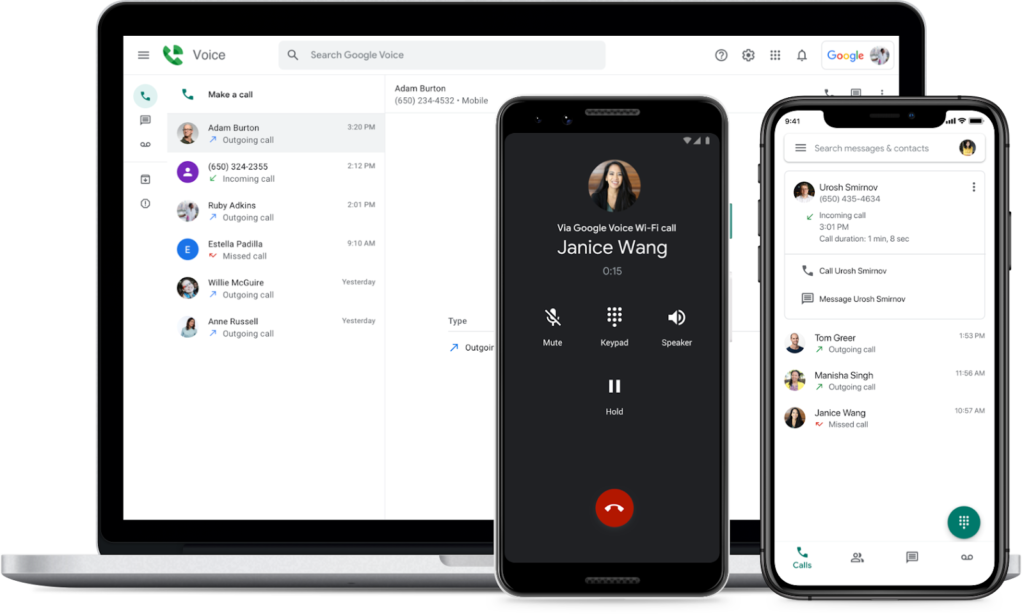
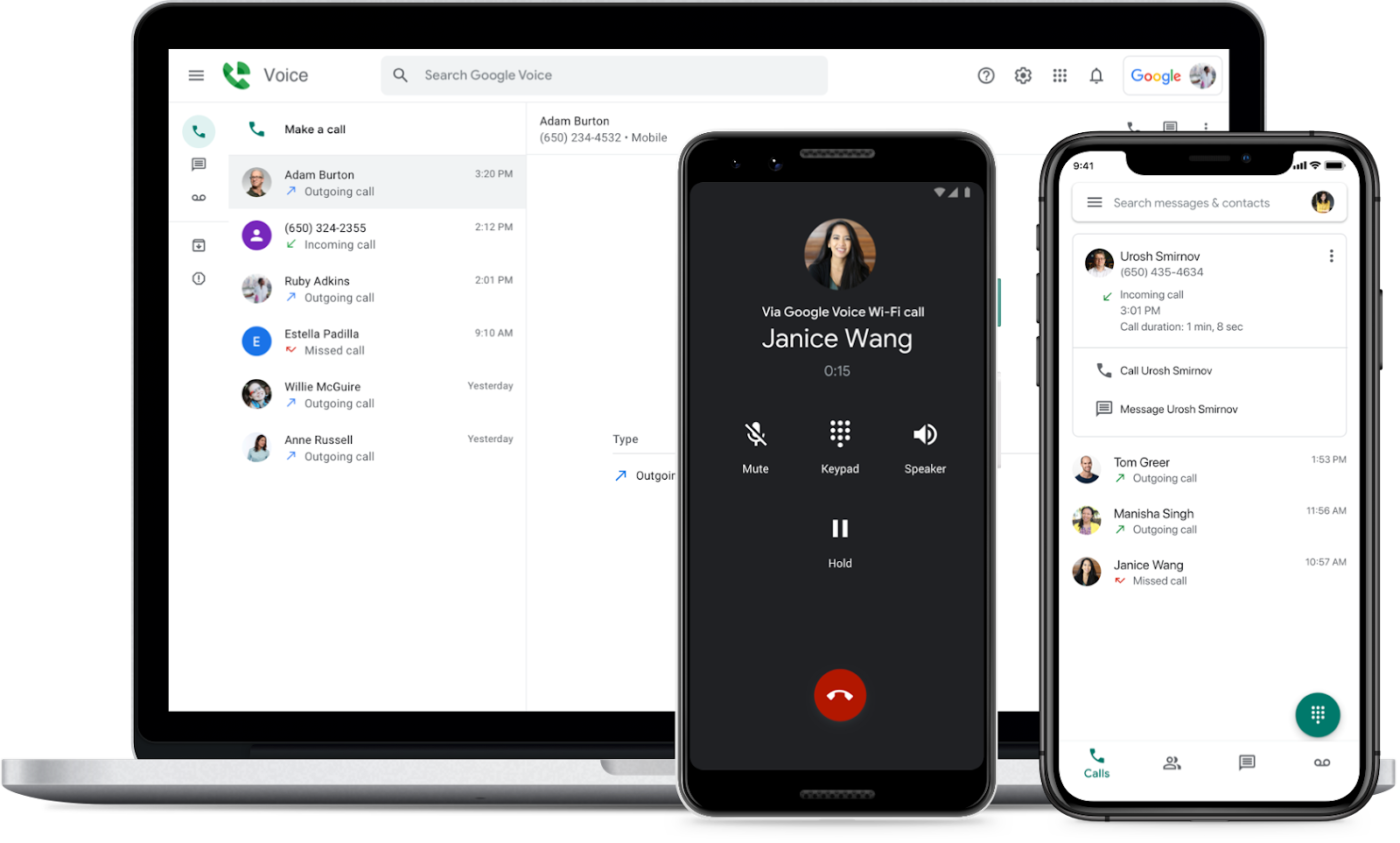
The Best Android POS Systems
Over the years, I’ve seen Android POS systems evolve into some of the most adaptable and accessible business tools on the market. Today’s Android POS offers straightforward setup, seamless connectivity, and compatibility with most smart devices, making it appealing to both new entrepreneurs and seasoned business owners.
Here are my recommendations for the best Android POS systems of 2024:
Note that all providers on this list are highly rated on Google Play by real life users and compatible with most Android POS hardware.
For this guide, my research focused on your top-of-mind concerns, such as overall value-for-money, scalability, and user experience. I developed a rubric that evaluated pricing, management tools, register features, support and reliability, and user experience.
Here are the specific categories and criteria I considered:
- Pricing (15%): Upfront and monthly POS and hardware costs, as well as overall pricing transparency.
- Management tools (25%): Durability, integrations, and core functionality.
- Register features (25%): How efficiently the POS software and hardware work together to process transactions, manage employee access, update inventory, and track transactions.
- Support & reliability (10%): Hardware availability, software customer support, system reliability, onboarding & training, and offline transaction processing.
