) has two vulnerabilities, CVE-2025-4427 and CVE-2025-4428, that are critical for organizations using this software for mobile device management. These vulnerabilities, when chained together, allow unauthenticated attackers to bypass authentication and execute arbitrary code remotely on the affected systems.
Both vulnerabilities were discovered and publicly disclosed in May 2025, and there are reports of active exploitation in the wild. However, no PoC exploit code has been publicly released. The vulnerabilities were not added to CISA’s KEV catalog as of the time of disclosure.
For third-party risk management (TPRM) professionals, these vulnerabilities pose a severe risk because they impact the integrity and availability of the mobile device management (MDM) infrastructure. Organizations using Ivanti EPMM for mobile device management may be exposed to potential breaches, unauthorized access, and even complete control over their devices and networks.
If attackers successfully exploit these vulnerabilities, they could gain access to sensitive data and internal configurations, leading to further lateral movement in the network. This makes it essential for TPRM professionals to assess the risk posed by vendors using Ivanti EPMM, especially those running vulnerable versions.
Black Kite’s FocusTag for Ivanti EPMM highlights the affected versions and helps TPRM professionals quickly identify vendors exposed to these critical vulnerabilities. By using Black Kite’s platform, TPRM teams can determine which vendors are affected, identify any potentially vulnerable assets (like IP addresses and subdomains), and prioritize outreach to those vendors for remediation.
The FocusTag also provides actionable intelligence, such as the specific versions at risk and recommendations for mitigations. This enables organizations to proactively manage their risk exposure and make data-driven decisions.
Since this is a new FocusTag, it provides an updated and detailed analysis of the risk posed by Ivanti EPMM vulnerabilities. Black Kite customers can operationalize this tag by integrating the identified vulnerabilities into their risk management workflows, ensuring a more targeted and efficient vendor outreach process.

In April 2025, Black Kite’s FocusTag for SAP NetWeaver included a series of vulnerabilities that continue to pose a significant threat to organizations relying on this enterprise platform. As of May 2025, the situation has escalated, with multiple ransomware groups now actively exploiting these vulnerabilities.
The CVE-2025-42999, an insecure deserialization vulnerability in SAP NetWeaver Visual Composer’s Metadata Uploader, has been added to the existing SAP NetWeaver VCFRAMEWORK [Suspected] FocusTag. This vulnerability allows privileged users to upload untrusted serialized content, which, when deserialized, can severely compromise the system’s confidentiality, integrity, and availability.
The vulnerability has been actively exploited by several threat actor groups, including notorious ransomware gangs. As detailed in SAP’s May 2025 Security Patch Day alert, the RansomEXX and BianLian ransomware groups are targeting SAP NetWeaver systems with this flaw. While no ransomware payloads have been successfully deployed, the ongoing exploitation is a stark reminder of the continuing risk posed by this vulnerability. Additionally, several Chinese APT groups are also targeting unpatched NetWeaver instances, with evidence suggesting strategic objectives tied to espionage.
The addition of CVE-2025-42999 to the SAP NetWeaver FocusTag further emphasizes the critical nature of this vulnerability. TPRM professionals must now be even more vigilant in identifying vendors and third parties that rely on SAP NetWeaver systems. With active exploitation reported in the wild, including by sophisticated ransomware actors, the risk to organizations’ operational continuity is heightened.
If you’re managing third-party risks related to SAP NetWeaver, it is crucial to ensure that vendors have applied the latest patches and are actively monitoring for suspicious activity, especially around Visual Composer and its related components. Prompt remediation and proactive monitoring will be key to preventing a potential breach.
For those following the SAP NetWeaver VCFRAMEWORK [Suspected] FocusTag, stay informed on new CVEs and exploit activity to adjust your risk mitigation strategies accordingly.
In today’s rapidly evolving cybersecurity landscape, staying ahead of vulnerabilities is crucial for robust Third-Party Risk Management (TPRM). Black Kite’s FocusTags™ provide essential insights and tools to effectively manage these risks, especially in the face of emerging threats like those found in Ivanti EPMM and SAP NetWeaver.
Here’s how Black Kite’s FocusTags™ can enhance your TPRM strategy:
Black Kite’s FocusTags™ transform complex cyber threat data into actionable intelligence, empowering TPRM professionals to effectively manage risks, reduce exposure, and bolster security.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
The post FOCUS FRIDAY: TPRM Insights on Ivanti EPMM and SAP NetWeaver Vulnerabilities – Ongoing Threat Actor/Ransomware Groups Activity appeared first on Black Kite.
Written by: Dr. Ferhat Dikbiyik, Chief Research & Intelligence Officer
“What percentage of CVEs do you cover?”
It’s a question we hear a lot at Black Kite. It’s reasonable on the surface, but ultimately misleading.
It’s like asking a meteorologist how many weather events they track. The number might be high, but it tells you nothing about whether a severe storm is headed for your house. The same logic applies here. The total count of vulnerabilities a platform covers—or claims to cover—doesn’t actually tell you how well it assesses risk to your business.
At Black Kite, we don’t optimize for volume. We optimize for relevance, discoverability, and actionability. Because when it comes to third-party risk, more data is not necessarily better data. It’s just more noise.
More than 40,000 CVEs were published in 2024. Narrow it down to those with a CVSS score above 9.0, and you’re still looking at more than 4,400 critical issues.
Understandably, many security teams start with scale: How much of that are we tracking? However, “coverage” is a flawed metric. Here’s why:
1. It depends entirely on the scope.
What’s being covered? Every CVE ever published? Just critical ones? Only those with active exploitation? The definition of “coverage” varies so widely that it becomes almost meaningless.
2. Visibility is variable.
We identify vulnerable software versions only when they’re visible via OSINT—through headers, banners, exposed services, and so on. Not every version leaves enough of a fingerprint to be seen externally (i.e., discoverable by bad actors). As detection techniques evolve, our coverage evolves. This isn’t a static number.
3. More CVEs don’t mean better insight.
If a system is severely outdated, it’s already high-risk. Tagging it with 500 additional CVEs doesn’t make it more actionable. In fact, it often dilutes the signal. What matters is knowing the right vulnerabilities, not all of them.
The takeaway? CVE count is a distraction. What’s important is whether the vulnerabilities you can see are the ones that matter—and whether they’re likely to be exploited in the wild.
At Black Kite, our job isn’t to show you every CVE (although we do offer quite a robust CVE database with TPRM insights to the public). For our customers, our job is to surface the few dozen vulnerabilities that truly matter for your vendor ecosystem—so you can act quickly and decisively.
We get there in two ways.
Our platform continuously scans exposed infrastructure using passive OSINT techniques like banner grabbing, protocol response analysis, and header inspection. From that, we extract product and version data (when available), match it to known Common Platform Enumerations (CPEs), and map it to vulnerabilities from NIST’s National Vulnerability Database.
We apply strict filters to keep the output meaningful:
For example, if we find a server running Windows Server 2008 R2, we flag the 10 most relevant CVEs. We don’t tag all 500-plus known vulnerabilities for that product. The additional volume wouldn’t change the risk signal. It’s already high.
Some vulnerabilities warrant immediate action. For these, we created FocusTags™—a curated set of CVEs selected for their real-world risk based on exploitability, exposure, and threat actor interest.
For example, in 2024, more than 40,000 CVEs were published.
These tags often overlap with known exploited vulnerabilities—many of which we flagged before public exploitation was confirmed. In certain cases, we used advanced techniques like TLS certificate analysis or favicon hash matching to surface assets that don’t respond to traditional scanning methods.
A note: Black Kite is not a vulnerability scanner. We do not perform authenticated internal scans. Instead, we use OSINT to identify whether systems appear susceptible to known vulnerabilities. Our goal is to measure risk exposure—not confirm exploit paths or patch status.
