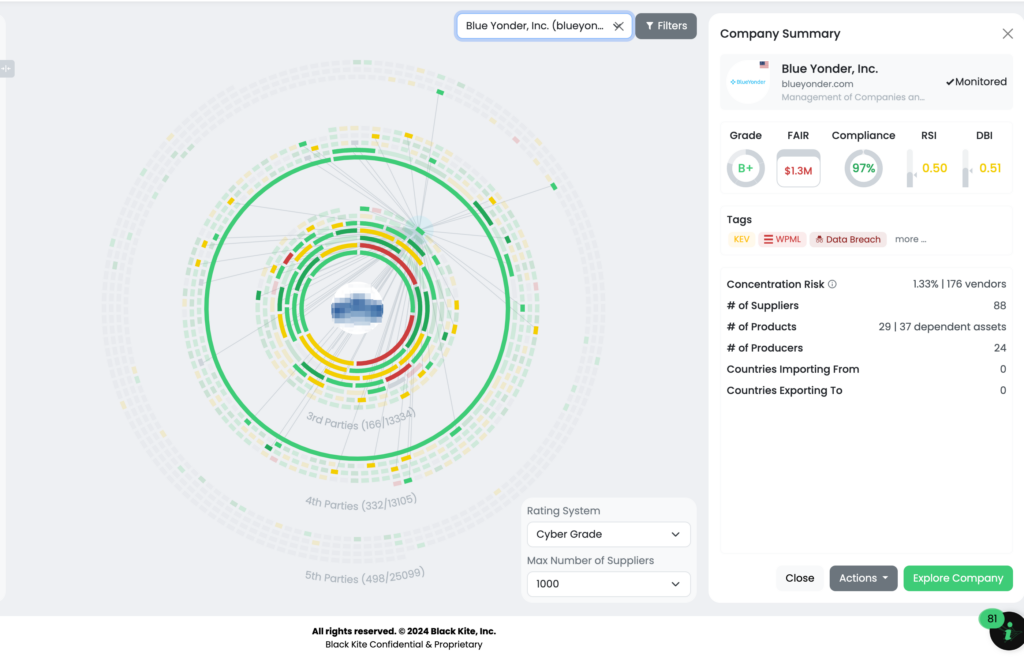
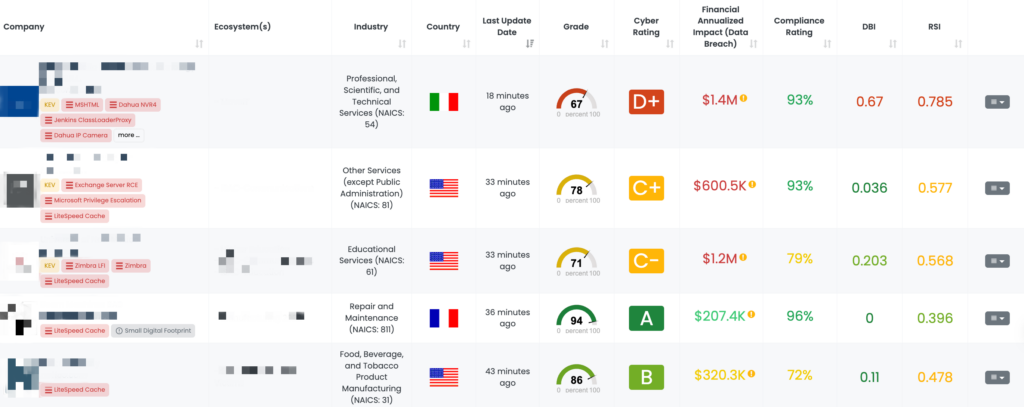
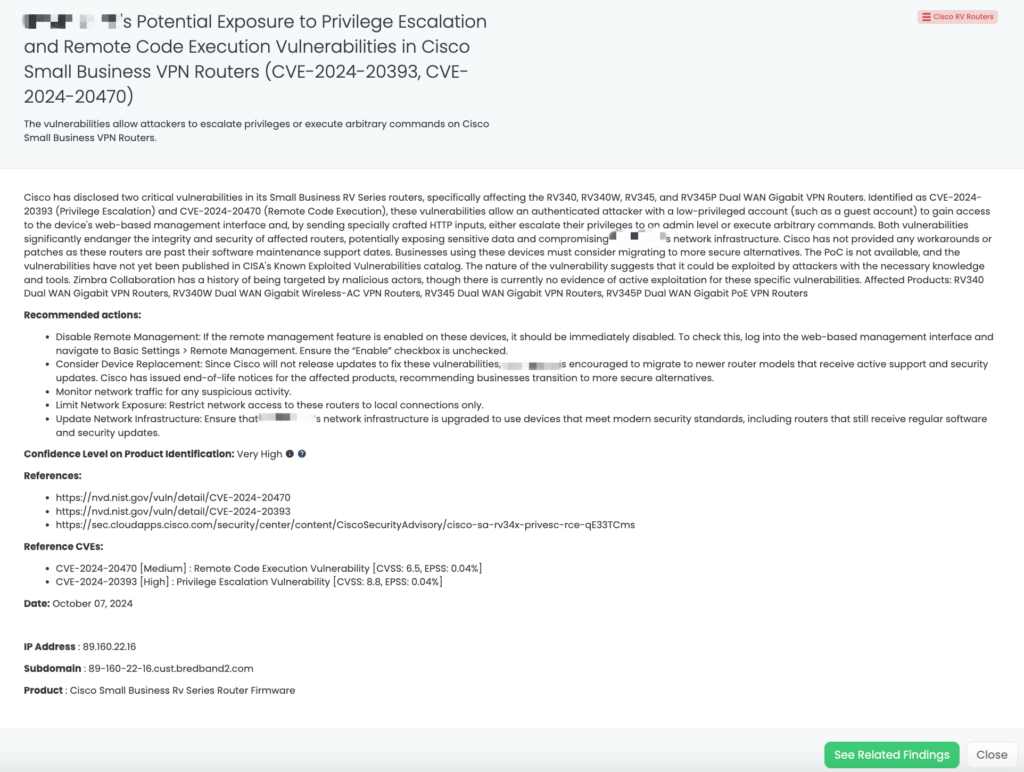
FOCUS FRIDAY: Third-Party Risks From Critical Juniper Junos, Rsync, and SimpleHelp Vulnerabilities
Written by: Ferdi Gül
Welcome to this week’s Focus Friday, where we dive into key vulnerabilities impacting widely used technologies. This installment highlights three significant incidents that pose unique challenges to third-party risk management (TPRM) teams. From Juniper Junos OS to Rsync and SimpleHelp, we explore how these vulnerabilities affect the security posture of vendors and their downstream supply chains. By examining these issues, we aim to provide actionable insights and strategies to help organizations mitigate risks and maintain robust third-party relationships.

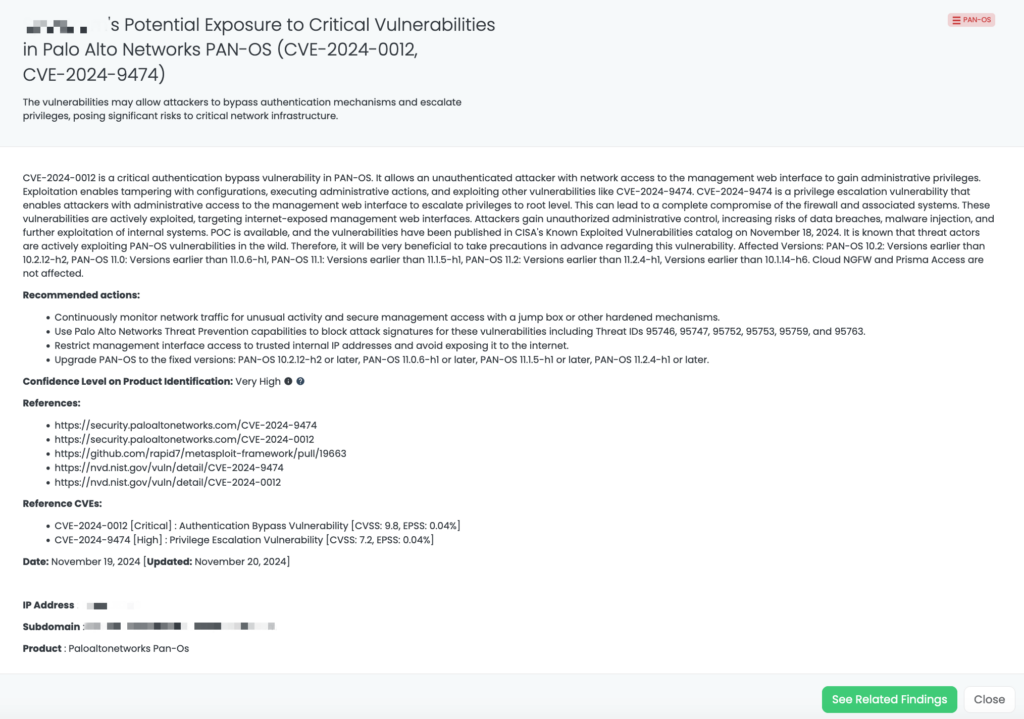
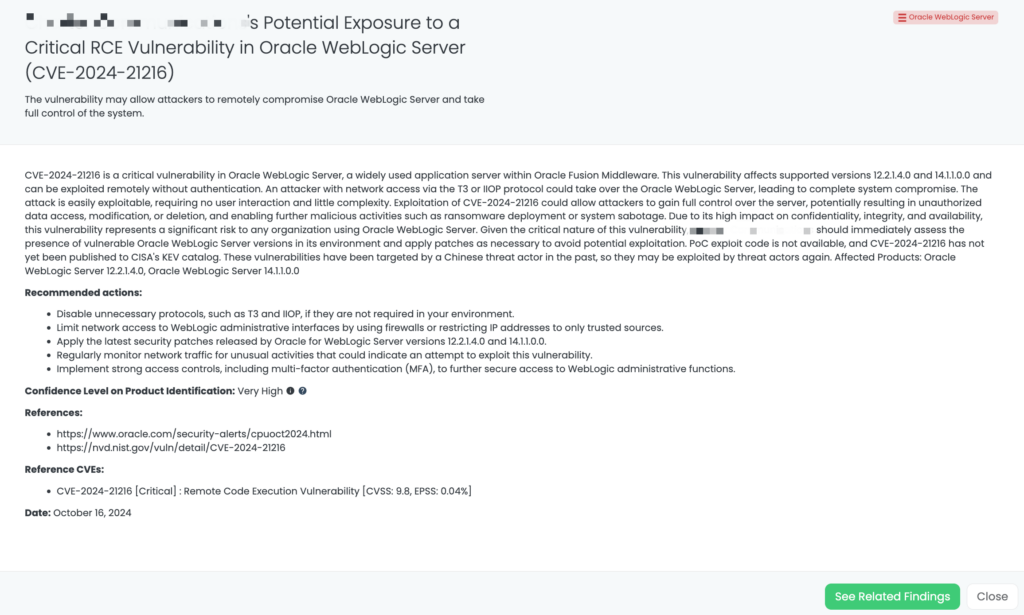
Juniper Junos CVE-2025-21598
What is the Juniper Junos BGP Vulnerability (CVE-2025-21598)?