- User experience (25%): POS software review score on Google Play, as well as ease of use and setup, mobility, and transparency of information on the provider’s website.
I then put together a shortlist of 12 popular Android POS system providers to consider.
- Square
- PayPal Zettle
- Helcim
- SumUp
- Shopify POS
- Vagaro
- Toast
- SpotOn
- eHopper
- Lightspeed Retail
- CloverGo
- Loyverse
Each criteria focuses primarily on maximizing the benefits of Android OS to business systems, so the scores will highlight which POS provider offers the most compatibility and best value-for-money. The result is my five best Android POS system recommendations that cover different use cases and business requirements.
Please note: While I worked extensively to include all significant aspects of Android POS system functionality, my analysis is based on current relevant POS and hardware features, which can change over time. To consistently provide the best answer, this buyers guide will be regularly updated to reflect both industry standards and provider system upgrades.
My recommendations for Android POS systems are based on more than 7 years of evaluating POS software and hardware across different industries and business types. To score each one, I tested the POS software (when possible), reviewed hardware specifications, and gathered feedback from real-life users. I also considered payment processing options and available integrations to gauge the scalability of each system.
Best Android POS systems compared
Our Score (out of 5)
Software Plan Starts at
POS Software on
Compatible POS Hardware Add-Ons
Payment Processing Options

Square
4.37
$0
Android Smartphone/Tablets
Square mobile card reader, Square & third-party peripherals*
In-house

Loyverse
4.31
$0
Android Smartphone/Tablets, Third-party Android POS Hardware
Third-party mobile card reader and peripherals
Third party integrations

Shopify
4.22
$5
Shopify Tablet Stand, Android Smartphone/Tablets
Shopify mobile card reader, Shopify & third-party peripherals
In-house

Clover
4.19
$14.95
Android Smartphone/Tablets
Clover mobile card reader, third-party peripherals
In-house or reseller

Vagaro
4.12
$30
Vagaro Tablet Stand, Android Smartphone/Tablets
Vagaro mobile card reader, Vagaro peripherals
In-house
* Such as barcode scanners, cash registers, receipt printers, weighing scales, customer display, and kitchen display systems that run on an Android operating system.
Did you know? The Android operating system (OS) is built on an open-source platform that developers use to create proprietary business systems. So, there are many POS software that run on Android. For example, the popular restaurant POS software Toast is Android-based, though you can’t download the software for free on Google Play.
Many POS hardware peripherals are also built using the Android OS and are, by default, compatible with any POS software that runs on an Android device.
Read more: Types of POS systems

Square: Best overall (best value for small and new businesses)
Overall Score
4.37/5
Pricing
5/5
Management tools
3.96/5
Register features
4.58/5
Support & reliability
4.06/5
User experience
4.32/5
Pros
- Best value
- Free POS plan
- Industry-specific POS software
- Native ecommerce platform
- Fast and easy set up
Cons
- Tied to Square payment processor
- iOS version is rated higher
- Limited support hours
Why I chose Square Android POS
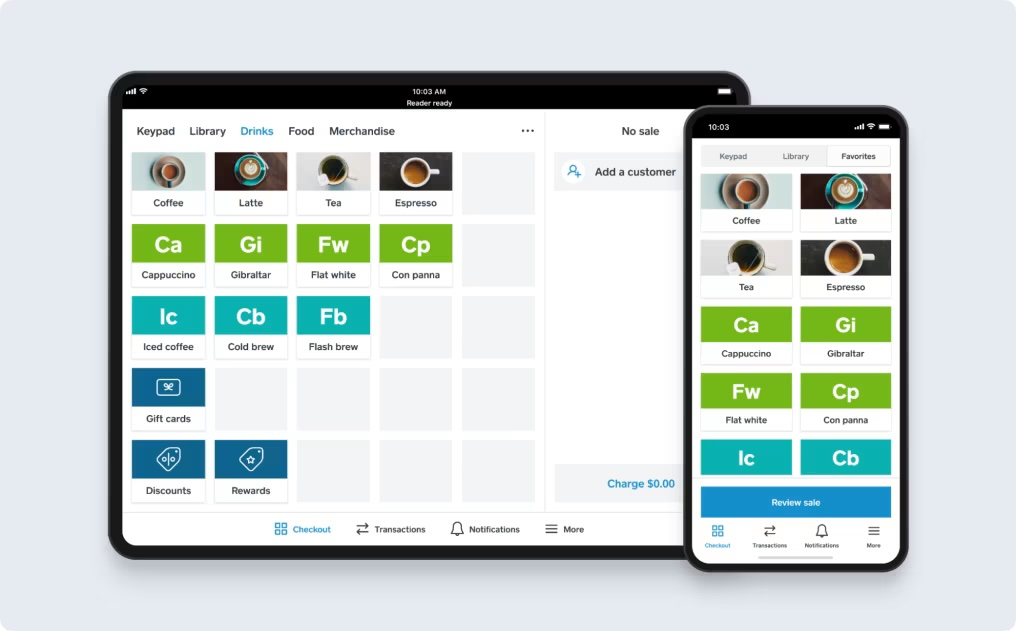
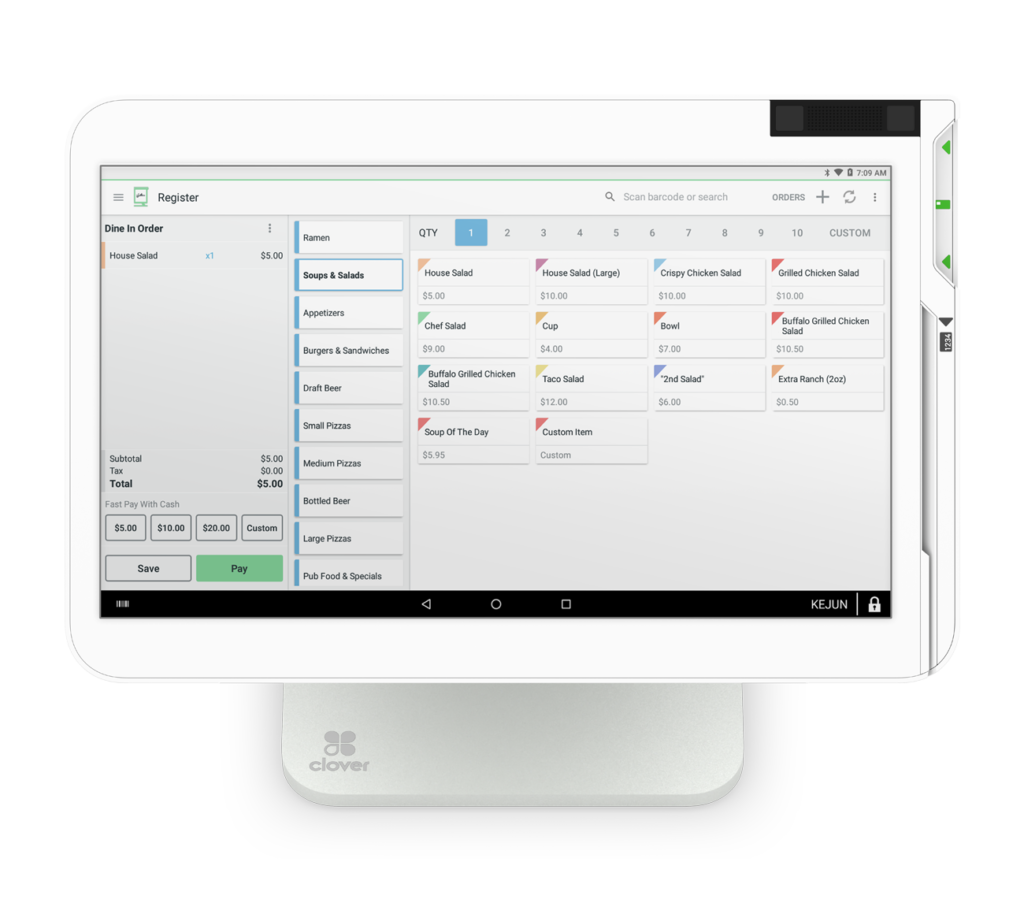
Launched in 2009, Square is one of the first POS providers to harness the power of mobile software for a payment app. And to this day, its mobile software is among the most highly rated in both Apple Apps and Google Play. Square is well known for its ease of setup and ease of use, primarily because of its mobile deployment.