Yes, the threat landscape is growing more complex. But so are the tools we have to manage it.
We no longer need to chase every vulnerability across every vendor. With the right intelligence, we can take a more targeted, more effective approach. That means better prioritization, smarter remediation, and stronger overall cyber resilience.Want to see what that looks like in practice? Read our full 2025 Supply Chain Vulnerability Report.
Read our full 2025 Supply Chain Vulnerability Report: Navigating a New Era of Managing Vulnerability Risk in Third Parties – accessible instantly, no download required.
The post Why Counting CVEs Misses the Real Third-Party Risk appeared first on Black Kite.
Written by: Ferdi Gül
This week’s Focus Friday highlights four high-priority vulnerabilities affecting widely used enterprise technologies: SysAid On-Premises, Apache ActiveMQ, Webmin, and Couchbase Server. Each of these products serves a critical function—whether facilitating IT service management, message brokering, system administration, or database operations. Their importance makes them prime targets for exploitation, and this week’s disclosures demonstrate both the breadth and depth of third-party risks facing modern enterprises.
From pre-authentication remote code execution in SysAid to denial-of-service vulnerabilities in ActiveMQ, privilege escalation flaws in Webmin, and file disclosure issues in Couchbase, the potential for vendor-side compromise is substantial. This week’s blog dissects these incidents through a Third-Party Risk Management (TPRM) lens and explains how Black Kite’s FocusTags™ empower organizations to swiftly identify which vendors are truly at risk and prioritize outreach accordingly.
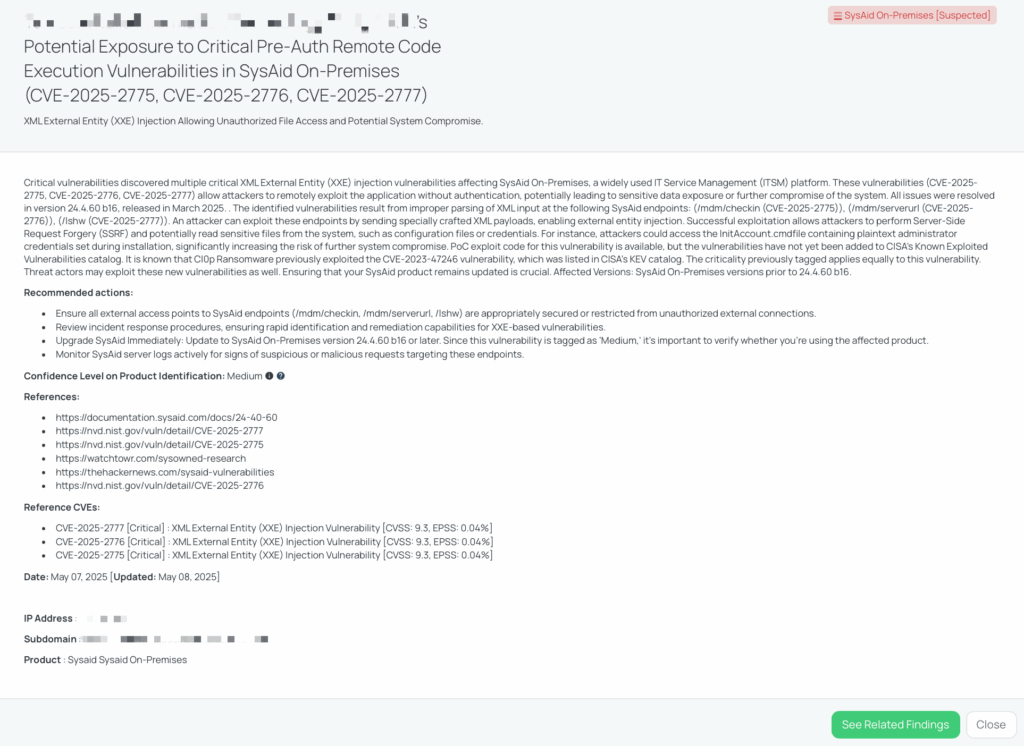
In March 2025, multiple critical pre-authentication XML External Entity (XXE) injection vulnerabilities were disclosed in SysAid On-Premises, a widely used IT Service Management (ITSM) solution. These flaws—CVE-2025-2775, CVE-2025-2776, and CVE-2025-2777—impact the /mdm/checkin, /mdm/serverurl, and /lshw endpoints respectively. Improper XML parsing in these components allows attackers to inject external entities, enabling unauthenticated access to sensitive local files or performing Server-Side Request Forgery (SSRF).
The vulnerabilities are classified as Critical, each carrying a CVSS score of 9.3, although these scores were not officially published at the time of writing. A working Proof-of-Concept (PoC) exploit is publicly available. While these CVEs are not yet listed in CISA’s Known Exploited Vulnerabilities (KEV), historical precedence—such as the exploitation of CVE-2023-47246 by the Cl0p ransomware group—suggests high likelihood of active weaponization.
All three vulnerabilities are patched in SysAid On-Premises version 24.4.60 b16, released in March 2025. Earlier versions remain susceptible, including v23.3.40, the version confirmed to be vulnerable by researchers.
SysAid On-Premises is more than just helpdesk software—it is a business-critical, internet-facing ITSM platform. It manages internal tickets, configuration data, asset inventories, and privileged workflows across an enterprise. As such, any compromise could cascade across multiple internal systems.
The pre-authentication nature of these vulnerabilities significantly lowers the exploitation barrier, especially since one of the attack paths exposes the plaintext administrator password stored in the InitAccount.cmd file. With that credential, attackers gain privileged access to the SysAid environment, and in known exploit chains, this leads to Remote Command Execution (RCE) via a separate post-auth command injection vector.
Vendors using SysAid On-Premises are at elevated risk of compromise through:
These risks multiply when threat actors use the platform as a pivot to access more sensitive parts of a vendor’s network.
Organizations managing third-party risk should direct the following questions to vendors potentially using SysAid On-Premises:
Vendors should take the following remediation steps to mitigate these vulnerabilities:
Black Kite published the SysAid On-Premises [Suspected] FocusTag™ on May 7, 2025, identifying vendors potentially exposed to CVE-2025-2775, CVE-2025-2776, and CVE-2025-2777. The FocusTag enables third-party risk managers to zero in on vendors that are running vulnerable assets, significantly reducing the time required to triage broad vulnerabilities.
The tag includes:
This tag empowers TPRM professionals to focus only on vendors truly at risk, minimizing redundant outreach and enabling faster remediation.