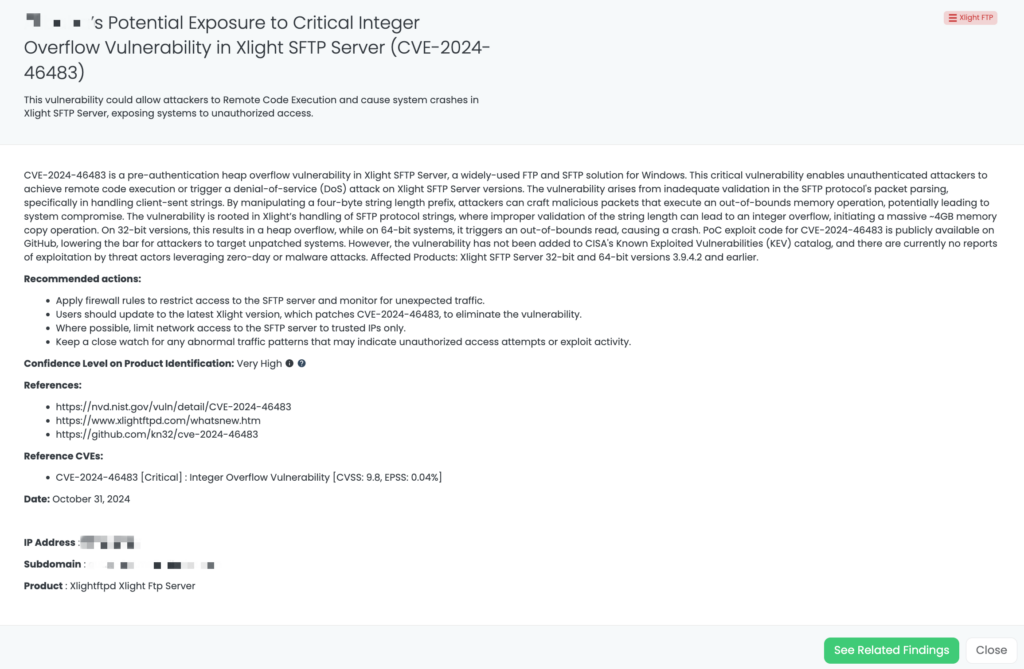
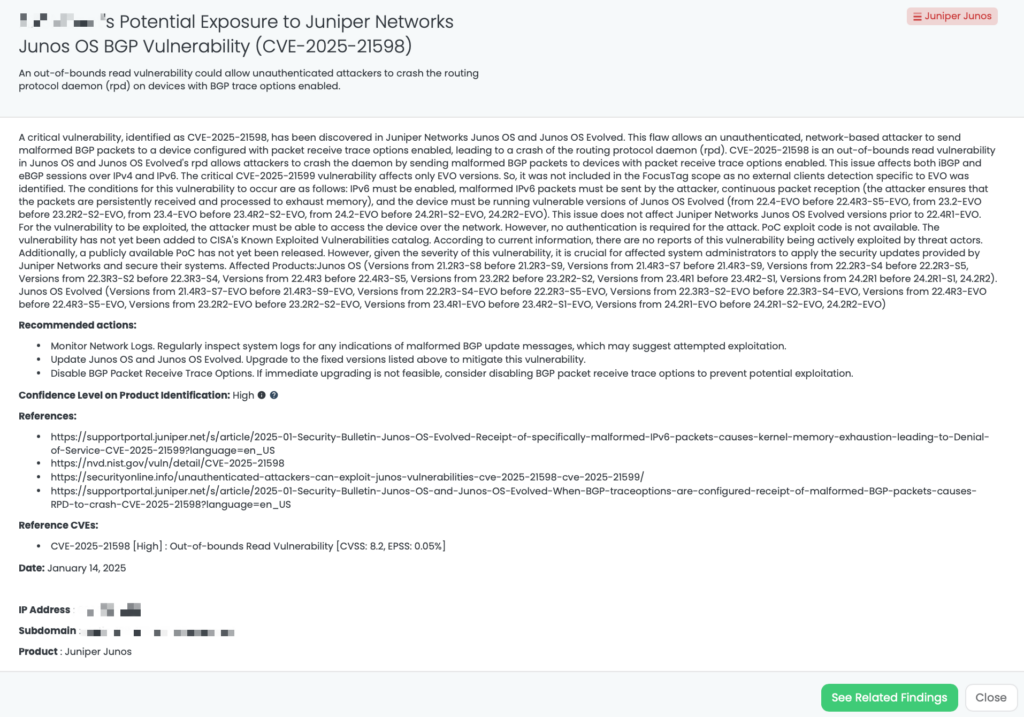
CVE-2025-21598 is an out-of-bounds read vulnerability in the routing protocol daemon (rpd) of Junos OS and Junos OS Evolved. When a device is configured with BGP packet receive trace options, an unauthenticated attacker can send malformed BGP packets that cause the rpd process to crash. This vulnerability has a CVSS score of 8.2, making it a high-severity issue. It was first disclosed on January 14, 2025, and there are currently no reports of active exploitation. CISA’s KEV catalog does not yet list this vulnerability. Proof-of-concept (POC) is not available.
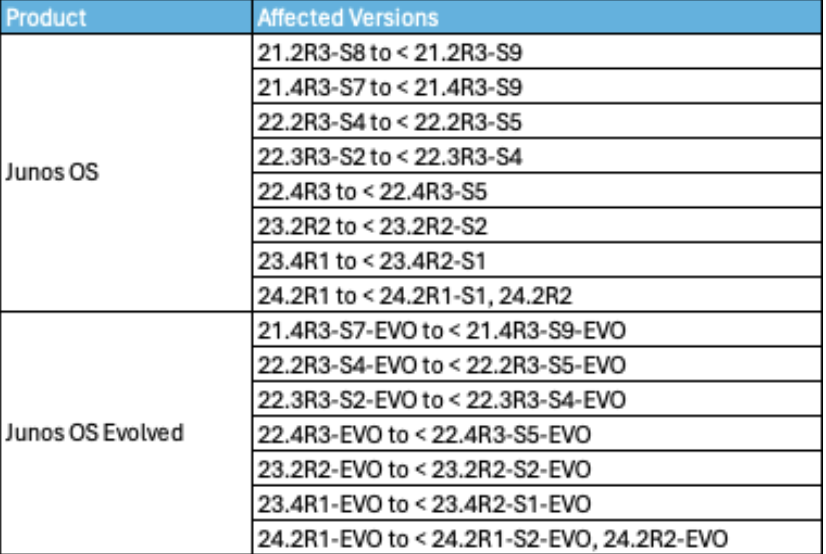
CVE-2025-21599 is a critical vulnerability affecting specific versions of Junos OS Evolved. It requires IPv6 to be enabled and involves attackers sending malformed IPv6 packets persistently to exhaust memory. Exploitation does not require authentication but needs network access to the device. The affected versions are:
- From 22.4-EVO: before 22.4R3-S5-EVO
- From 23.2-EVO: before 23.2R2-S2-EVO
- From 23.4-EVO: before 23.4R2-S2-EVO
- From 24.2-EVO: before 24.2R1-S2-EVO, and 24.2R2-EVO.
Versions prior to 22.4R1-EVO are unaffected. This vulnerability was excluded from the FocusTag™ scope due to its limitation to EVO versions and no detection by external clients specific to EVO.
Why should TPRM professionals care about CVE-2025-21598?
This vulnerability impacts network infrastructure devices, which are critical to business operations. If left unpatched, it could result in significant service interruptions, loss of connectivity, and reduced reliability of the affected network environment. Organizations that rely on these devices could face disruptions in their supply chain communications and business operations, making it essential for TPRM professionals to assess the risk and ensure proper mitigation measures are in place.
What questions should TPRM professionals ask vendors about CVE-2025-21598?
- Have you updated all instances of Junos OS and Junos OS Evolved to the fixed versions mentioned in the advisory to mitigate the risk of CVE-2025-21598?
- Can you confirm if you have disabled BGP packet receive trace options on your Junos OS and Junos OS Evolved devices to prevent potential exploitation of CVE-2025-21598?
- Are you regularly inspecting your system logs for any indications of malformed BGP update messages, which may suggest attempted exploitation of CVE-2025-21598?
- For Junos OS Evolved, have you ensured that all versions from 22.4-EVO before 22.4R3-S5-EVO, from 23.2-EVO before 23.2R2-S2-EVO, from 23.4-EVO before 23.4R2-S2-EVO, from 24.2-EVO before 24.2R1-S2-EVO, 24.2R2-EVO have been updated to mitigate the risk of CVE-2025-21599?
Remediation recommendations for vendors subject to this risk
- Upgrade all affected Junos OS and Junos OS Evolved devices to the patched versions.
- Disable BGP packets receive trace options if updating is not immediately possible.
- Implement continuous network monitoring to identify any indications of exploitation attempts.
- Maintain up-to-date logging configurations and review logs for signs of malformed BGP packets.
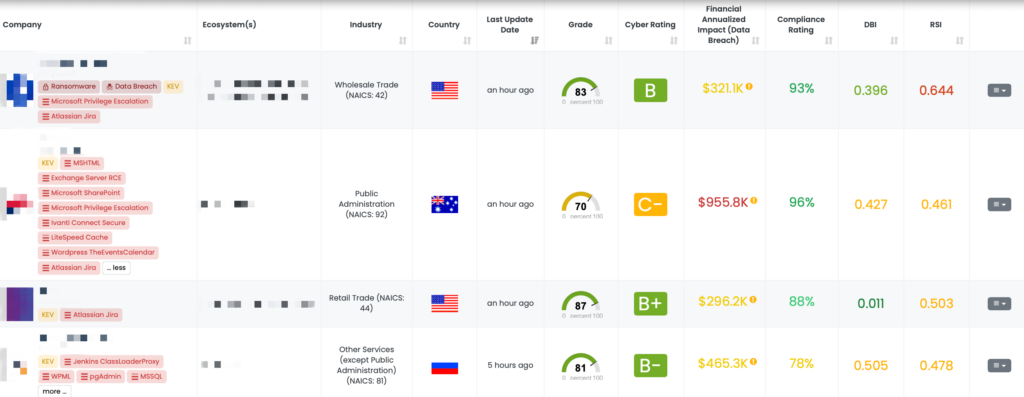
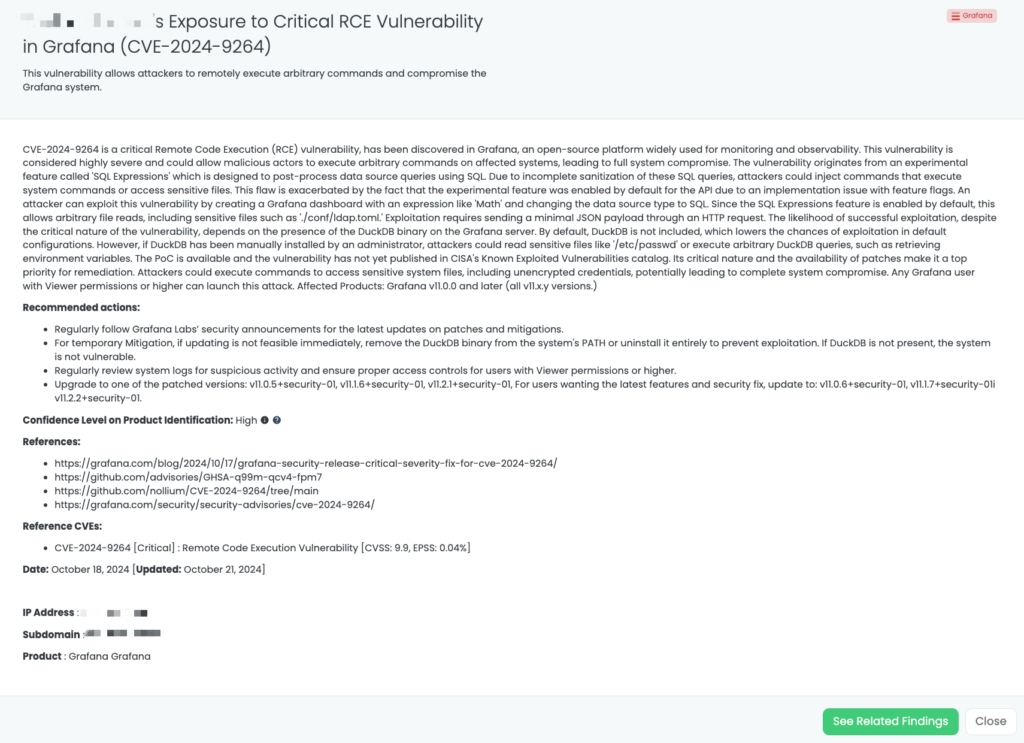
How can TPRM professionals leverage Black Kite for CVE-2025-21598?