What I like most about Square is that it provides the most feature-rich all-in-one POS system of all the providers on our list, allowing small and new businesses, even those on a tight budget, to get started with little upfront cost. You can download Square’s Android POS app for free on Google Play, sign up for an account, and set up your store on your smartphone or tablet. You also get a free magstripe reader to connect to the app, but you can also manually enter payments right into the app.
I recommend Square if you want to launch your business with minimum fuss. Note that as your business grows, you will eventually want to sign up for a paid Square plan to upgrade your business management tools. You will also need to purchase hardware adaptors to keep using your Android tablet with Square’s barcode scanners and cash drawers.
Related: What is Square
- Monthly account fee: $0–$89 (includes POS software)
- In-person transaction fee: 2.6% + $0.10
- Online transaction fee: 2.9% + $0.30
- Keyed-in transaction fee: 3.5% + $0.15
- Custom pricing: Sales volume greater than $250,000 annually
- Virtual terminal fee: $0
- Chargeback fee: Waived up to $250/month
- Hardware cost: $0–$299
- Application/set up fee: $0
- Cancellation fee: $0
All Square users receive a free magstripe reader for swipe card payments.
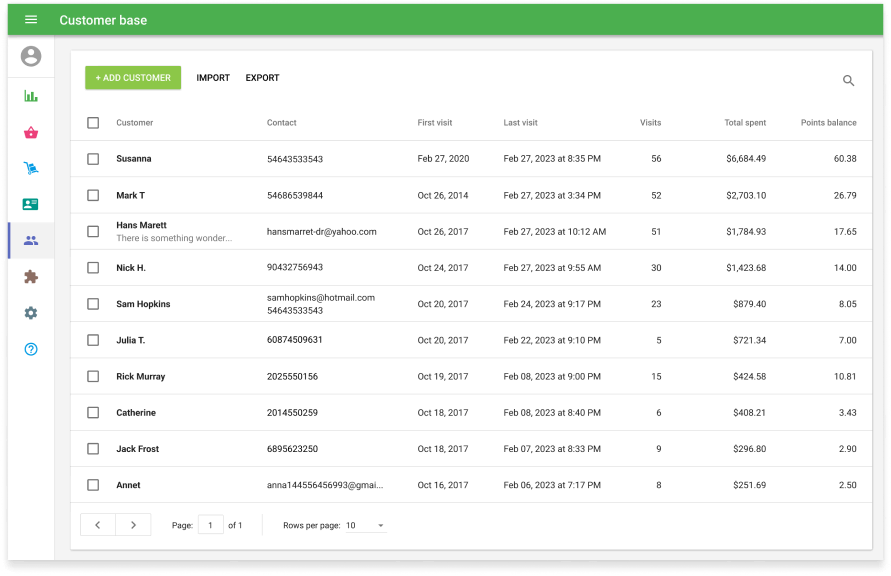
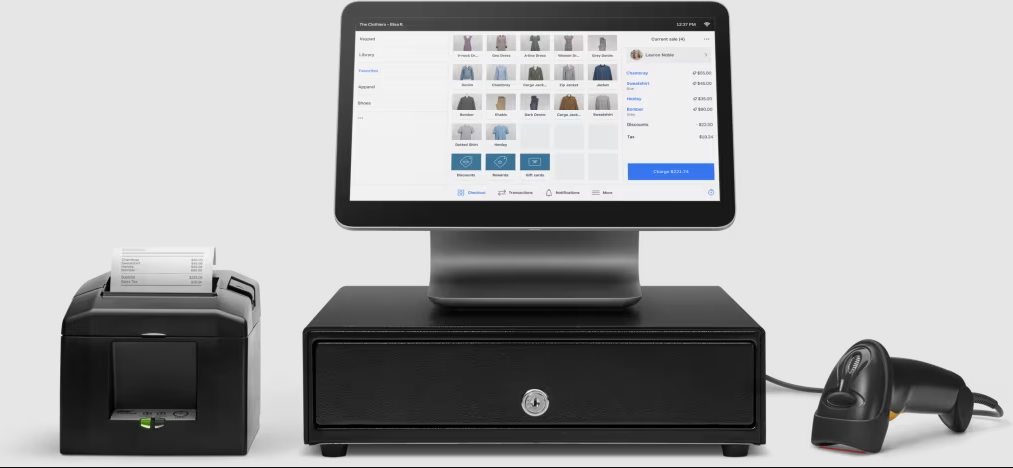
Android POS app: The Square mobile POS app is available for Android devices and can connect seamlessly with Square’s mobile credit card readers. Square is the most reviewed POS software in our list, scoring 4.1 out of 5 from around 233,000 reviews on Google Play
Android POS hardware: You can run the Square POS app on any Android smartphone or tablet and connect it to a Square magstripe and/or contactless mobile card readers. The magstripe reader (first is free) is separate from the contactless and accepts all types of in-person payment methods, including tap-to-pay on iPhone.
Supported Android hardware accessories: To complete your POS set up, connect your Android tablet to Square’s USB receipt printers, receipt printers with Ethernet interface, Impact kitchen ticket printer, barcode scanner (with a USB OTG adaptor), cash drawer (with a USB OTG adaptor). You can also choose from Square’s long list of third-party POS hardware peripherals.
Free all-in-one POS plan: Square offers the most comprehensive free POS plan with industry-specific software, ecommerce platform, payments, and even a magstripe reader included.
Free online store: Square’s basic website builder is free and easy to use. It features drag-and-drop functions for setting up every page of your website. You can also integrate your website with social media platforms such as Instagram, Facebook, and Google product listings.