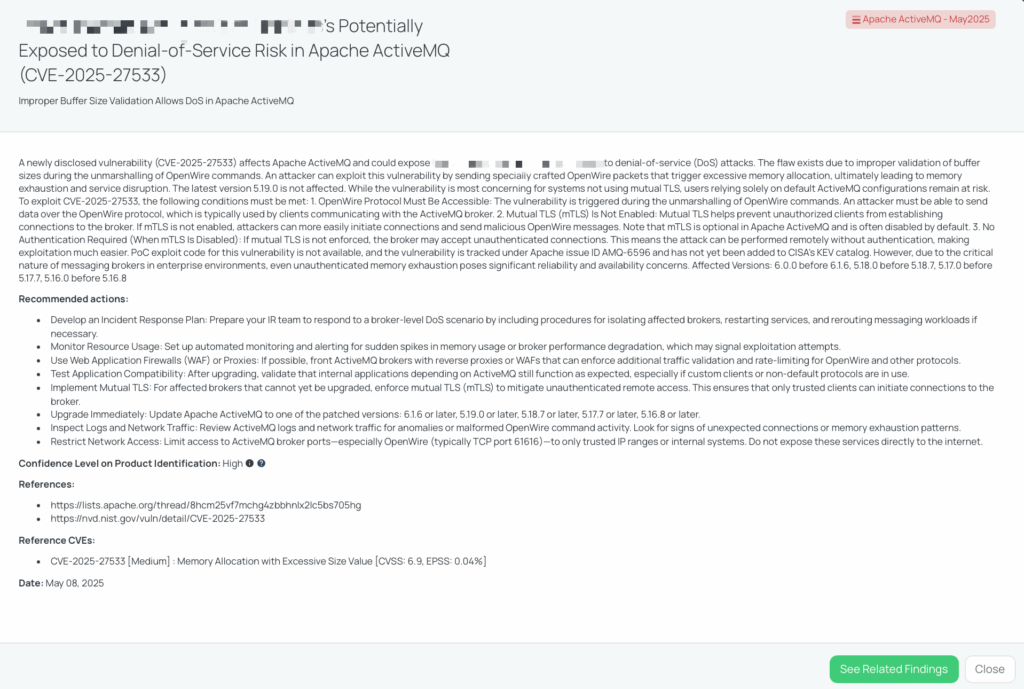
CVE-2025-27533 is a medium-severity vulnerability identified in Apache ActiveMQ, a widely used open-source message broker. The flaw arises from improper validation of buffer sizes during the unmarshalling of OpenWire commands. An attacker can exploit this vulnerability by sending specially crafted OpenWire packets that trigger excessive memory allocation, leading to memory exhaustion and potential denial-of-service (DoS) attacks.
Exploit Conditions for CVE-2025-27533
An attacker can exploit this vulnerability only if all of the following are true:
Although no PoC exploit code is currently available for CVE‑2025‑27533 and it remains tracked under Apache issue AMQ‑6596 without inclusion in CISA’s KEV catalog, its potential for unauthenticated memory‑exhaustion attacks against critical messaging brokers poses a serious reliability and availability risk in enterprise environments.
Apache ActiveMQ serves as a critical component in many enterprise environments, facilitating communication between different applications and systems. A DoS attack exploiting this vulnerability could disrupt business operations, leading to service outages and potential data loss. Furthermore, if mutual TLS (mTLS) is not enabled, attackers can exploit this vulnerability remotely without authentication, increasing the risk of widespread impact.
Black Kite provides continuous monitoring and risk assessment capabilities that can help TPRM professionals identify and manage vulnerabilities like CVE-2025-27533. By leveraging Black Kite’s platform, organizations can:
Black Kite’s FocusTag™ for Apache ActiveMQ – May2025, published on May 8, 2025, offers detailed insights into this vulnerability, including affected versions, mitigation strategies, and monitoring recommendations. TPRM professionals can use this information to engage with vendors, ensure timely patching, and enhance their overall risk management posture.
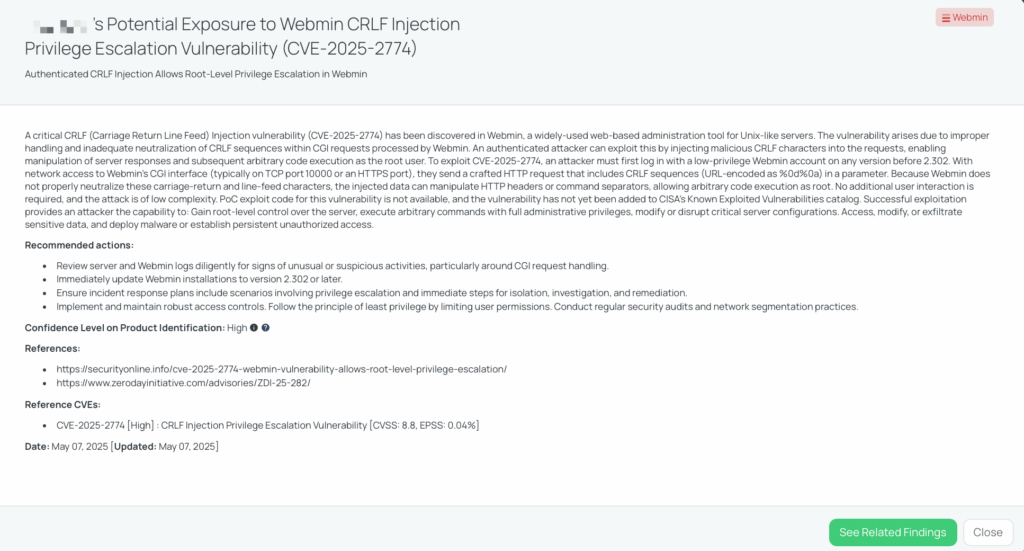
CVE-2025-2774 is a critical CRLF (Carriage Return Line Feed) injection vulnerability affecting Webmin versions prior to 2.302. This flaw arises from improper neutralization of CRLF sequences in CGI request handling, allowing authenticated attackers to manipulate HTTP headers and execute arbitrary code with root privileges. The vulnerability has a CVSS score of 8.8, indicating high severity and low exploit probability.
Discovered and reported to the vendor on February 28, 2025, the vulnerability was publicly disclosed on May 1, 2025. As of now, there is no evidence of exploitation in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities catalog.
Webmin is a widely used web-based system administration tool for Unix-like servers, with over a million installations worldwide. A successful exploit of CVE-2025-2774 could grant attackers root-level access, allowing them to:
Given Webmin’s role in managing critical server functions, this vulnerability poses significant risks to organizations relying on it for system administration.
Black Kite published the FocusTag for CVE-2025-2774 on May 7, 2025. TPRM professionals can utilize Black Kite’s platform to identify vendors potentially affected by this vulnerability. The platform provides asset information, such as IP addresses and subdomains, associated with the vendors’ systems, enabling organizations to assess and manage third-party risks effectively.
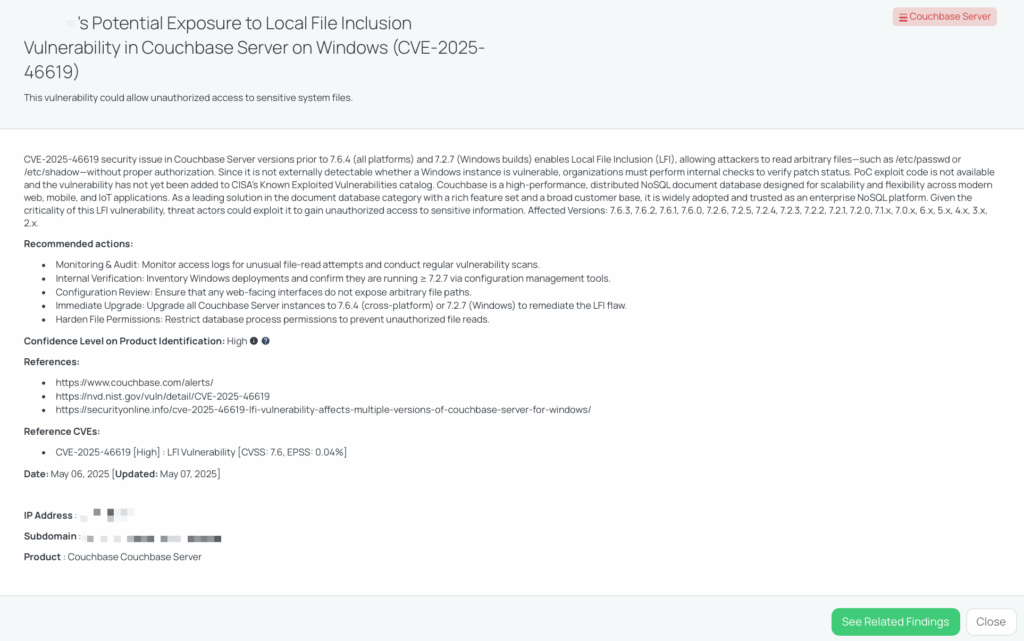
CVE-2025-46619 is a high-severity Local File Inclusion (LFI) vulnerability identified in Couchbase Server versions prior to 7.6.4 (all platforms) and 7.2.7 (Windows builds). Affected Versions are 7.6.3, 7.6.2, 7.6.1, 7.6.0, 7.2.6, 7.2.5, 7.2.4, 7.2.3, 7.2.2, 7.2.1, 7.2.0, 7.1.x, 7.0.x, 6.x, 5.x, 4.x, 3.x, 2.x.