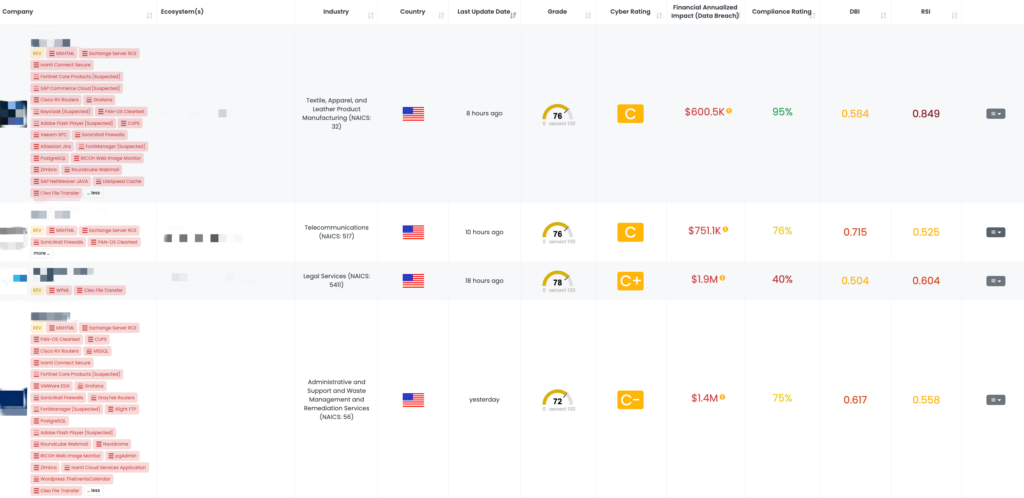
Black Kite published this FocusTag™ to help organizations pinpoint the vendors affected by CVE-2025-21598. By providing detailed asset information—including relevant subdomains and vulnerable IPs—Black Kite enables TPRM professionals to rapidly identify which vendors need immediate attention. This targeted approach reduces time spent on outreach and allows more efficient mitigation efforts.
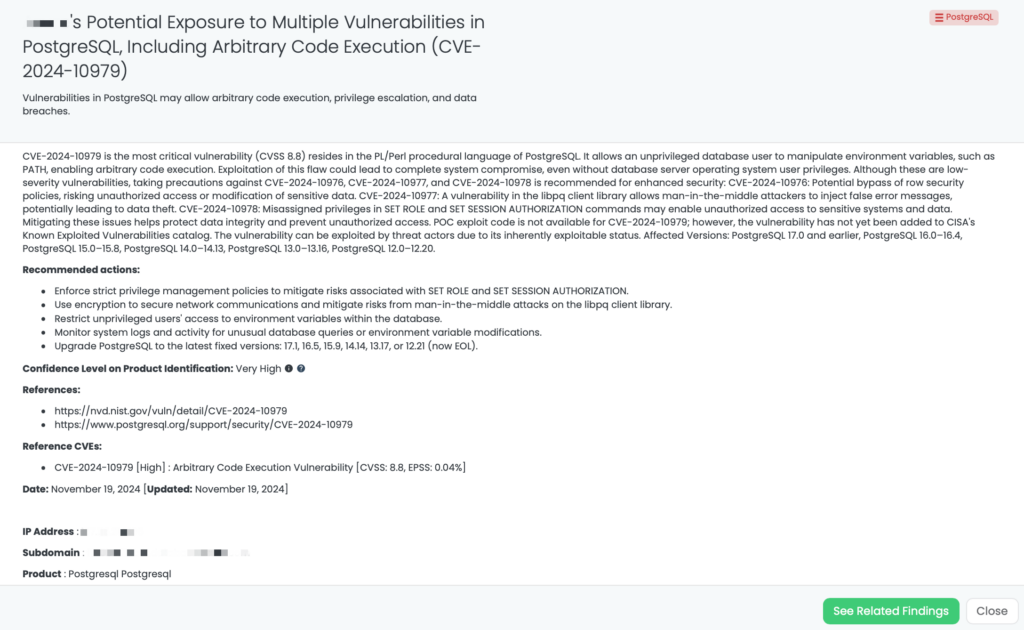
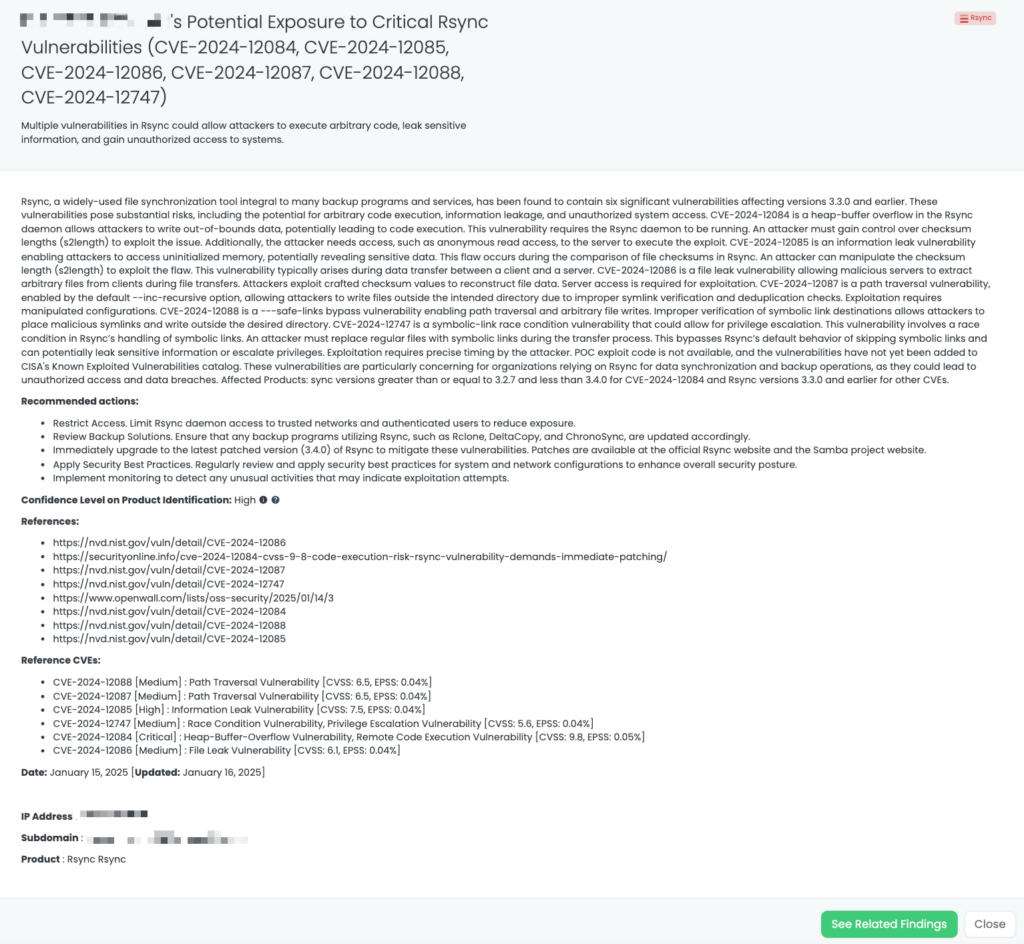
Rsync Vulnerabilities (CVE-2024-12084, CVE-2024-12085, CVE-2024-12086, CVE-2024-12087, CVE-2024-12088, CVE-2024-12747)
What are the critical Rsync vulnerabilities?
Rsync, a widely-used file synchronization tool, has six significant vulnerabilities in versions 3.3.0 and earlier. These flaws pose risks such as arbitrary code execution, information leakage, and unauthorized system access, particularly for organizations relying on Rsync for backups.
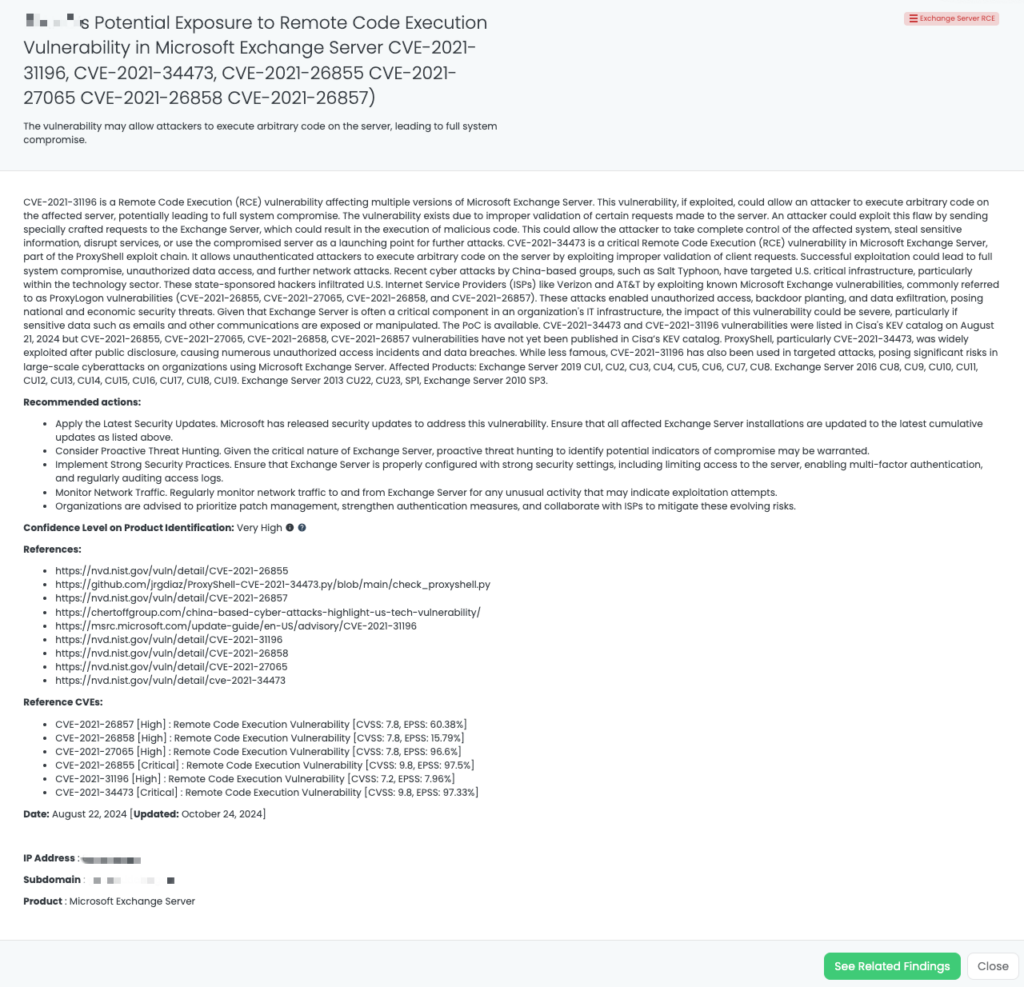
Six vulnerabilities have been identified in Rsync, posing significant security risks. These include a heap-buffer overflow (CVE-2024-12084) in the Rsync daemon that allows attackers to execute code by controlling checksum lengths (s2length) and gaining server access. An information leak vulnerability (CVE-2024-12085) exposes uninitialized memory during file checksum comparisons. Additionally, malicious servers can exploit crafted checksums to extract arbitrary files from clients (CVE-2024-12086). Path traversal is possible due to improper symlink checks with the default –inc-recursive option (CVE-2024-12087), while a –safe-links bypass flaw (CVE-2024-12088) allows arbitrary file writes and further path traversal. Finally, a symbolic-link race condition (CVE-2024-12747) could lead to privilege escalation or data leakage by exploiting timing issues during file transfers. Exploitation of these vulnerabilities requires specific conditions, such as server access or manipulated configurations.