Native payment processor: Each Square account comes with a built-in payment processor, Square Payments, which offers simple flat rate fees and waived chargeback claims up to $250 per month. No additional monthly fee or application process is required to set up a merchant account.

Loyverse: Best for quick-service restaurants and food retailers
Overall Score
4.31/5
Pricing
4.69/5
Management tools
3.96/5
Register features
4.38/5
Support & reliability
4.06/5
User experience
4.48/5
Pros
- Flexible payment processing options
- Wide range of complete Android POS hardware
- Free and affordable POS software plan
- High ratings from real-life Android users
Cons
- 24/7 support for paid plan users
- Will have to purchase hardware separately
- Add on monthly fee to access integrations
Why I chose Loyverse’s Android POS
Loyverse (Loyalty Universe) started in 2014, developing app-based POS software for various industries but with a particular focus on restaurant needs. The system is compatible with both iOS and Android operating software, making it a versatile and user-friendly option. While most experts recommend Loyverse for quick-service restaurants, I also find the system very useful for food-based retailers.
Loyverse comes in a close second on this list, and with good reason. Compared to Square, Loyverse offers more flexibility with your choice of payment processor and hardware. I love that Loyverse allows you to choose between an Android tablet stand setup and a complete Android POS terminal, so it fits any type of budget. Best of all, its free basic POS software already comes with a built-in kitchen display system (KDS) and loyalty features, which would cost you extra when using popular POS alternatives like Square
In addition to the free kitchen display system and loyalty features, Loyverse’s advanced inventory management features for restaurants also offer better value. Around 14,000 Android users on Google Play scored Loyverse significantly higher than Square.
That said, Loyverse does come with a few trade-offs. For one, the company lists recommended hardware on the website but doesn’t offer any assistance in purchasing. Nor does Loyverse help you sign up with a payment processor (though the website can redirect you to a Loyverse-SumUp landing page to apply for a merchant account).
What’s more, since you are purchasing hardware and your merchant account through other vendors, that means customer and technical support for those services will also be through those other vendors, and not Loyerse. This lack of seamlessness cost Loyverse points for ease of use and setup.
Related: Best Free POS systems
Software plans:
- Monthly basic POS software: $0/month
- Advanced inventory management: $25/month (14-day free trial)
- Access to integrations: $9/month
- Employee management: $5/month per employee
- 24/7 customer support: for customers with a paid plan
Payment processor options:
- SumUp card reader: $54 fast set up, zero monthly fee, no long-term contracts
- PayPal Zettle card reader: $79 (first card reader discounted at $29), fast set up, zero monthly fee, no long-term contracts
Please note: Loyverse does not sell POS hardware directly.
Android POS app: The Loyverse POS app is free to download and compatible with both iOS and Android OS. The free basic software comes with a customer display, KDS, and loyalty program. It is the highest-rated Android POS app in our list, with a score of 4.9 out of 5 from around 14,000 reviews on Google Play
Android POS hardware: You can run the Loyverse POS software on any Android-based smart device and set it up on third-party tablet stands. Alternatively, you can opt for a Loyverse-supported Android-based POS terminal (Sunmi, Bematech, and iMin). Loyverse also supports integrated third-party payment processors that offer compatible mobile card readers.
Supported Android hardware accessories: To complete your countertop POS set up, Loyverse offers a list of compatible Android-based receipt printers, label printers, barcode and ID scanners, scales, and cash drawers.
Flexible payment processing: Loyverse allows you to choose from among its third-party payment processing partners. For US and Canada-based merchants, Loyverse works with SumUp and PayPal, which offer low rates, zero monthly fees, no long-term contracts, and fast setup.
Advanced inventory management features: Loyverse’s advanced inventory management tools provide robust product tracking features that restaurants and food-based retailers need, such as expiry date and bottle deposit tracking, mobile inventory count, and stock transfers. Purchase and vendor management is also included.
Loyalty program: Loyverse offers free loyalty program features that allow you to create custom loyalty and rewards programs. You can even create loyalty cards with unique barcodes that customers can present at the checkout counter.
Ecommerce integrations: Loyverse integrates with a number of website platforms, including the popular WooCommerce and Shopify. These integrations, in turn, give you access to numerous local delivery and shopping apps.

Shopify POS: Best for omnichannel point of sale
Overall Score
4.22/5
Pricing
4.38/5
Management tools
4.17/5
Register features
4.58/5
Support & reliability
3.13/5
User experience
4.26/5
Pros
- Strong omnichannel features
- Full Android POS hardware setup
- Smart inventory tools
- Free POS software
Cons
- Connectivity issues for Android users
- Limited offline mode capabilities
- High transaction fees for basic POS plan
Why I chose Shopify’s Android POS
Launched in 2006, today, Shopify has around 5.6 million active stores worldwide, making it one of the top multi-channel POS providers on the market today. Like Square and Loyverse, it offers free mobile-based POS software for iOS and Android users.
There are two things that I like most about Shopify. First, its omnichannel features are top-notch. It provides everything you need to sell products on multiple channels (including social media platforms). And, it includes native local delivery and shipping functionalities.
Second, it offers tablet stands that support both iOS and Android systems. Square, on the other hand, only offers an iPad stand. Other POS hardware accessories are also available directly from Shopify, so you can build an Android-based POS countertop setup without having to deal with third-party resellers.
Note, however, that transaction rates for Shopify’s Starter POS plan ($5/month) are nearly twice the processing fee of the higher Retail plan ($89/month). Both allow you to sell in-person and online, but the Retail plan offers a better value with advanced inventory features, lower processing fees, and multichannel selling tools.
Related: Best tablet POS systems
- Monthly fee:
- Starter plan: $5/month
- Retail plan: $89/month
You can also opt for an ecommerce plan from $29 per month, which includes the basic Shopify POS.
- Transaction fees: Starter plan
- In-person: 5%
- Online: 5% + 30 cents
- Transaction fees: Retail plan
- In-person: 2.6% + 10 cents
- Online: 2.9% + 30 cents
- Chargeback fee: $15
- Hardware: From $49
Android POS app: Over 500,000 users have downloaded Shopify’s Android POS app. With its omnichannel features, your sales, inventory, and customer data are updated in real time. While it has historically above-average reviews, many users claim that the app’s May 2024 update has been causing connectivity issues. The app is currently rated 3.5 out of 5 from over 2,400 reviews.
Android POS hardware: You can download Shopify’s POS app on a smartphone and connect it to a mobile credit card reader for a mobile setup. Alternatively, Shopify also supports tablet stands for Android that you can connect to the mobile card reader or payment terminal.
Supported Android hardware accessories: Shopify also sells POS peripherals, receipt printers, label printers, barcode and ID scanners, and cash drawers to add to your tablet stand for a countertop setup.