This flaw allows unauthorized users to access sensitive system files, such as /etc/passwd or /etc/shadow, without proper authorization. The vulnerability arises from improper access controls, enabling attackers to read arbitrary files on the server.
The vulnerability was publicly disclosed on April 30, 2025. As of now, there is no evidence of exploitation in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities catalog. The vulnerability’s CVSS score of 7.6 is currently classified as High.
Couchbase Server is a widely-used NoSQL document database, integral to many enterprise applications. Exploitation of CVE-2025-46619 could allow attackers to access sensitive configuration files, leading to potential data breaches or system compromises. Given the prevalence of Couchbase in critical systems, this vulnerability poses a significant risk to organizations relying on it for data management.
Black Kite published the FocusTag™ for CVE-2025-46619 on May 6, 2025. TPRM professionals can utilize Black Kite’s platform to identify vendors potentially affected by this vulnerability. The platform provides asset information, such as IP addresses and subdomains, associated with the vendors’ systems, enabling organizations to assess and manage third-party risks effectively.
In an era where threat actors rapidly pivot to exploit newly disclosed vulnerabilities, organizations need fast, intelligent ways to assess third-party exposure. That’s where Black Kite’s FocusTags™ come into play—especially for critical flaws like those found in SysAid, Apache ActiveMQ, Webmin, and Couchbase Server.
Here’s how Black Kite’s FocusTags™ amplify TPRM efficiency and precision:
With Black Kite’s FocusTags™, your organization is empowered to act swiftly and precisely—not just to understand where exposure exists, but to take meaningful, time-sensitive steps to reduce risk in a constantly evolving threat landscape.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
The post Focus Friday: TPRM Insights Into SysAid, ActiveMQ, Webmin, and Couchbase Server Vulnerabilities appeared first on Black Kite.
Written by: Dr. Ferhat Dikbiyik, Chief Research & Intelligence Officer
From corporate-sounding breach statements to templated negotiations and ESXi support, LockBit blurred the line between cybercrime and customer service — until they were hacked themselves.
If you’ve ever imagined ransomware gangs as chaotic bands of hoodie-wearing hackers launching attacks from the shadows, LockBit would like a word — preferably via encrypted chat, with structured pricing, timezone-aware support, and test decrypts to elp you “experience the product” before buying.
LockBit operates with a surprising level of business sophistication, offering structured pricing, customer support, and even test decrypts. This article details their corporate-like breach announcement after being hacked themselves, their tiered negotiation tactics, and their understanding of enterprise IT environments like ESXi. Ultimately, defenders need to recognize this business-like approach to ransomware in order to better anticipate and prevent future attacks.
After being hacked themselves on May 7, 2025, LockBit released a statement so polished it could’ve been run through a corporate PR team:
“I’m currently investigating how the breach happened and rebuilding the system… no decryptors or any stolen company data were harmed. The full panel and blog are still operational.”
They even offered to pay for intel on the perpetrator (“xoxo” from Prague) — a move eerily reminiscent of a bug bounty program, though they may have just misread a cheeky “hugs and kisses from Prague” sign-off as a hacker’s handle.
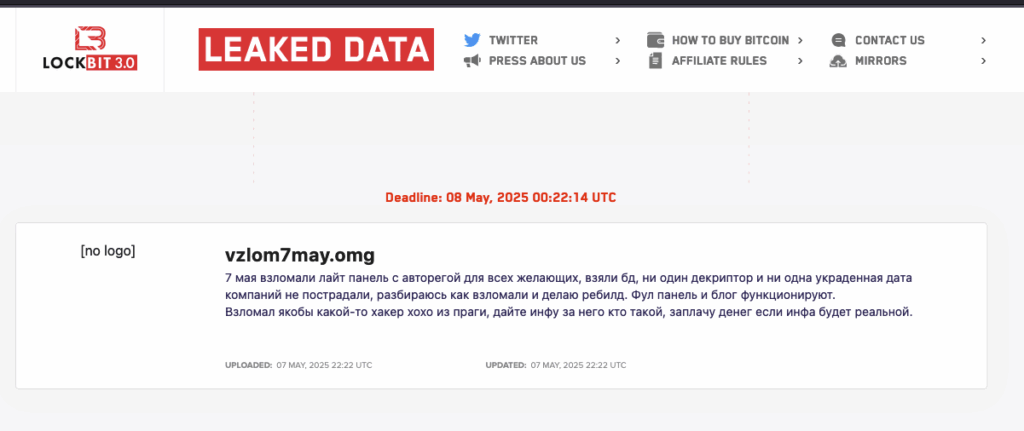
Yes, you read that correctly.
This isn’t just ransomware. It’s ransomware-as-a-business.
And if LockBit had an investor pitch deck, I wouldn’t be surprised if it included growth charts and an affiliate referral program.
But that’s the thing: LockBit wasn’t just a criminal enterprise. It was a business. A brand. A platform.
And just like any startup past its prime, it had structured pricing, technical documentation, customer onboarding…and a spectacular fall.
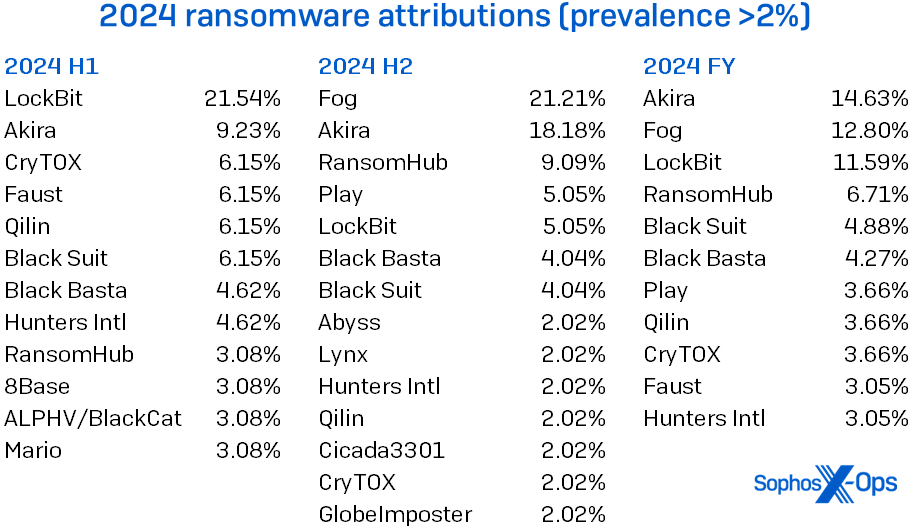
Before Operation Cronos dismantled parts of its infrastructure earlier this year, LockBit was the reigning king of ransomware. They leaked data from over 200 victims per month, supported hundreds of affiliates, and ran a criminal operation with all the polish of a B2B tech firm.
After Cronos, that number dropped to single digits per month. Many affiliates walked away. And when LockBit got breached themselves, the mask slipped, revealing not just their systems, but their business logic.
The leaked negotiation chats read less like ransom demands and more like CRM transcripts.