Currently, no publicly available POC exists, and these vulnerabilities are not listed in CISA’s Known Exploited Vulnerabilities catalog. Affected versions include Rsync ≥3.2.7 and <3.4.0 for CVE-2024-12084, while other CVEs impact Rsync 3.3.0 and earlier. Organizations relying on Rsync for synchronization or backups should apply patches or mitigations promptly to mitigate risks of unauthorized access and data breaches.
Why should TPRM professionals care about Rsync vulnerabilities?
Many organizations rely on Rsync for critical backup operations. Unaddressed vulnerabilities could lead to severe disruptions, including unauthorized data exposure, system compromise, and operational downtime. These risks demand immediate attention from TPRM professionals to ensure that vendors and their supply chain partners have implemented the necessary remediations.
What questions should TPRM professionals ask vendors about the Rsync vulnerabilities?
- Have you upgraded all instances of Rsync to version 3.4.0 or later to mitigate the risk of CVE-2024-12084, CVE-2024-12085, CVE-2024-12086, CVE-2024-12087, CVE-2024-12088, and CVE-2024-12747?
- Can you confirm if you have implemented the recommended mitigation measures such as restricting Rsync daemon access to trusted networks and authenticated users, and regularly reviewing and applying security best practices for system and network configurations?
- Have you reviewed and updated any backup programs utilizing Rsync, such as Rclone, DeltaCopy, and ChronoSync, in response to these vulnerabilities?
- Are you monitoring for any unusual activities that may indicate exploitation attempts related to these Rsync vulnerabilities, specifically those related to heap-buffer overflow, information leak, file leak, path traversal, safe-links bypass, and symbolic-link race condition?
Remediation recommendations for vendors subject to this risk
- Upgrade Rsync to version 3.4.0 or higher to eliminate known vulnerabilities.
- Disable unused options such as –inc-recursive and –safe-links to minimize exposure.
- Implement strict access controls, allowing only authenticated and trusted connections.
- Conduct regular security audits of your Rsync configuration and logs.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite’s FocusTag™ for Rsync, published in January 2025, helps TPRM professionals identify vendors at risk from these vulnerabilities. By providing detailed information on affected versions, associated IPs, and potentially vulnerable assets, Black Kite enables organizations to narrow their outreach to only those vendors requiring immediate action. This targeted approach not only streamlines risk management processes but also helps protect sensitive data and critical systems from emerging threats.
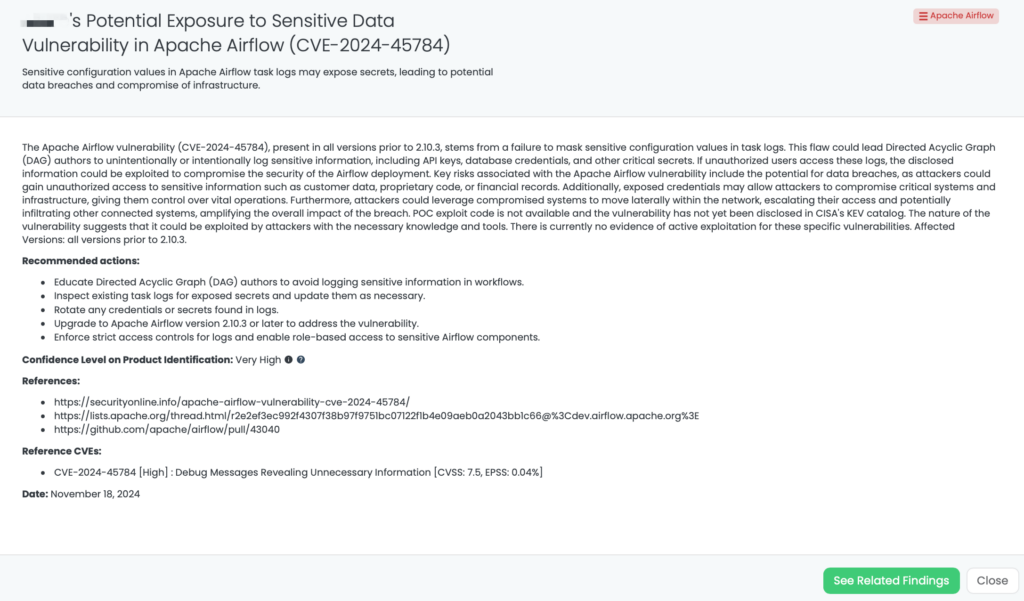
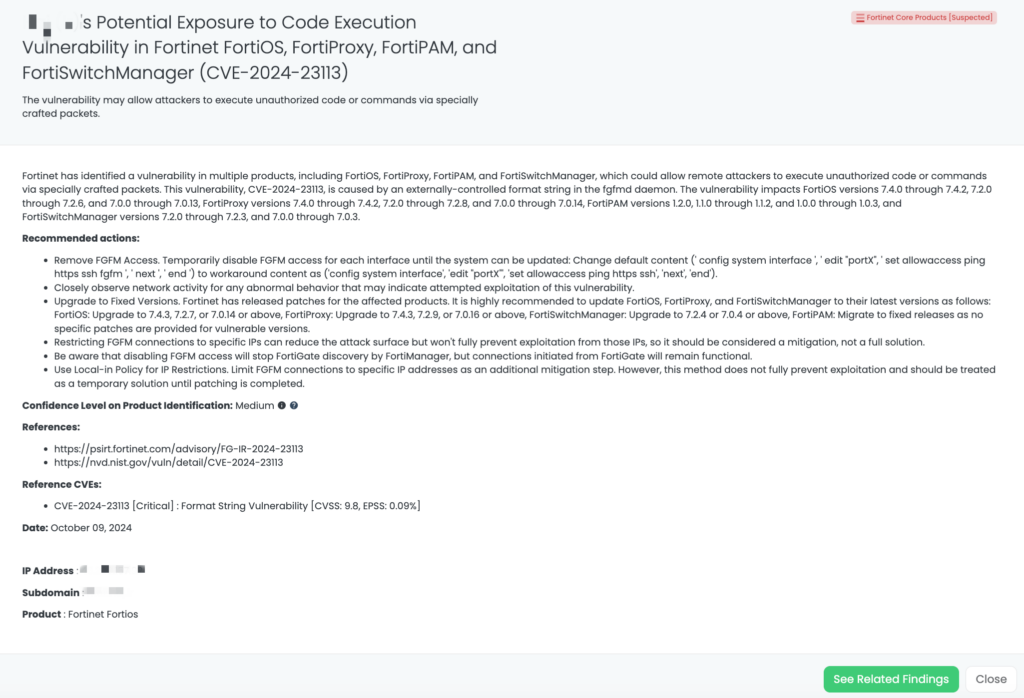
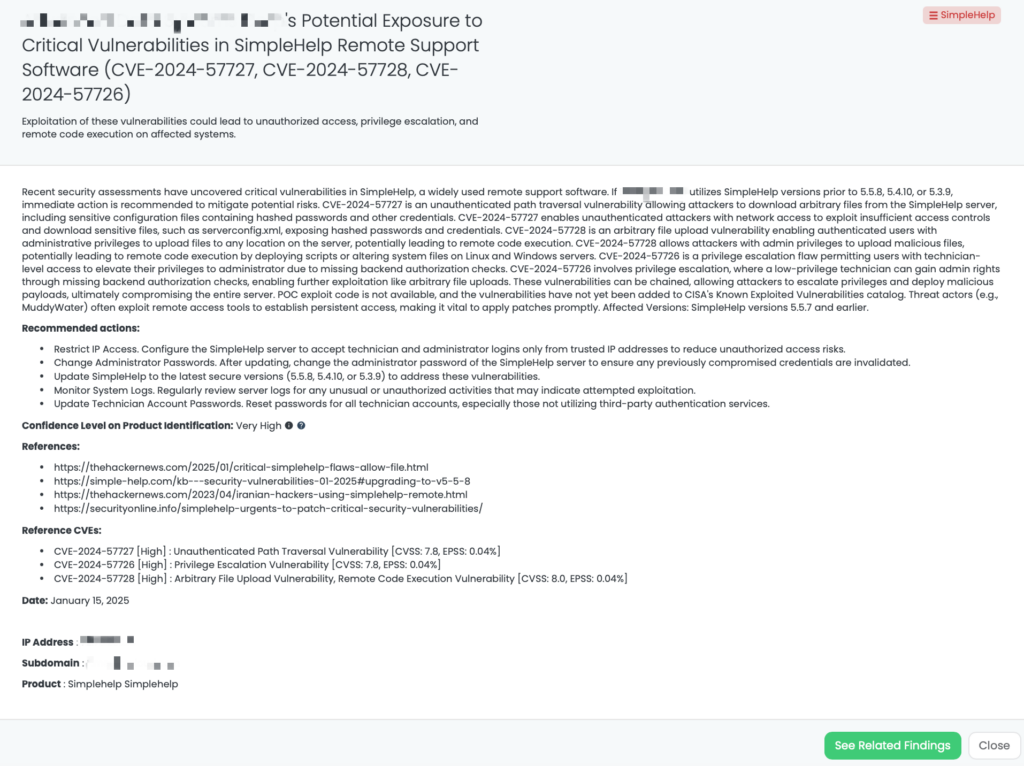
SimpleHelp Vulnerabilities (CVE-2024-57727, CVE-2024-57728, CVE-2024-57726)
What are the critical SimpleHelp vulnerabilities?
Recent security assessments have uncovered critical vulnerabilities in SimpleHelp, a widely used remote support software.
CVE-2024-57726: A privilege escalation flaw that allows users with technician-level access to elevate their privileges to administrator due to missing backend authorization checks. This vulnerability has a CVSS score of 8.2, making it a high-severity issue. This vulnerability has a CVSS score of 8.8, making it a high-severity issue.
CVE-2024-57727: A path traversal vulnerability allowing unauthenticated attackers to download arbitrary files, including sensitive configuration files. This vulnerability has a CVSS score of 7.5, making it a high-severity issue.
CVE-2024-57728: An arbitrary file upload vulnerability enabling attackers with administrative privileges to upload malicious files anywhere on the server, potentially leading to remote code execution. This vulnerability has a CVSS score of 8.8, making it a high-severity issue.
These vulnerabilities can be chained to compromise the entire server, leading to sensitive information disclosure and potential remote code execution. They affect SimpleHelp versions 5.5.7 and earlier. Currently, there are no reports of these vulnerabilities being exploited in the wild, no available PoC, and no listing in CISA’s Known Exploited Vulnerabilities catalog.
Why should TPRM professionals care about SimpleHelp vulnerabilities?
SimpleHelp is widely used for remote support, making these vulnerabilities particularly concerning. A compromised SimpleHelp server could expose sensitive client information, provide attackers with persistent remote access, and lead to unauthorized actions such as executing malicious scripts. TPRM professionals must ensure that vendors relying on SimpleHelp have patched their systems and implemented necessary security controls to avoid supply chain disruptions and data breaches.