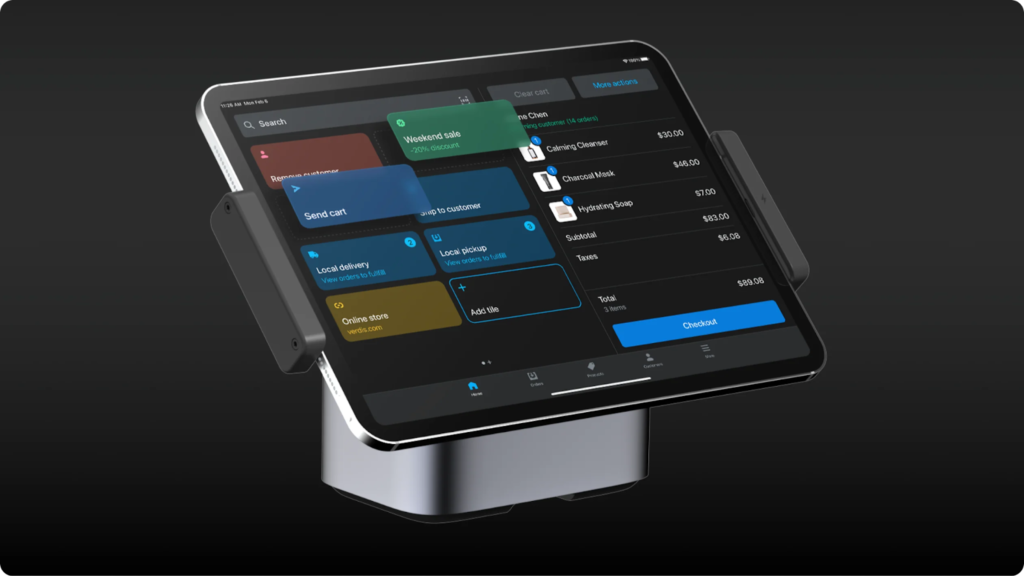
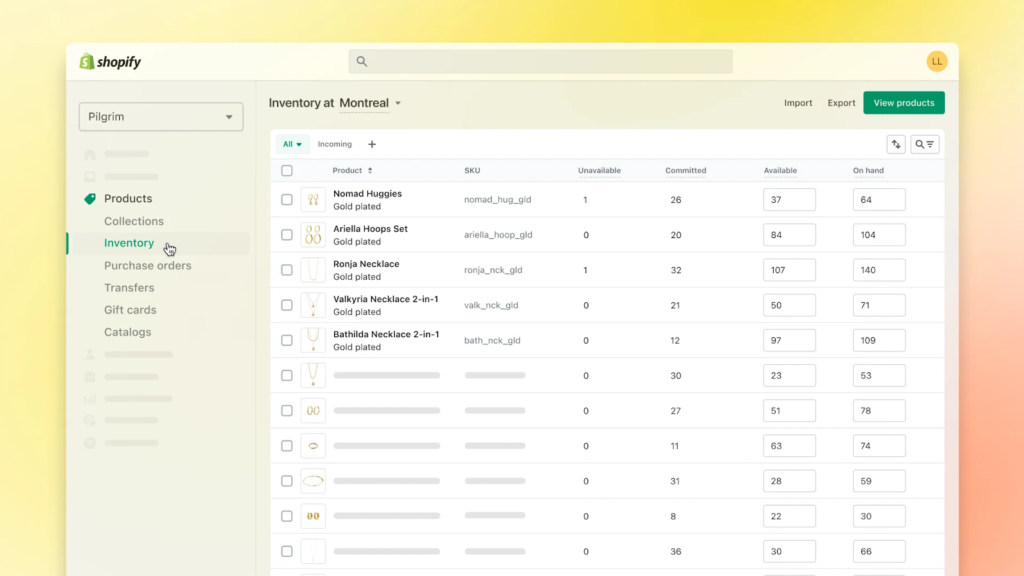
Omnichannel selling: Shopify’s Android POS software comes with built-in omnichannel selling tools, which allow you to manage multichannel inventory and sales from a single platform. You can track real-time data and update stocks, communicate with employees, and configure sales reports from your Android device.
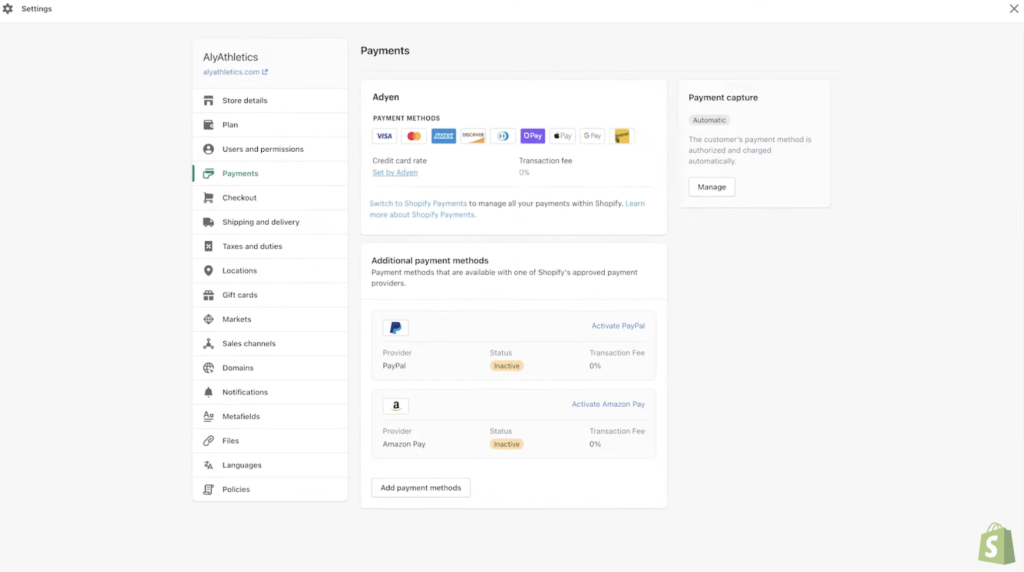
Built-in payment services: Shopify offers native payment processing, Shopify Payments for seamless acceptance of various credit card payment methods. You can also accept ACH and B2B payments for both in-person and online transactions.
Ecommerce features: Shopify’s core product offering is its ecommerce platform, which comes with robust checkout, inventory, and order fulfillment features. Shopify also allows you to integrate your website with Facebook, Instagram, TikTok, and Pinterest.