LockBit’s chats followed a consistent rhythm: name your price, offer a taste, apply pressure, close the deal. Sound familiar?
One small business pleads:
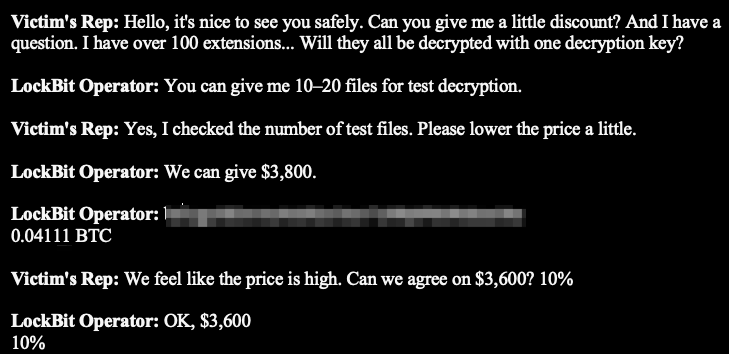
“We feel like the price is high. Can we agree on $3,600?”
LockBit’s response?
“Ok, $3600” (reduced from $4,000)
But after an initial discount, they’re not here for haggling:
“no”
“There will be no more talk about discounts.”
Ransom pricing was neatly aligned with perceived company size:
Total across all negotiations: $767,800
Average ask: $40,410
This isn’t chaos. It’s value-based pricing.
“You can attach a few files for test decryption by packing them into an archive…”
“Please wait for a reply, sometimes it takes several hours due to possible time zone differences.”
These lines appear over and over — clearly copy-pasted.
We’re not dealing with improvisation here. We’re dealing with internal playbooks and canned responses. Like Zendesk, but for extortion.
Need proof that the decryptor works? No problem.
“We can decrypt few random files for FREE.”
“You will need to disable your AV and just run the .exe decryptor.”
That’s not just social engineering. That’s product-led growth.
In one case, a desperate employee begs:
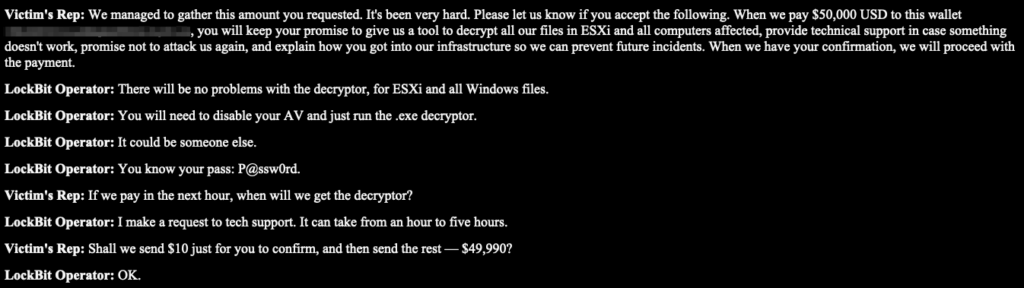
“Please don’t spoil my life… My company will file a case on me… My family will be suffered.”
LockBit replies coldly: “I can’t help you, it’s to end this dialog.”
Elsewhere, they mock:
“You know your pass: P@ssw0rd”
They don’t just threaten. They undermine your confidence.
LockBit tailors its tactics to your environment:
“We found a lot of contact information of your employees, clients, partners…”
“We will try to convey information about the leak to each of these contacts.”
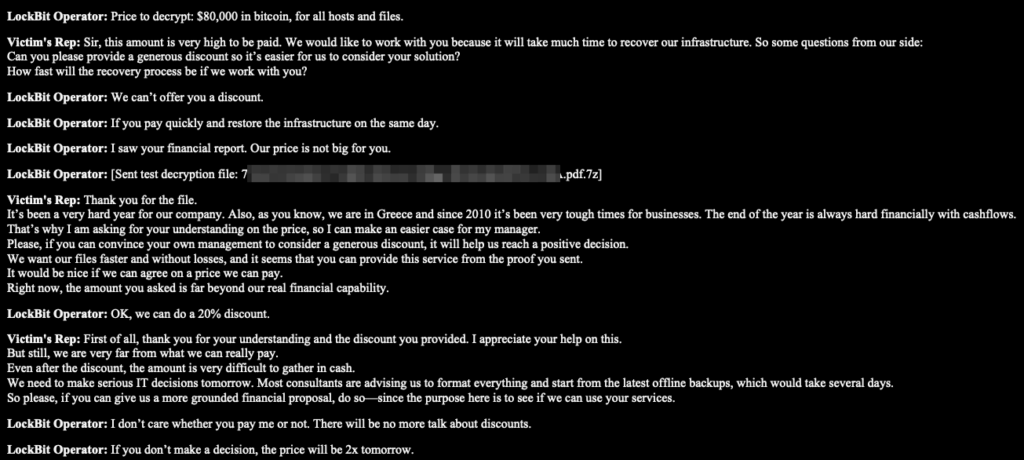
And if you’re rich?
“I saw your financial report. Our price is not big for you.”
“The price…was formed based on the indicators of your company.”
This is market segmentation, but for criminal revenue.
Need to decrypt an ESXi cluster? LockBit’s got you.
“Log in to vCenter, enable SSH, upload decryptor… run ./decrypt… check decrypt.llg log…”
“Do not run multiple decryptors simultaneously… or files may be corrupted.”
We’ve seen fewer steps in vendor documentation.
These actors understand virtualization, backup systems, and endpoint behavior.
This isn’t script kiddie territory. This is ransomware with release notes.
When LockBit got breached, the illusion cracked.
They scrambled to assure “customers” that nothing critical was lost, systems were being rebuilt, and operations were ongoing. The message, minus the extortion and anonymity, would be right at home in an AWS status update.
The offer to pay for intel on “xoxo from Prague” (which again, might’ve just been a sarcastic sign-off) cemented the absurdity: even ransomware groups are vulnerable to phishing and misinterpretation.
They were so committed to acting like a business… they ended up reacting like one too.
So what now?
LockBit may be on the decline, but the playbook they wrote will outlive them. And the next ransomware “startup” will come with better UX, faster support, and cleaner infrastructure.
To stay ahead, we need to:
At Black Kite, we’ve developed tools like the Ransomware Susceptibility Index® (RSI™) and FocusTags™ to help our clients and their vendors stay ahead of this evolution — not just after an incident, but before they become one.
Because if ransomware syndicates are going to act like businesses, it’s time we start treating them like competitors — not just criminals.
Read our full 2025 Supply Chain Vulnerability Report: Navigating a New Era of Managing Vulnerability Risk in Third Parties – accessible instantly, no download required.
The post Your Friendly Neighborhood Ransomware Syndicate Will See You Now appeared first on Black Kite.
Written by: Ferdi Gül
Welcome to this week’s Focus Friday, where we approach the latest critical vulnerabilities through a third-party risk management lens. We begin with SAP NetWeaver Visual Composer’s unauthenticated file upload RCE (CVE-2025-31324), a zero-day actively exploited on over 1,200 servers. Then, we turn to Apache Tomcat’s April 2025 issues—CVE-2025-31650 (HTTP/2 memory-leak DoS) and CVE-2025-31651 (rewrite-rule bypass)—which pose denial-of-service and data-exposure risks. In each section, we’ll outline key details, TPRM-specific questions, and actionable remediation steps, before demonstrating how Black Kite’s FocusTags™ streamline vendor risk identification and response.
This issue is an unauthenticated file-upload flaw in the Metadata Uploader component of SAP NetWeaver Visual Composer (VCFRAMEWORK). Attackers can send crafted POST requests to /developmentserver/metadatauploaderto place JSP, WAR, or JAR payloads on the server, then invoke them via simple GET requests—achieving full remote code execution and system takeover.