What questions should TPRM professionals ask vendors about SimpleHelp vulnerabilities?
- Have you updated all instances of SimpleHelp to versions 5.5.8, 5.4.10, or 5.3.9 to mitigate the risk of CVE-2024-57727, CVE-2024-57728, and CVE-2024-57726?
- Can you confirm if you have implemented IP access restrictions on your SimpleHelp server to accept technician and administrator logins only from trusted IP addresses, as recommended in the advisory?
- Have you changed the administrator and technician account passwords after updating SimpleHelp to ensure any previously compromised credentials are invalidated?
- Are you regularly reviewing your server logs for any unusual or unauthorized activities that may indicate attempted exploitation of these vulnerabilities in SimpleHelp?
Remediation recommendations for vendors subject to this risk
- Update SimpleHelp to the latest secure versions (5.5.8, 5.4.10, or 5.3.9) to address these vulnerabilities.
- Change Administrator Passwords. After updating, change the administrator password of the SimpleHelp server to ensure any previously compromised credentials are invalidated.
- Update Technician Account Passwords. Reset passwords for all technician accounts, especially those not utilizing third-party authentication services.
- Restrict IP Access. Configure the SimpleHelp server to accept technician and administrator logins only from trusted IP addresses to reduce unauthorized access risks.
- Monitor System Logs. Regularly review server logs for any unusual or unauthorized activities that may indicate attempted exploitation.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite provides a detailed FocusTag™ highlighting these vulnerabilities, including a list of affected versions and mitigation steps. By using Black Kite’s asset information—such as associated IP addresses and potentially vulnerable subdomains—TPRM professionals can quickly identify which vendors require immediate attention, streamlining the risk mitigation process.
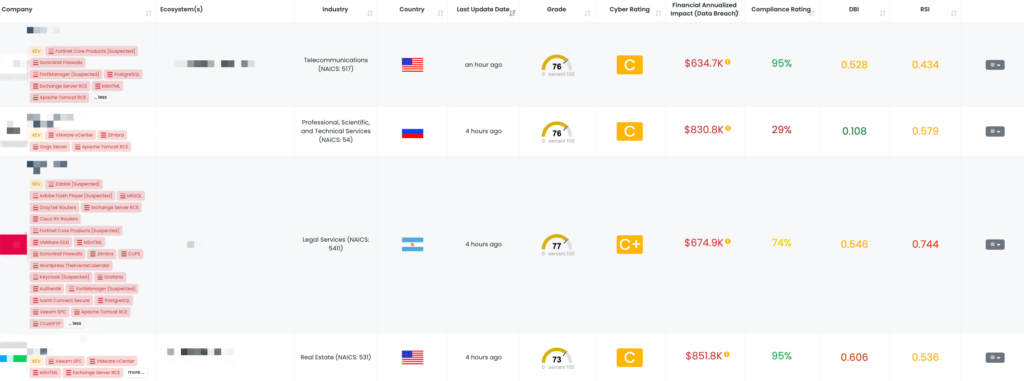
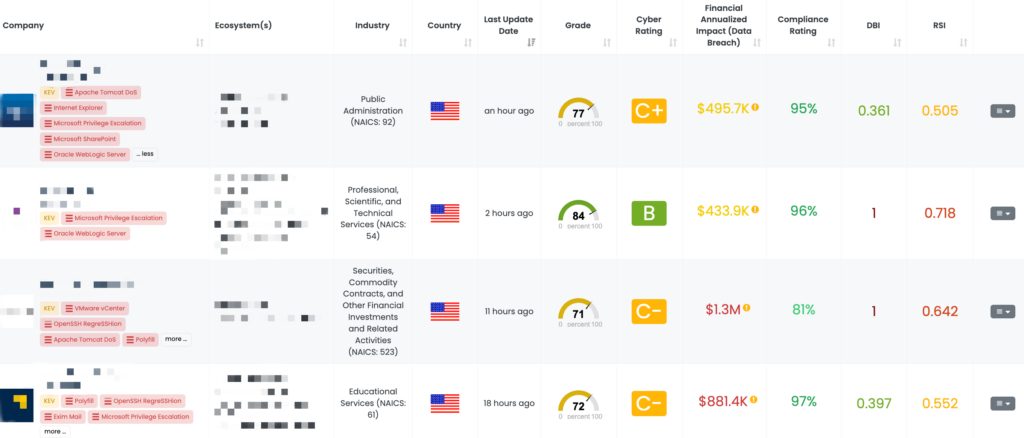
Enhancing TPRM Strategies with Black Kite’s FocusTags™
As the cyber threat landscape continues to evolve, maintaining a resilient Third-Party Risk Management (TPRM) framework is more crucial than ever. Black Kite’s FocusTags™ provide a unique advantage, allowing organizations to identify and respond to high-profile vulnerabilities quickly and effectively. By incorporating FocusTags into their TPRM processes, organizations gain:
Timely Vendor Risk Identification: Quickly determine which vendors are impacted by emerging threats, enabling prompt and strategic action.
Prioritized Risk Management: Focus on the most critical vulnerabilities and vendors, ensuring that resources are allocated where they’re needed most.
Enhanced Vendor Collaboration: Conduct more informed and productive discussions with vendors, addressing their specific exposure and improving overall security measures.
Broader Security Insight: Gain a comprehensive view of the current threat landscape, helping TPRM teams anticipate future risks and strengthen their cybersecurity defenses.
With Black Kite’s FocusTags™, TPRM professionals have the tools they need to transform complex threat data into actionable intelligence. This capability not only improves risk management efficiency but also helps ensure that organizations can confidently manage their third-party ecosystem in an increasingly unpredictable digital environment.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
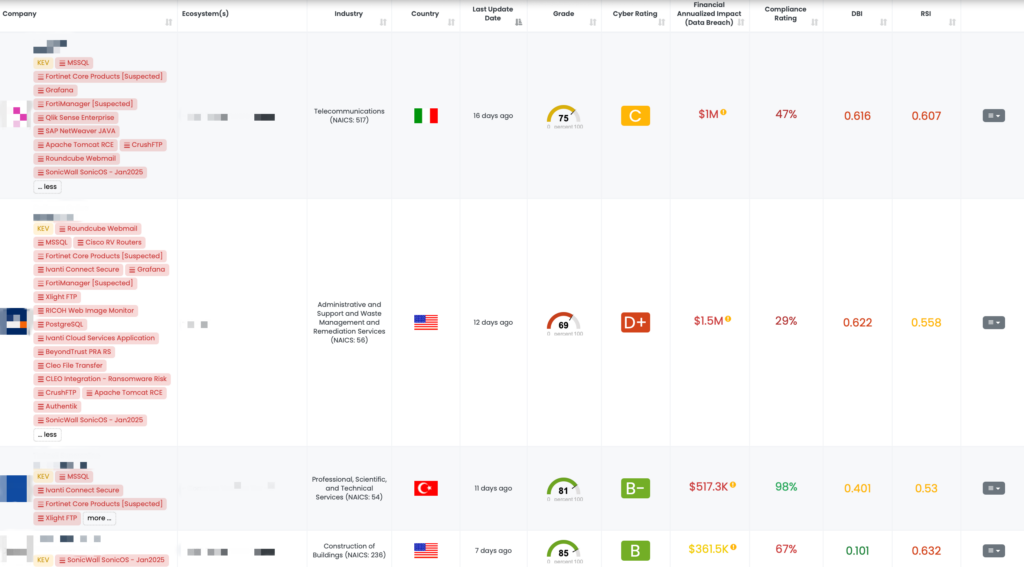
FocusTagsTM in the Last 30 Days:
- Juniper Junos: CVE-2025-21598, Out-of-bounds Read vulnerability in Juniper’s Junos.
- Rsync: CVE-2024-12084, CVE-2024-12085, CVE-2024-12086, CVE-2024-12087, CVE-2024-12088, CVE-2024-12747, Heap-Buffer-Overflow Vulnerability, Remote Code Execution Vulnerability, Information Leak Vulnerability, File Leak Vulnerability, Path Traversal Vulnerability, Race Condition Vulnerability, Privilege Escalation Vulnerability in Rsync.
- SimpleHelp: CVE-2024-57727, CVE-2024-57728, CVE-2024-57726, Unauthenticated Path Traversal Vulnerability, Arbitrary File Upload Vulnerability, Remote Code Execution Vulnerability, Privilege Escalation Vulnerability in SimpleHelp.
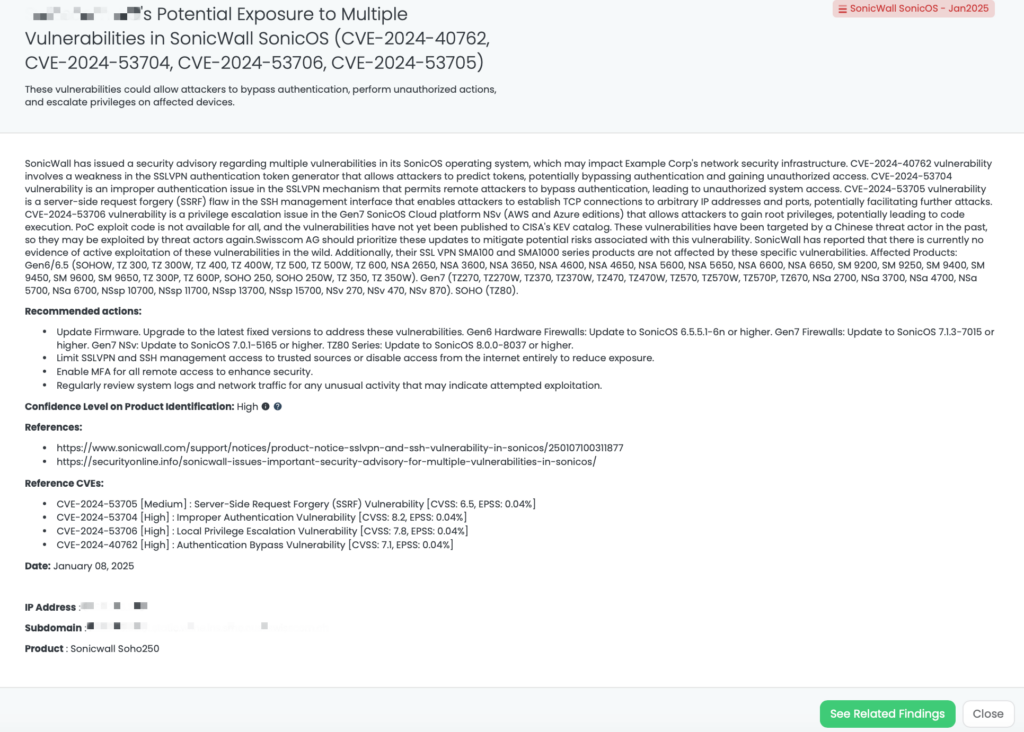
- SonicWall SonicOS – Jan2025: CVE-2024-40762, CVE-2024-53704, CVE-2024-53706, CVE-2024-53705, Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG), Authentication Bypass Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability, and Local Privilege Escalation Vulnerability in SonicWall’ SonicOS SSLVPN, SSH Management, and Gen7 Cloud NSv SSH Config Function.