Clover Go: Best for overall flexibility
Overall Score
4.19/5
Pricing
4.06/5
Management tools
3.86/5
Register features
4.58/5
Support & reliability
4.69/5
User experience
3.92/5
Pros
- Card reader that connects with Android smart devices
- POS and hardware available from various payment processors
- Industry-specific POS software
- Offline payment processing available
Cons
- Hardware cannot be reprogrammed
- Little oversight on third-party vendors
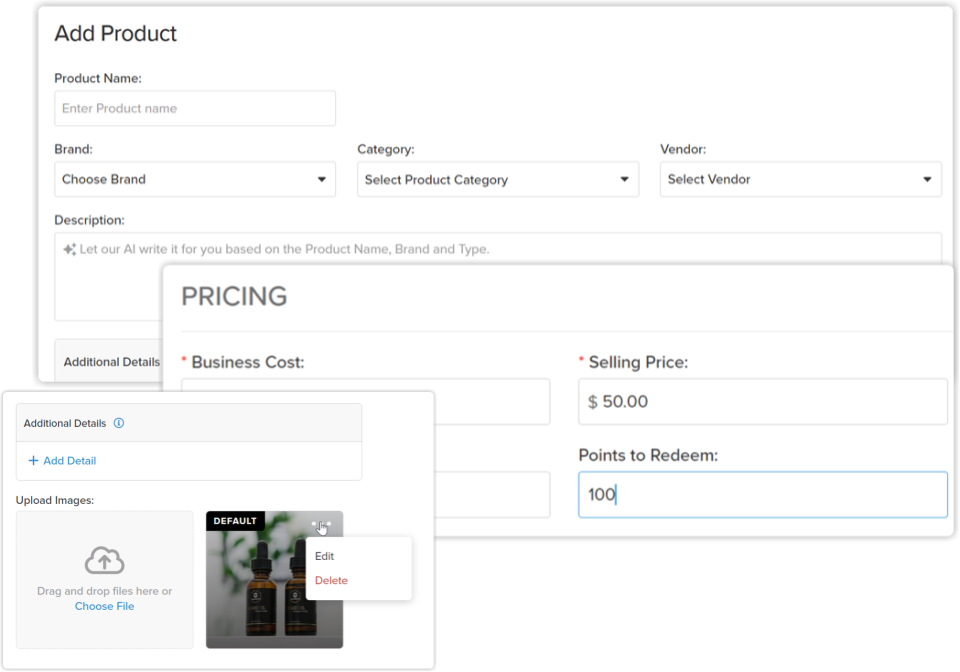
- Unable to upload images to inventory (only for online menu)
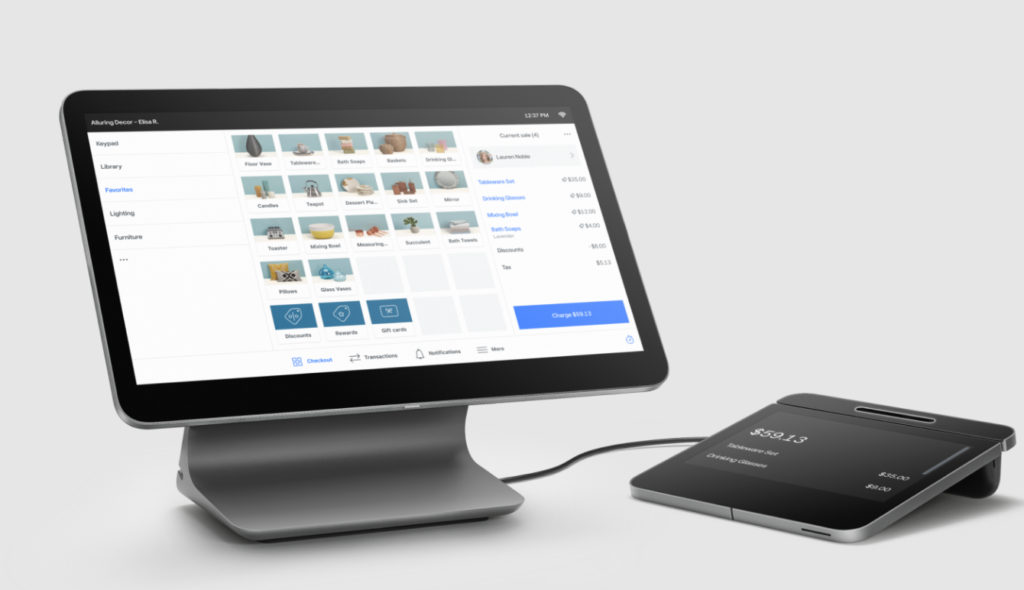
Why I chose Clover’s Android POS
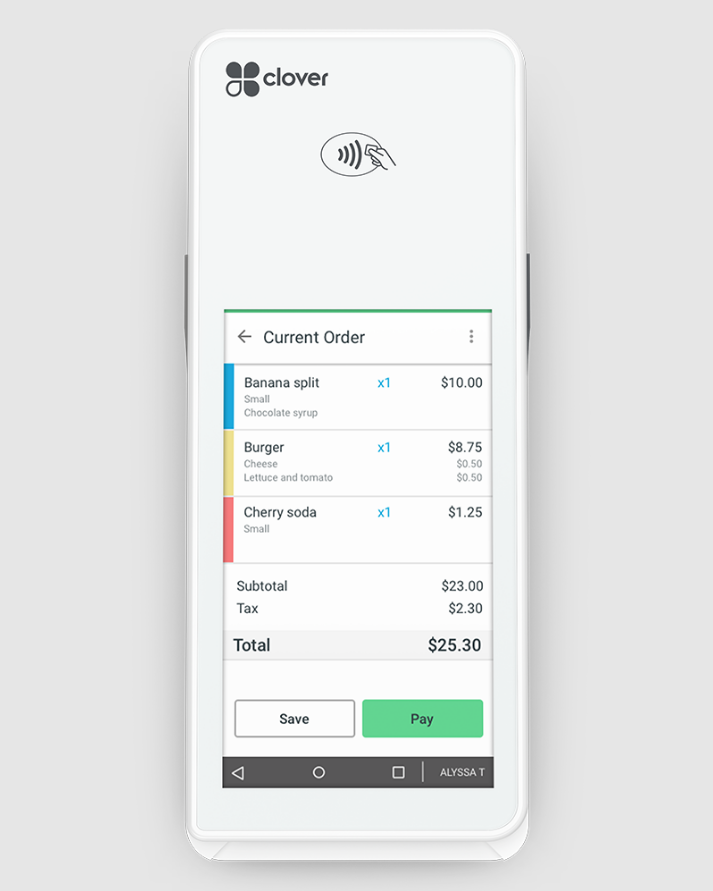
Clover is a popular all-in-one POS solution owned by Fiserv, a global fintech and payments company. What’s unique about Clover is that aside from using Fiserv directly as a payment processor, the Clover hardware and POS system can be purchased through any of Fiserv’s resellers or independent sales partners (ISOs), which includes payment service providers Stax and PaymentCloud.
I chose Clover for this guide, but I only recommend this to seasoned entrepreneurs who have enough experience dealing with POS providers to get the most out of the system. Because while Clover does not tie you to a single payment processor like Square, you will need to be familiar with POS and payment subscription plans to effectively compare your current payment processor’s fees against what’s available in the market.
I like how you don’t have to stick to Clover’s hardware to upgrade. Online marketplaces such as Amazon have a long list of Clover-compatible cash drawers, barcode scanners, and thermal printers to complete your countertop setup. However, again, you’ll need to have an idea of what to expect in terms of pricing.