It is rated Critical with a CVSS v3.1 base score of 10.0 SAP Support Portal and carries an EPSS score of 55.64%. The National Vulnerability Database first published the CVE on April 24, 2025.
Exploitation in the wild has been observed since at least March 27, 2025, primarily targeting manufacturing environments and deploying webshells such as helper.jsp and cache.jsp. Post-exploit tooling includes Brute Ratel C2 and Heaven’s Gate for stealthy persistence (per FocusTag details).
This CVE was added to CISA’s Known Exploited Vulnerabilities catalog on April 29, 2025. CISA has not issued a separate advisorial beyond the KEV entry.
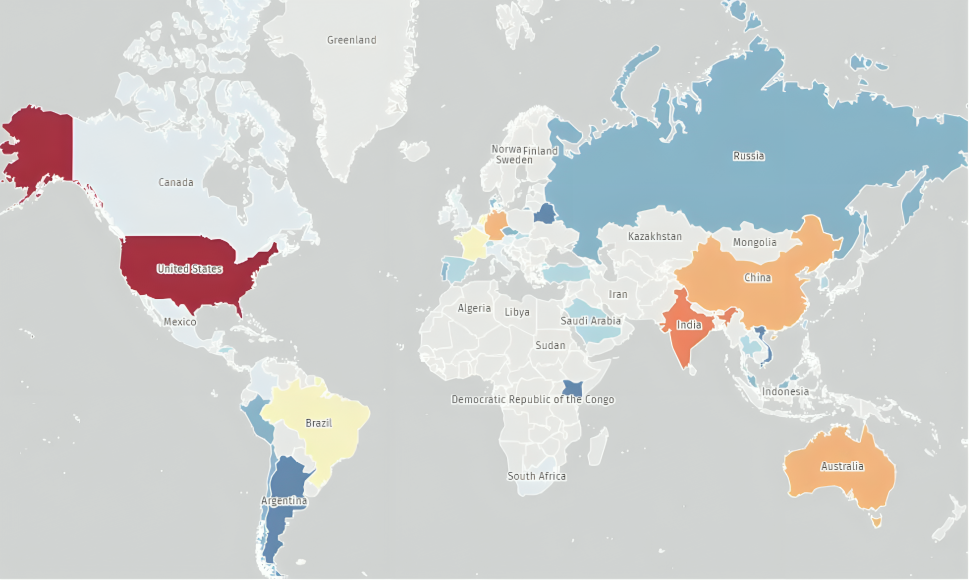
SAP NetWeaver is a widely deployed application server and development platform—often underpinning critical business processes. An unauthenticated RCE in a Visual Composer add-on can lead to full server compromise, unauthorized data access, lateral movement, and supply‐chain ripple effects. TPRM teams must ensure that any third‐party vendors using VCFRAMEWORK have assessed their exposure and applied mitigations promptly to avoid costly incident response and reputational damage.
To assess vendor risk, consider asking:
Vendors should take the following steps immediately:
Black Kite published the SAP NetWeaver VCFRAMEWORK [Suspected] FocusTag on April 29, 2025, highlighting over 1,200 exposed servers and active exploitation trends. Within the Black Kite platform, TPRM teams can:
Drive focused outreach: Narrow questionnaires and assessments to only those vendors with confirmed exposure, reducing vendor fatigue and accelerating risk mitigation.
CVE-2025-31650 is a denial-of-service issue in Tomcat’s HTTP/2 implementation: malformed priority headers lead to incomplete request cleanup, causing a memory leak and eventual server crash. It carries a CVSS v4 score of 8.7 and an EPSS of 0.03%.
CVE-2025-31651 is a rewrite-rule bypass flaw in Tomcat’s RewriteValve: certain percent-encoded paths slip past security rules, exposing JSP shells or confidential files. It has a CVSS v3.1 score of 7.5 and an EPSS of 0.02%.
Both were first published on April 28, 2025 National Vulnerability DatabaseNational Vulnerability Database. Public proof-of-concept code exists for each, but no active exploitation has been reported and neither appears in CISA’s Known Exploited Vulnerabilities catalog.
Apache Tomcat powers countless web applications. A DoS can disrupt critical services and lead to business outages, while a rewrite-rule bypass can expose sensitive data and application logic. In a third-party risk context, vendors running affected versions—even if not compromised—pose material operational and data-exposure risks.
To home in on true exposure, consider asking:
Vendors should:
Black Kite published the “Apache Tomcat – Apr2025” FocusTag on April 30, 2025, highlighting both DoS (CVE-2025-31650) and rewrite-rule bypass (CVE-2025-31651) flaws. Through the platform, TPRM teams can:
Target outreach to only vendors with confirmed exposure, reducing questionnaire overload and speeding mitigation.
Black Kite’s FocusTags™ are essential for transforming raw vulnerability data into TPRM-ready intelligence. With tags for SAP NetWeaver VCFRAMEWORK and Apache Tomcat’s April 2025 flaws, TPRM teams can:
By integrating these FocusTags™ into your TPRM workflow, you gain a data-driven method that accelerates vendor risk reduction and boosts overall supply-chain resilience.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
The post Focus Friday: TPRM Approach to SAP NetWeaver VCFRAMEWORK RCE and Apache Tomcat HTTP/2 DoS and Rewrite-Rule Bypass appeared first on Black Kite.
Written by: Ferdi Gül
Welcome to this week’s Focus Friday, where we spotlight emerging cybersecurity threats through the lens of Third-Party Risk Management (TPRM). As organizations continue to rely heavily on digital ecosystems involving hundreds or thousands of vendors, a single vulnerability in a third-party product can ripple across entire supply chains. This week, we analyze three critical issues affecting high-profile technologies used globally: the exploitation of Fortinet SSL-VPN vulnerabilities through a symlink backdoor, a DoS flaw in SonicWall’s Gen7 SSLVPN interface, and a resource exhaustion vulnerability in Redis servers. Each of these poses unique challenges for TPRM professionals seeking to evaluate vendor exposure and reduce systemic risk.
Through the use of Black Kite’s FocusTags™, organizations can more effectively identify which vendors are likely impacted, prioritize mitigation efforts, and streamline communication. Let’s break down the technical and strategic implications of each threat.