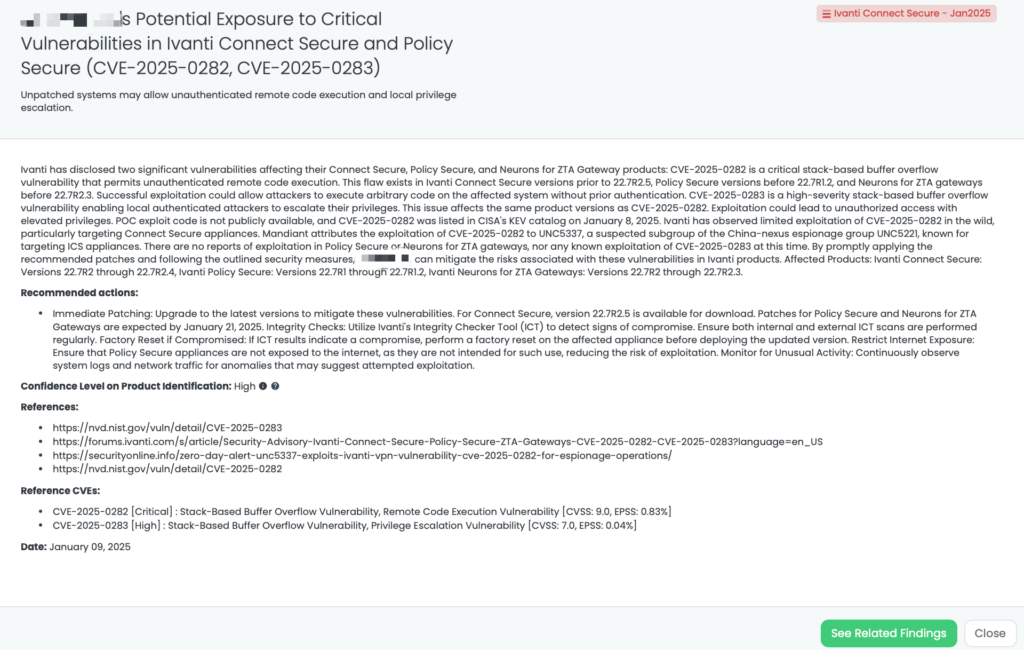
- Ivanti Connect Secure – Jan2025: CVE-2025-0282, CVE-2025-0283, Stack-Based Buffer Overflow Vulnerability, Remote Code Execution Vulnerability, Privilege Escalation Vulnerability in Ivanti Connect Secure, Policy Secure, and Ivanti Neurons for ZTA gateways.
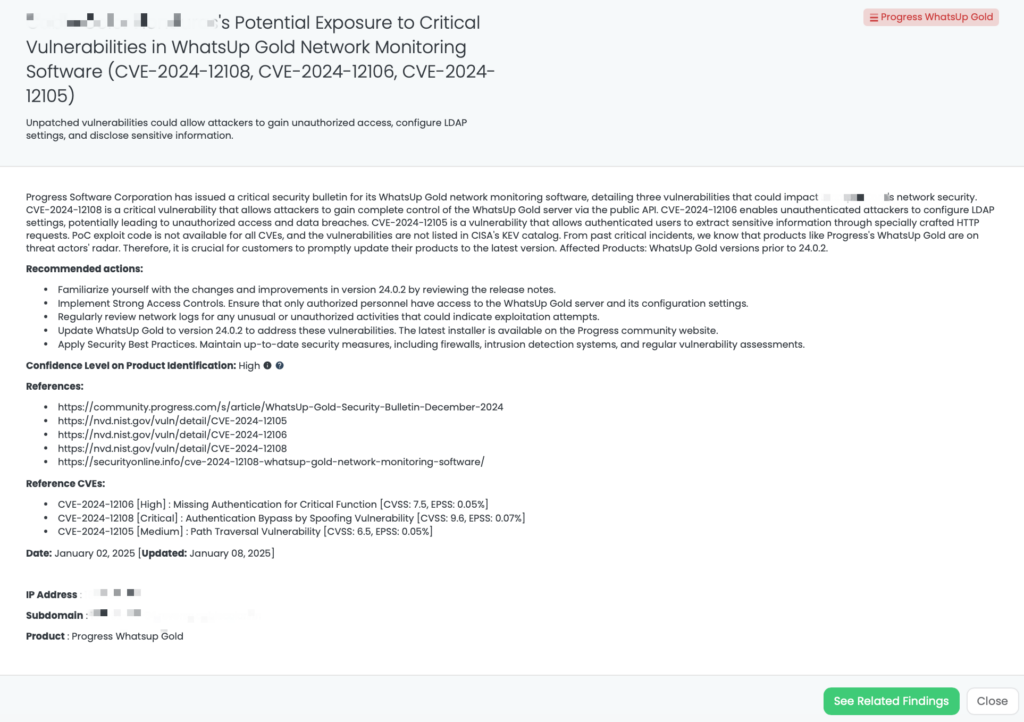
- Progress WhatsUp Gold: CVE-2024-12108, CVE-2024-12106, CVE-2024-12105, Authentication Bypass by Spoofing Vulnerability, Missing Authentication for Critical Function, and Path Traversal Vulnerability in Progress WhatsUp Gold.
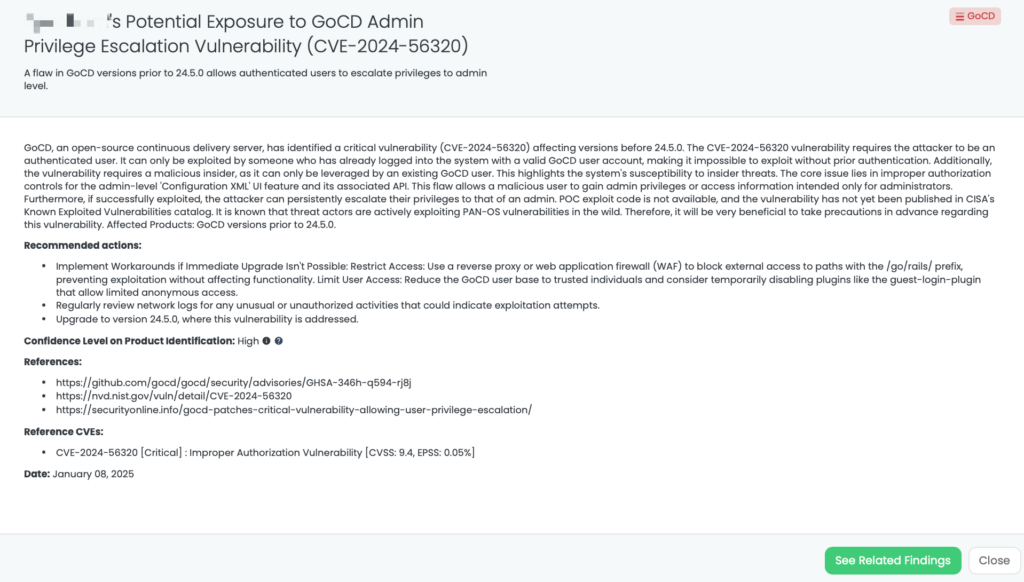
- GoCD: CVE-2024-56320, Improper Authorization Vulnerability in GoCD.
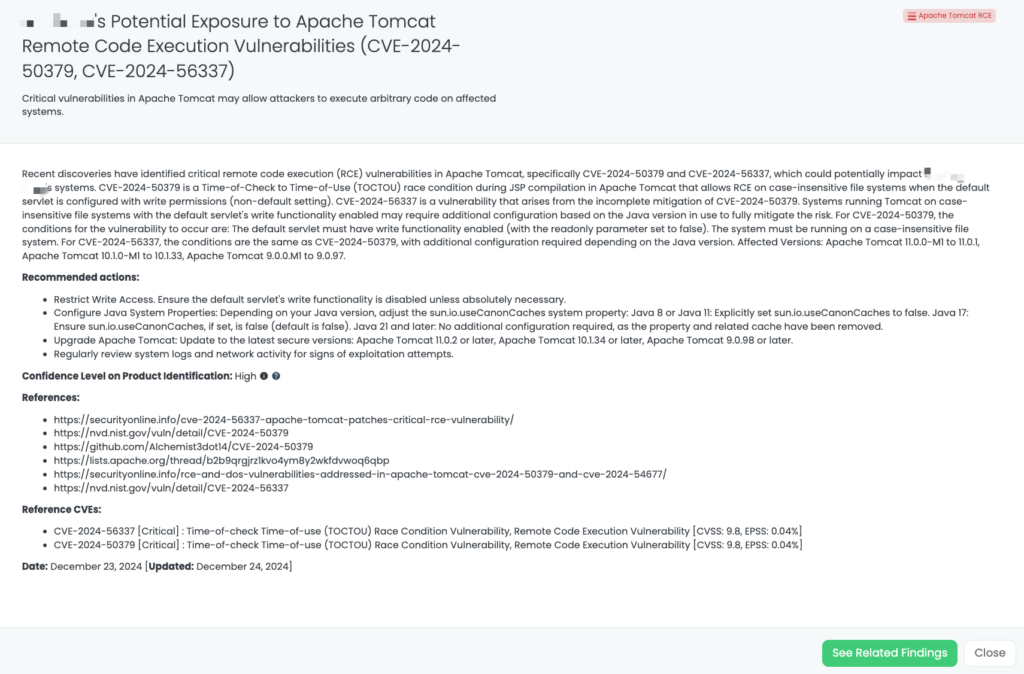
- Apache Tomcat RCE: CVE-2024-56337, CVE-2024-50379, Time-of-check Time-of-use (TOCTOU) Race Condition Vulnerability, Remote Code Execution Vulnerability in Apache Tomcat.
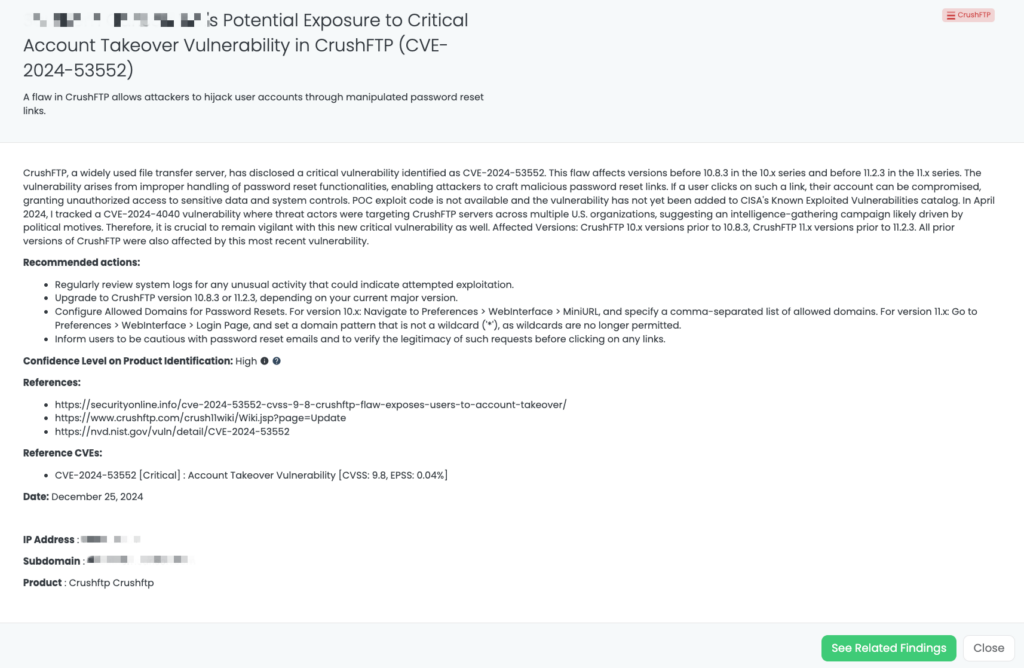
- CrushFTP: CVE-2024-53552, Account Takeover Vulnerability in CrushFTP.