Clover has little oversight on how resellers price their software and hardware. This may be an advantage or disadvantage (even for savvy business owners), depending on how you look at it. On one hand, you may get better all-in-one POS system deals; on the other hand, you may find it difficult to get support in case of software and hardware issues. It is also important to note that Clover hardware cannot be reprogrammed to work with a different processor once purchased from a reseller, so choose wisely.
Related: Best mobile POS systems
- Monthly fee: $14.95–$69.90
- In-person transaction fees (Fiserv direct): 2.3%-2.6% + 10 cents
- Online transaction fees (Fiserv direct): 3.5% + 10 cents
- Hardware Cost (Fiserv direct): From $49
Note: Subscription, transaction fees, and other contract terms will vary depending on where you purchase your Clover system.
Android POS app: The Clover Go dashboard and POS is available for Android users on Google Play. You can download the software on a smartphone or tablet and connect the mobile card reader to accept credit card and signature debit card transactions. The Clover Go card reader and app has the second highest rating on this list after Loyverse with a score of 4.7 out of 5 from around 6,000 reviews.
Android POS hardware: Clover does not have its own tablet stand, but you can get one from third party sellers and marketplaces. Connect your tablet to the Clover Go mobile card reader and add the optional Clover Go dock (with built-in USB charging port and security lock) for a countertop setup.
Supported Android hardware accessories: You can purchase Android-compatible cash drawers, barcode scanners, and thermal printers from third-party vendors and marketplaces
Flexible payment processor: The Clover hardware and POS software is available through third party payment processing resellers that partner with Fiserv, allowing you to shop for the best rates and more savings.
Built-in loyalty program: Clover’s loyalty program is included in all of its POS plans. It provides you with a free customer-facing mobile app (available for iOS and Android). The app allows you to track your customers’ reward points and update their records in real time.
Customer engagement: Clover allows you to create real-time promotions, which you can launch via email, text, or social media.
Scalability: Large businesses with their own custom Android-based POS system can program Clover’s hardware via Clover Connector API.

Vagaro: Best for appointment-based POS software
Overall Score
4.12/5
Pricing
4.38/5
Management tools
3.96/5
Register features
4.17/5
Support & reliability
3.44/5
User experience
4.36/5
Pros
- Proprietary Android POS terminal
- Easy-to-use calendar and scheduler
- 24/7 support with free training
- Fully HIPAA compliant
Cons
- No free plan
- Tied to built-in payment processor
- Limited hardware options
Why I chose Vagaro Android POS
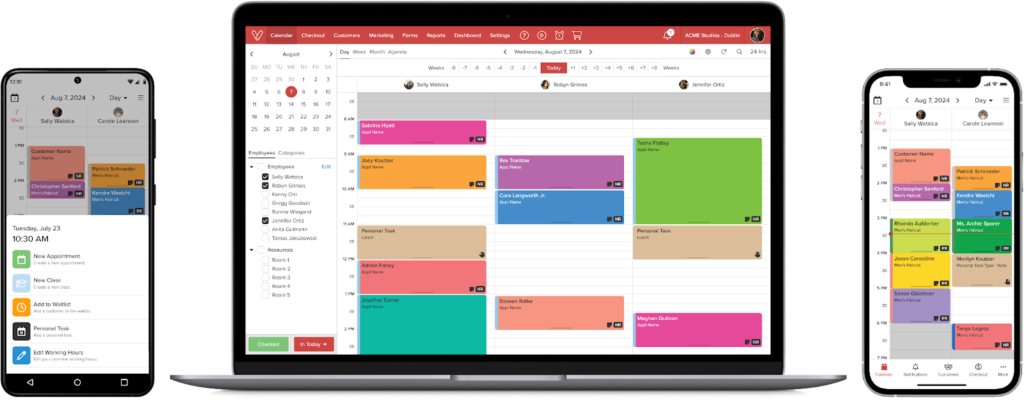
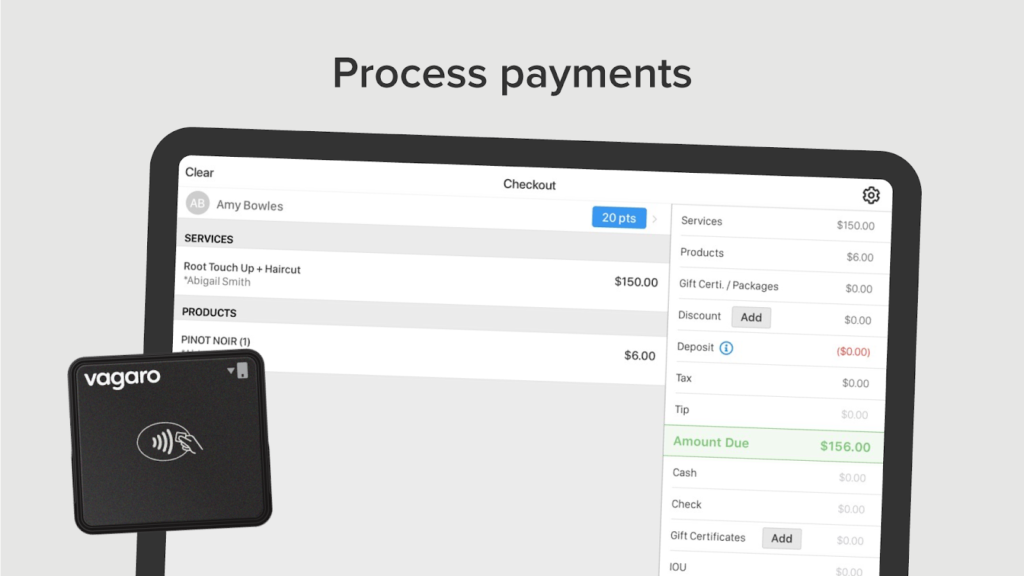
Launched in 2009, Vagaro is a cloud-based, fully HIPAA-compliant POS software provider for professionals in the beauty, wellness, and fitness industry. The software is popular for its robust booking and marketing features. Vagaro then added a proprietary payment processing service in 2016 and recently launched a set of sleek POS hardware to its lineup.
Today, around 83,000 businesses use Vagaro’s all-in-one POS system for appointments, online sales, customer, inventory, marketing, and employee management. While many POS apps have high ratings for their iOS version and lower ratings for their Android version, Vagaro is highly rated by both iOS and Android users.