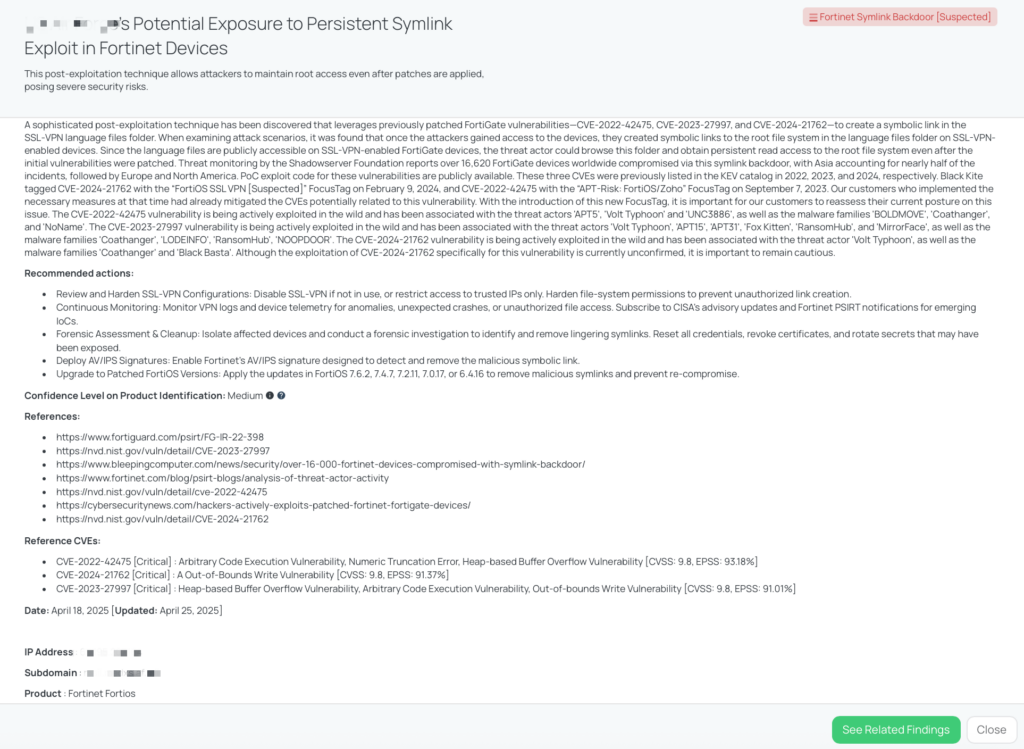
A newly identified post-exploitation method has come to light, which exploits previously patched FortiGate vulnerabilities—CVE‑2022‑42475, CVE‑2023‑27997, and CVE‑2024‑21762. This technique involves the creation of symbolic links within the SSL-VPN language files directory, effectively leveraging access to gain persistent visibility into the root file system. Upon gaining access to a vulnerable FortiGate device, attackers created symbolic links in the public-facing language folder, enabling them to bypass patching efforts and maintain read access to critical system files—even after the original flaws had been remediated.
According to telemetry from the Shadowserver Foundation, over 16,620 FortiGate devices across the globe have been compromised through this symlink backdoor. The majority of these cases are concentrated in Asia, followed by Europe and North America.
Proof-of-concept exploit code for the related vulnerabilities is readily available online. All three CVEs involved were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog in 2022, 2023, and 2024, reflecting their known exploitation in real-world attacks. Notably, Black Kite previously issued FocusTags™ for two of these vulnerabilities: CVE‑2024‑21762 was tagged with the “FortiOS SSL VPN [Suspected]” label on February 9, 2024, while CVE‑2022‑42475 was covered under the “APT‑Risk: FortiOS/Zoho” tag on September 7, 2023. Customers who responded to those alerts likely addressed the underlying vulnerabilities proactively. However, this newly emerged post-exploitation technique warrants renewed attention.
Each of these vulnerabilities is known to be actively exploited in the wild. CVE-2022-42475 has been linked to APT5, Volt Typhoon, and UNC3886, and associated with malware families such as BOLDMOVE, Coathanger, and NoName. CVE-2023-27997 has been exploited by Volt Typhoon, APT15, APT31, Fox Kitten, RansomHub, and MirrorFace, with related malware including Coathanger, LODEINFO, NOOPDOOR, and RansomHub. CVE-2024-21762 has also seen confirmed exploitation by Volt Typhoon, often using the Coathanger and Black Basta malware families. While there is no confirmed proof that CVE-2024-21762 was directly used to plant this specific symlink backdoor, its exploitation remains highly probable and cannot be ruled out.
CISA added CVE-2023-27997 to its Known Exploited Vulnerabilities (KEV) catalog on June 13, 2023, and CVE-2024-21762 on February 9, 2024 . CVE-2022-42475 has also been associated with nation-state threat actors.
FortiGate devices are widely used for network security, including firewall and VPN functionalities. A compromised FortiGate device within a vendor’s infrastructure can lead to unauthorized access to sensitive data, configuration files, and network traffic. This persistent access poses significant risks, including data breaches and lateral movement within networks.
To assess the risk associated with this backdoor, consider asking vendors the following questions:
Vendors should take the following actions to mitigate the risk associated with the Fortinet Symlink Backdoor:
Black Kite provides a FocusTag for the Fortinet Symlink Backdoor, enabling organizations to identify vendors potentially affected by this issue. The FocusTag includes detailed information about the associated vulnerabilities, affected assets, and remediation guidance. By utilizing this FocusTag, TPRM professionals can prioritize their risk assessments, focusing on vendors with known exposures, and facilitate targeted remediation efforts.
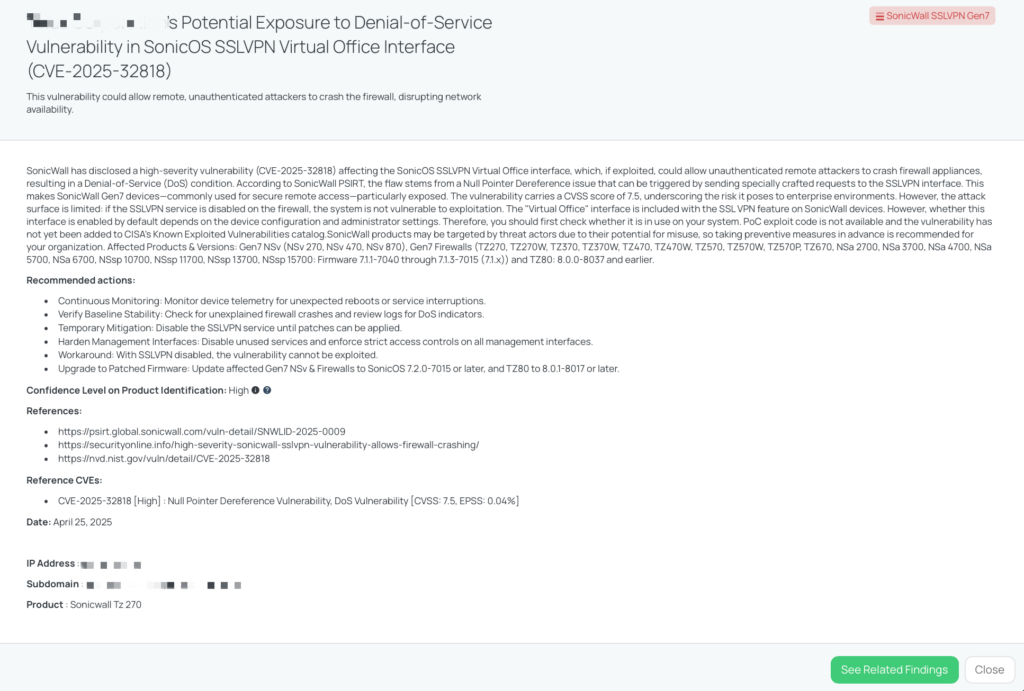
CVE-2025-32818 is a high-severity vulnerability impacting the SonicWall SonicOS SSLVPN Virtual Office interface, identified as a Null Pointer Dereference issue. This flaw allows unauthenticated remote attackers to crash the firewall, leading to a Denial-of-Service (DoS) condition. The vulnerability affects Gen7 firewall models and NSv platforms running firmware versions 7.1.1-7040 through 7.1.3-7015, and TZ80 models on version 8.0.0-8037 or earlier.
Disclosed publicly on April 23, 2025, by SonicWall PSIRT (Advisory ID: SNWLID-2025-0009), the vulnerability has a CVSS v3 score of 7.5 and an EPSS score of 0.04%. It is exploitable only if the SSLVPN service is enabled. While proof-of-concept exploit code is not yet publicly available, and the issue is not included in CISA’s Known Exploited Vulnerabilities catalog, proactive mitigation is strongly encouraged. Given the firewall’s critical role in securing remote access, any disruption to its availability can impact business continuity.
SonicWall Gen7 devices are widely deployed by vendors for secure remote access. These devices protect sensitive traffic through their SSLVPN services, and a crash of such a firewall can mean sudden loss of remote connectivity, disruption of business-critical workflows, and exposure to further compromise during downtime. Even though this vulnerability does not allow code execution or data exfiltration directly, it can be weaponized for targeted service disruption—especially in organizations that rely on 24/7 availability.