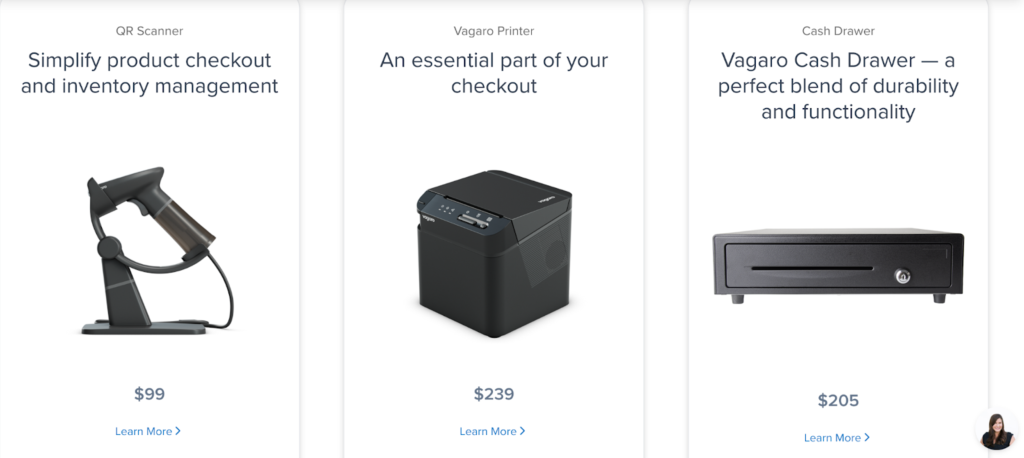
What I love most about this provider as an Android POS system is that, like Shopify, Vagaro’s POS terminal is compatible with Android tablets. You can purchase hardware directly from their website, so you’re assured an easy setup, seamless integration, and full support.
While you can download the POS software for free on Google Play, you’ll need to spend at least $30 per month to use one calendar. That said, Vagaro is one of the most popular software in the appointment scheduling space, with predominantly positive reviews. And while the choice of hardware is limited compared to other popular options like Square, you won’t have problems adding compatible scanners, printers, and cash drawers to build your countertop setup.
- Monthly POS fee: $30/month for one calendar, + $10 for each additional bookable calendar.
- Monthly payment processing fee: $0 (small merchants), $10 (large merchants)
- In-person transaction fee: 2.75% (small merchants), 2.2% + 19 cents (large merchants)
- Online transaction fee: 3.5% + 15 cents (small merchants), 3% + 19 cents (large merchants)
- Tap to pay transactions: + 5 cents per transaction
- Hardware: Starts at $0 (free credit card reader), countertops start at $370
Android POS app: Vagaro’s POS app is compatible with both iOS and Android. It consistently receives above-average ratings, though this is a small percentage of feedback considering the app has over a million downloads. It is currently 4.3 out of 5 from nearly 9,000 Android users.
Android POS hardware: Vagaro offers a choice between a simple tablet stand that you can connect to your mobile card reader or a complete POS terminal with a built-in card reader compatible with Android tablets, plus an optional customer display.
Supported Android hardware accessories: Vagaro offers proprietary POS hardware peripherals such as barcode scanners, thermal printers, and cash drawers
Robust business management features: On top of bookable calendars, Vagaro’s POS software comes with robust management features. This includes invoicing, inventory, reports, and payroll management, plus premium tools such as rent collection, membership/subscriptions, and ecommerce tools.
HIPAA-compliant POS software: HIPAA compliance means you can use Vagaro to securely store patient health information, ideal for clinics and other medical practices.
Native payment processor: Every Vagaro account comes with a built-in payment processing service plus a free mobile credit card reader to start accepting payments.
Customer-facing appointment app: Vagaro’s customer-facing scheduling app helps users set up and manage their appointments from their smartphones. Information is updated in real-time on your Vagaro calendar.
Key features of Android POS systems
The nature of the Android OS provides users with a simpler setup, better connectivity, and easier management than other operating software, which is why the two main features of Android POS systems are flexibility and mobility. That said, it’s also important to consider value-for-money features tailored to different business types.
So when choosing an Android POS system, be sure to look for the following key features:
Software compatibility
By default, Android POS software should be able to work seamlessly with most Android-based POS hardware. That said, you should still make sure to choose one that’s compatible with the Android operating software version installed on your smartphone or tablet. Because while you may be able to run the current platform on an older Android device, there is a big risk that software updates may not be supported.
Card reader reliability
While Android systems are highly compatible, some providers still experience frequent failed transactions due to faulty hardware. Before choosing a provider, research card reader feedback from real-life users on the Google Play Store and other third-party review sites.
Seamless payment processing
Like any top-tier POS system, Android POS software offers seamless payment processing, whether as a built-in feature or a third-party integration. Choose a provider that supports most payment methods, including contactless payments from Android-based smart devices.
Offline mode
Customer checkout should not be interrupted in cases of temporary internet downtime. The system can keep a record of transactions that will be processed once connectivity is restored.
Business management features
The system supports key POS features such as inventory, customer management, marketing, and reporting tools. It should also be compatible with third party business platform integrations built on an Android OS to help scale the POS system as the business grows.
Regularly updated software
The POS software is regularly updated with little to no downtime to business operations. Updates are also properly documented and available for feedback on the Google Play platform.
Read more: How much do POS systems cost?
Choosing the best Android POS system
The Android operating system is built on an open-source platform, so it’s no surprise that there are many payment and POS software built on Android. That said, the best Android POS for your business should match your business model and fulfill your specific goals.
In general, your Android POS should be able to:
- Run on your Android smartphone or tablet
- Provide a card reader that seamlessly connects with your Android smartphone or tablet
- Offer both a mobile and countertop setup
- Integrate seamlessly with other Android-based POS hardware peripherals
- Easily update with no additional cost and little to zero downtime
With this in mind, I recommend the following:
Square is the all around best value Android-based POS system for small and new businesses. It offers the most feature-rich free plan that includes industry-specific software plus hardware you can build around your Android tablet and card reader.
Loyverse is a standout for quick service restaurants and food retailers. It provides an impressive set of inventory management tools, plus free loyalty and kitchen display system. Loyverse also supports a full list of Android-based hardware.
Shopify POS is the best choice for ecommerce retailers. It offers excellent omnichannel management tools and supports full Android-based POS hardware.
Clover is an excellent alternative for business savvy entrepreneurs who want better control of business costs. The system is available from a number of popular payment service providers with varying rates to choose from. Third party vendors offer Android compatible hardware peripherals to build around your Clover card reader and tablet.
Vagaro is my top recommendation for Android-based appointment and scheduling POS software. The system offers a complete suite of software, hardware, ecommerce, and payment services, plus marketing, payroll, and order fulfillment tools for an easy all-in-one setup.
FAQs
Yes, popular POS software providers now offer app-based systems that can run on iOS and Android operating software (OS).
An Android POS is a point-of-sale and business management system that runs on Android OS. This makes it compatible with smartphones, tablets, and other hardware peripherals such as mobile credit card readers, barcode scanners, thermal printers, and cash registers.
A traditional POS system is based on a countertop setup where customers queue to checkout their purchases. An Android POS system, on the other hand, allows you and your staff to ring in sales anywhere with an Android device.
A mobile POS (MPOS) and can run on either an iOS or Android OS. While an mPOS offers great mobility, an Android-based POS software is more flexible because developers can use the OS to create their custom countertop system that can pair seamlessly with other Android-based devices in the market.
The post The Best Android POS Systems appeared first on TechnologyAdvice.