From a third-party risk perspective, a vendor with vulnerable or improperly configured SonicWall devices may lose access to essential services or fail to meet service-level agreements (SLAs). If exploited during an incident, the firewall’s unavailability can also delay incident response or containment activities.
To better understand vendor exposure and readiness, consider asking:
Vendors using SonicWall SSLVPN Gen7 appliances should take the following remediation steps:
Black Kite published the SonicWall SSLVPN Gen7 FocusTag on April 25, 2025, enabling TPRM teams to pinpoint vendors potentially exposed to CVE-2025-32818. This tag provides asset-level visibility, including IP addresses and service banners that indicate the presence of vulnerable configurations.
By using this FocusTag, risk managers can prioritize outreach to vendors actively running impacted SonicWall models and validate whether they’ve implemented mitigation steps. If a vendor has SonicWall SSLVPN publicly exposed, the tag surfaces this directly, significantly reducing the scope of your due diligence efforts.
This tag is especially useful for organizations relying on multiple vendors that use SonicWall for remote access, helping you rapidly assess operational impact and contain downstream availability risks before they escalate.
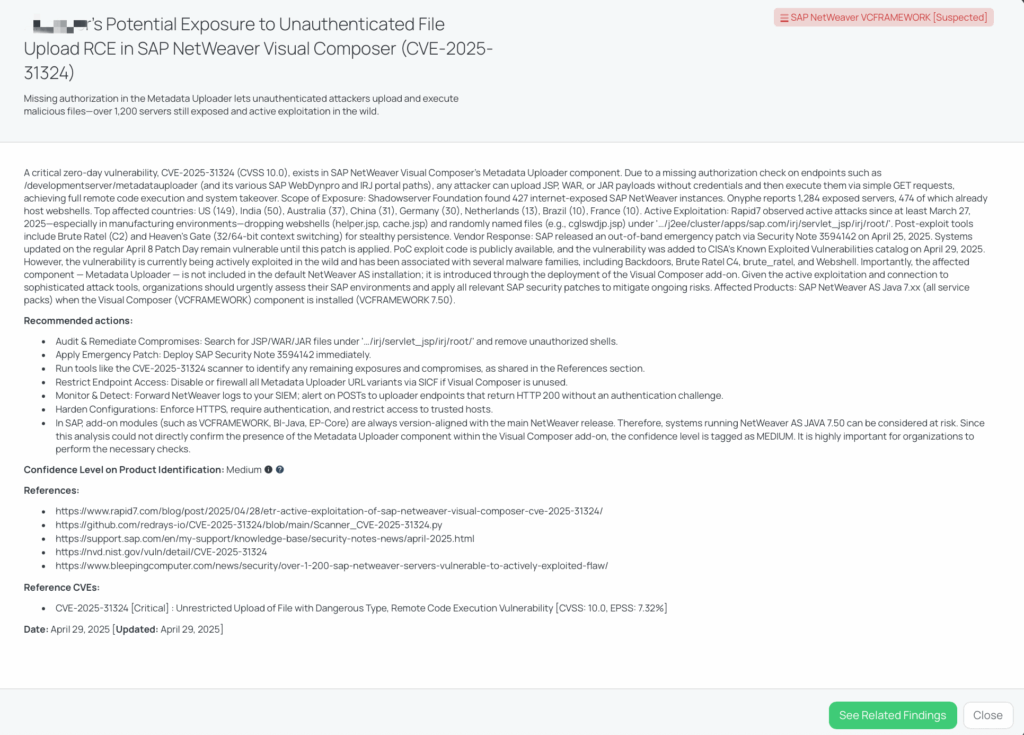
CVE-2025-21605 is a high-severity Denial-of-Service (DoS) vulnerability impacting Redis servers. The flaw arises due to unlimited growth of output buffers, caused by an unauthenticated client sending commands or triggering repeated “NOAUTH” responses when password authentication is enabled. If exploited, the Redis server’s memory can be completely exhausted, causing the service to crash. This vulnerability carries a CVSS v3 score of 7.5 and an EPSS score of 0.04%.
First publicly disclosed on April 23, 2025, via GitHub Security Advisories (GHSA-r67f-p999-2gff), the issue affects Redis versions from 2.6 up to but not including 7.4.3. Although no proof-of-concept exploit code is publicly available at this time, Redis’s widespread deployment in production environments elevates the concern. As of today, CVE-2025-21605 has not been added to CISA’s Known Exploited Vulnerabilities catalog, and no advisory has been released by CISA.
Redis maintainers have addressed this vulnerability in Redis 7.4.3, where sensible client output buffer limits have been introduced.
Redis servers are commonly used to cache critical application data, manage sessions, and handle real-time information. A service crash triggered by an unauthenticated client could lead to serious disruption in vendor environments, including website outages, application failures, and business process interruptions.
From a TPRM perspective, any vendor relying on exposed or improperly secured Redis instances is at risk of operational downtime without advance warning. In environments where Redis clusters are part of larger SaaS offerings or critical backend systems, a DoS incident could cascade across dependent systems, impacting availability and client trust. Given that Redis by default does not restrict output buffer growth for normal clients, vendors who have not proactively hardened their Redis configurations may be vulnerable.
To assess third-party exposure related to this Redis vulnerability, consider asking:
Vendors should adopt the following mitigation and remediation strategies:
Black Kite released the Redis Server FocusTag on April 23, 2025, allowing organizations to quickly identify vendors potentially exposed to CVE-2025-21605. By using this FocusTag, TPRM teams can pinpoint companies operating vulnerable Redis versions or improperly configured instances that may be susceptible to DoS attacks.
The FocusTag enriches risk assessments by providing asset-level intelligence such as IP addresses and relevant service information. With this insight, TPRM professionals can prioritize outreach and remediation requests, ensuring that critical third-party partners address the vulnerability before it leads to business disruption.
In environments where Redis plays a pivotal backend role, using Black Kite’s FocusTags™ ensures that availability risks are proactively managed, rather than discovered during an unexpected service failure.

The vulnerabilities explored in this week’s Focus Friday—ranging from backdoor persistence via patched Fortinet SSL-VPN flaws, to denial-of-service conditions in SonicWall appliances and Redis servers—highlight the diverse and evolving nature of third-party cybersecurity risk. In environments where availability, remote access security, and in-memory data handling are mission-critical, even a single overlooked CVE can introduce severe operational and reputational damage.
Black Kite’s FocusTags™ empower TPRM teams to tackle this complexity head-on with:
With threats targeting everything from network edge devices to internal caching systems, Black Kite’s FocusTags™ offer a powerful lens to see where exposure lies, how to address it, and how to prioritize what matters most—before incidents escalate.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
https://nvd.nist.gov/vuln/detail/CVE-2024-21762
https://nvd.nist.gov/vuln/detail/CVE-2023-27997
https://nvd.nist.gov/vuln/detail/cve-2022-42475
https://cybersecuritynews.com/hackers-actively-exploits-patched-fortinet-fortigate-devices
https://www.fortiguard.com/psirt/FG-IR-22-398
https://nvd.nist.gov/vuln/detail/CVE-2025-32818
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2025-0009
https://securityonline.info/high-severity-sonicwall-sslvpn-vulnerability-allows-firewall-crashing
https://nvd.nist.gov/vuln/detail/CVE-2025-21605
https://github.com/redis/redis/security/advisories/GHSA-r67f-p999-2gff
The post Focus Friday: TPRM Insights Into Fortinet Backdoors, SonicWall SSLVPN, and Redis DoS Vulnerabilities appeared first on Black Kite.