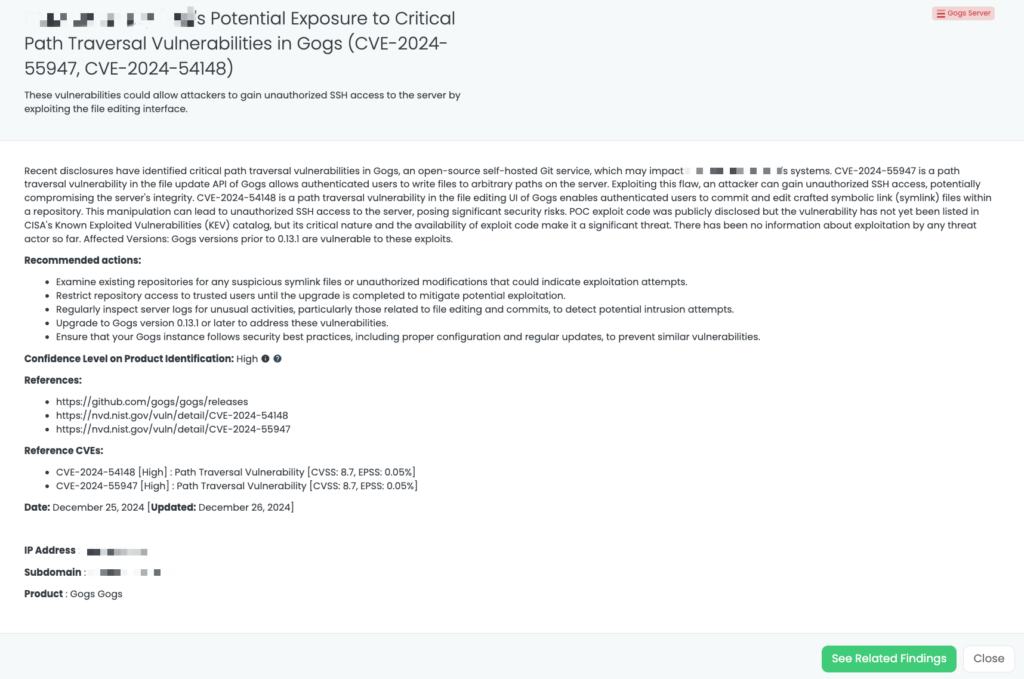
- Gogs Server: CVE-2024-55947, CVE-2024-54148, Path Traversal Vulnerability in Gogs Server.
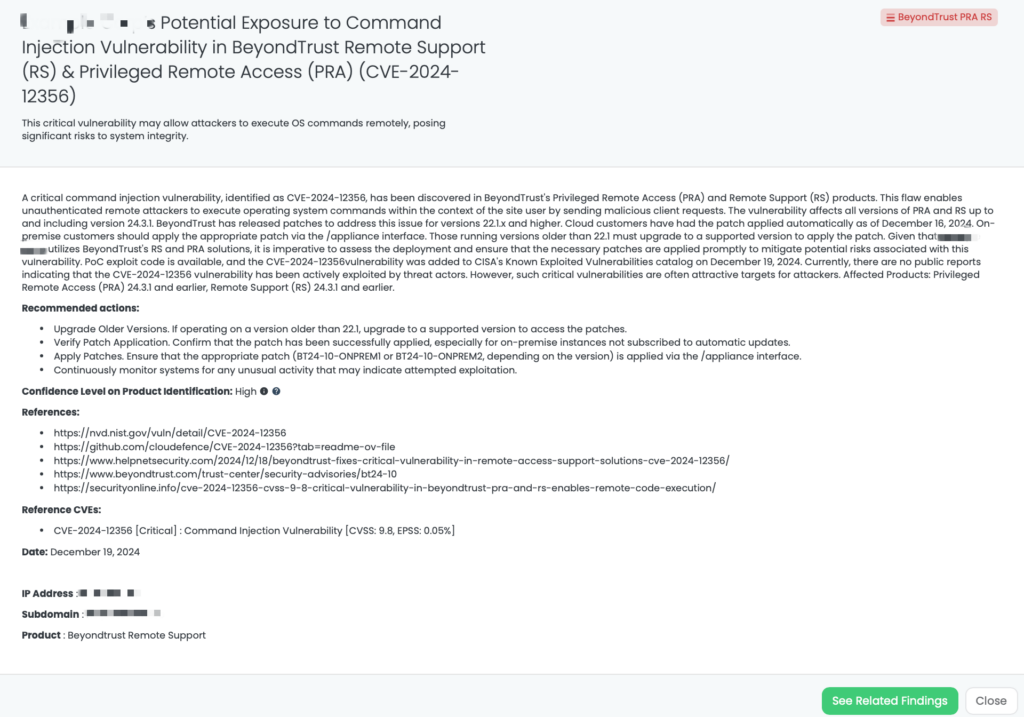
- BeyondTrust PRA RS: CVE-2024-12356, Command Injection Vulnerability in BeyondTrust’s Privileged Remote Access (PRA), Remote Support (RS).
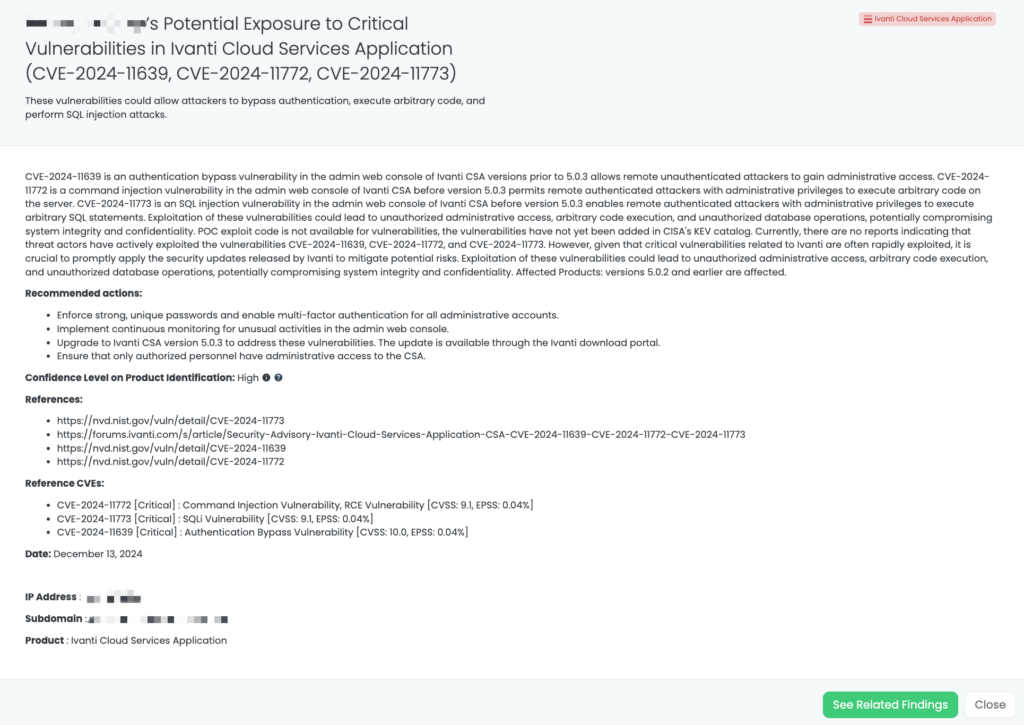
- Ivanti Cloud Services Application: CVE-2024-11639, CVE-2024-11772, CVE-2024-11772, Authentication Bypass Vulnerability Command Injection Vulnerability, and RCE Vulnerability SQLi Vulnerability in Ivanti Cloud Services Application.
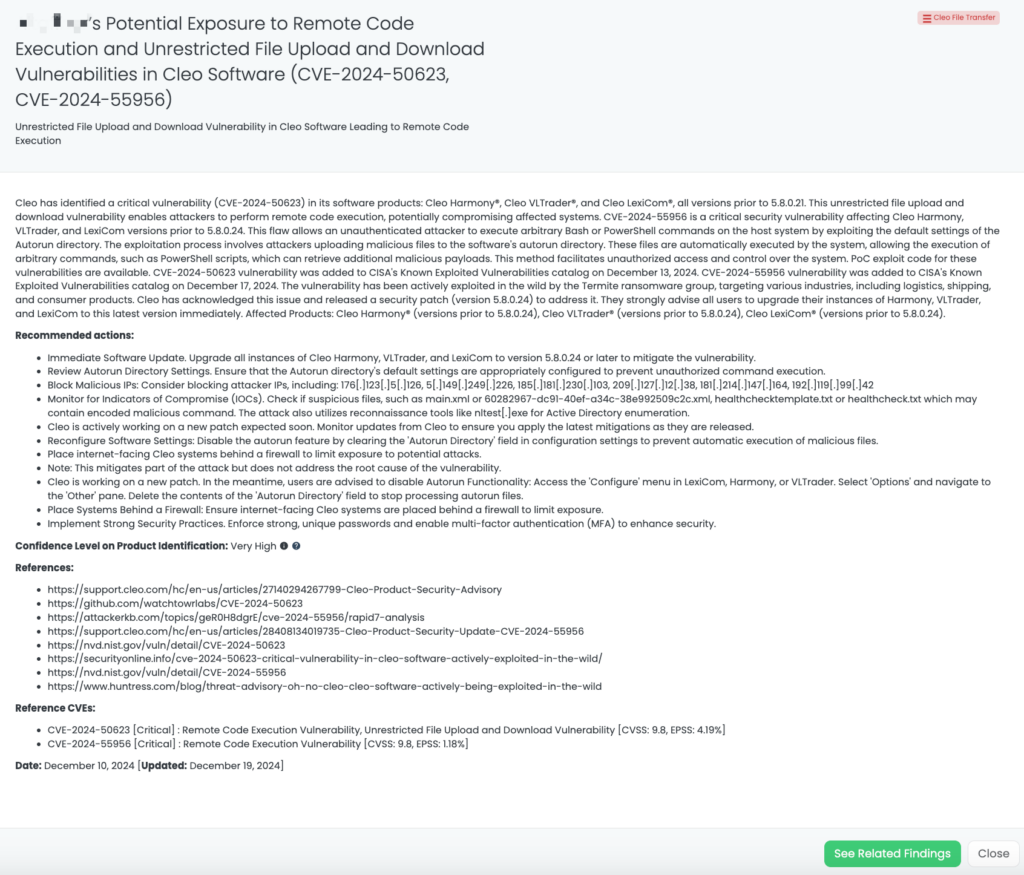
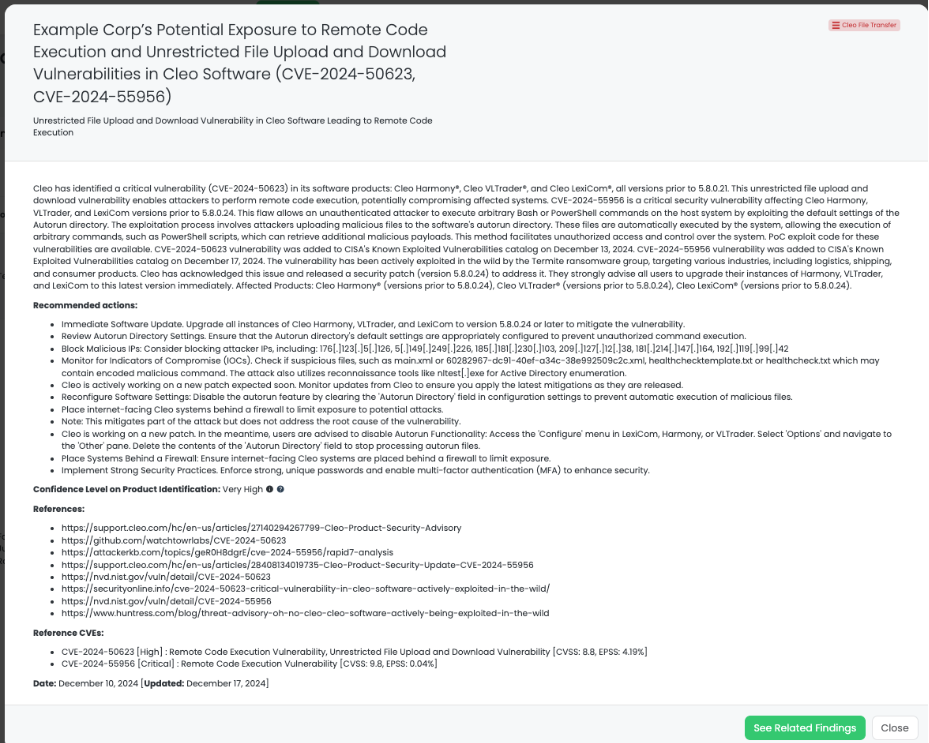
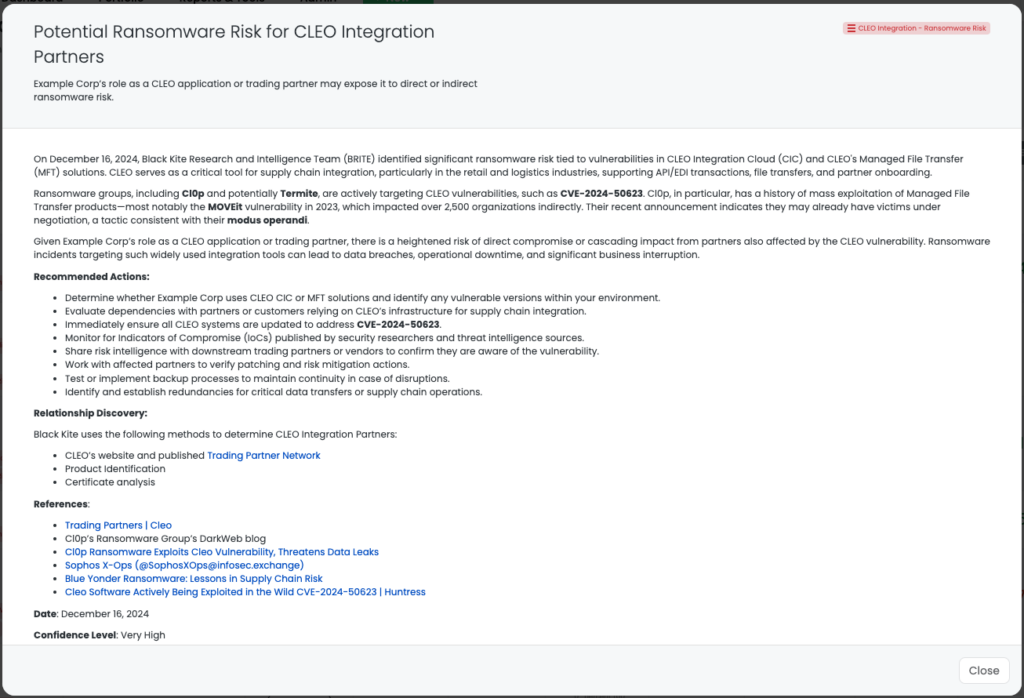
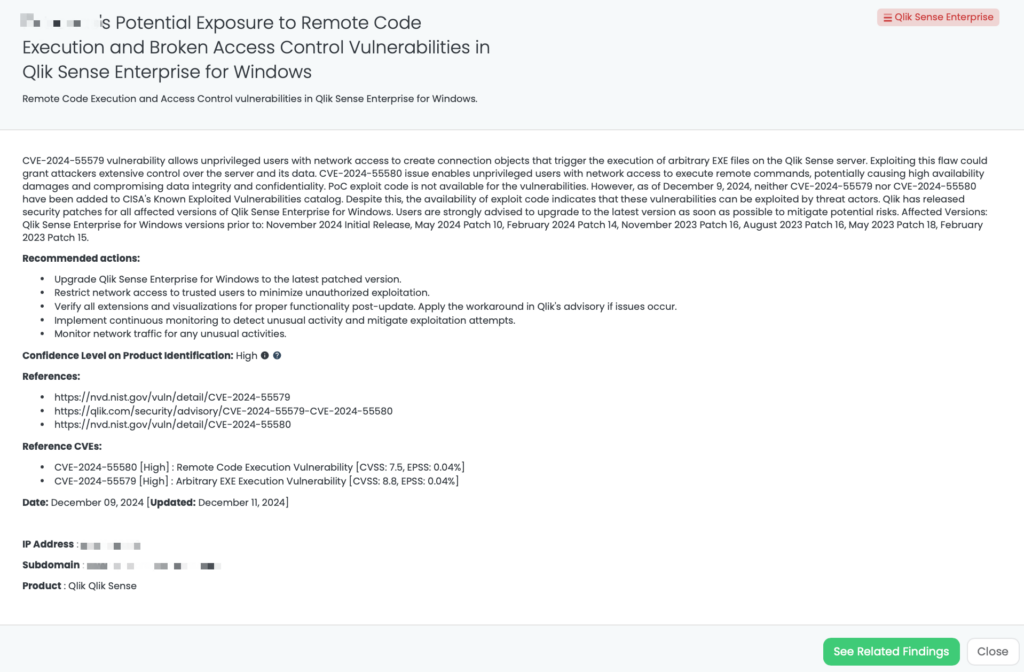
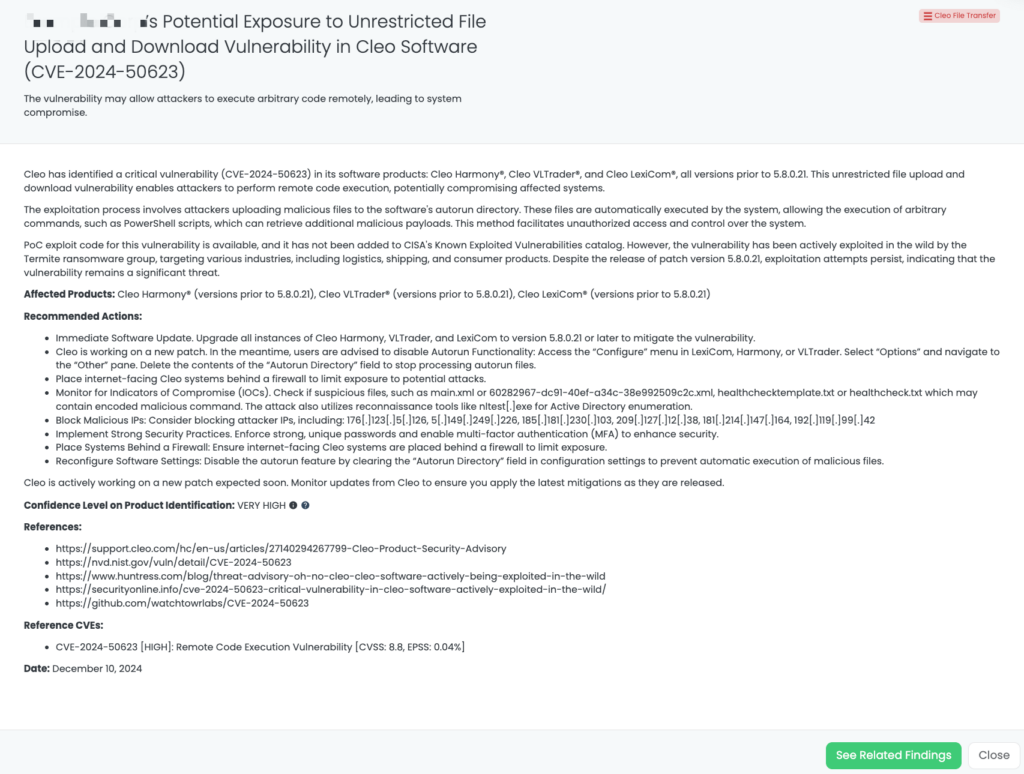
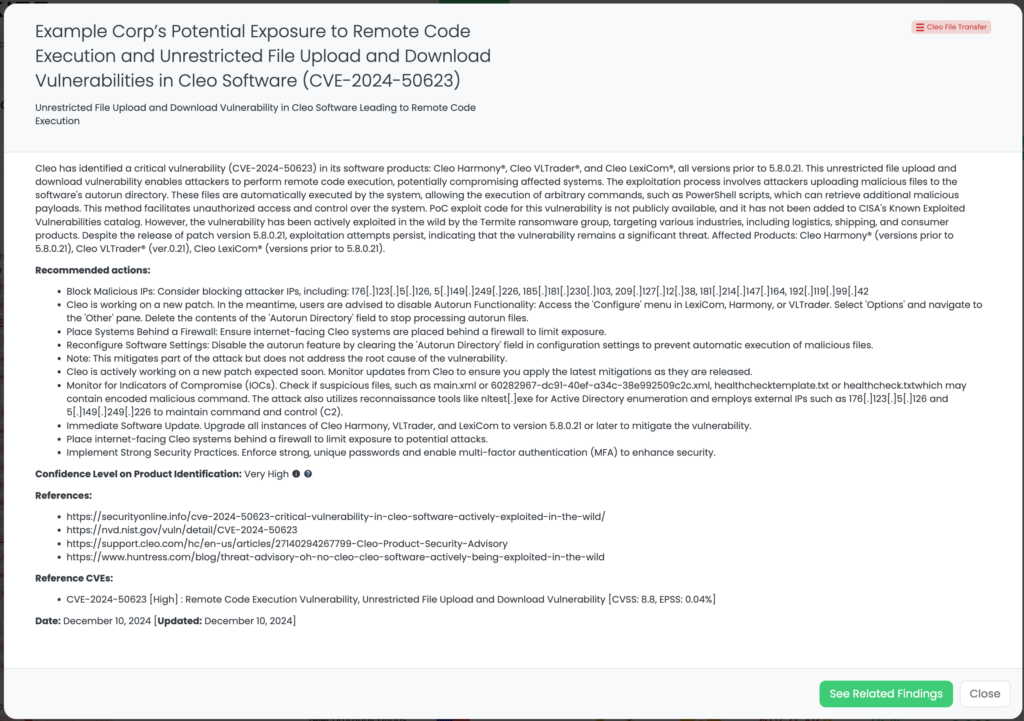
- Cleo File Transfer: CVE-2024-50623, CVE-2024-55956, Remote Code Execution Vulnerability, Unrestricted File Upload and Download Vulnerability in Cleo Harmony, VLTrader, LexiCom.
- Qlik Sense Enterprise: CVE-2024-55579, CVE-2024-55580, Arbitrary EXE Execution Vulnerability Remote Code Execution Vulnerability in Qlik Sense Enterprise.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-21598
https://nvd.nist.gov/vuln/detail/CVE-2024-12086
https://nvd.nist.gov/vuln/detail/CVE-2024-12087
https://nvd.nist.gov/vuln/detail/CVE-2024-12747
https://nvd.nist.gov/vuln/detail/CVE-2024-12084
https://nvd.nist.gov/vuln/detail/CVE-2024-12088
https://nvd.nist.gov/vuln/detail/CVE-2024-12085
https://www.openwall.com/lists/oss-security/2025/01/14/3
https://nvd.nist.gov/vuln/detail/CVE-2024-57726
https://nvd.nist.gov/vuln/detail/CVE-2024-57727
https://nvd.nist.gov/vuln/detail/CVE-2024-57728
https://simple-help.com/kb—security-vulnerabilities-01-2025#upgrading-to-v5-5-8
https://thehackernews.com/2025/01/critical-simplehelp-flaws-allow-file.html
https://securityonline.info/simplehelp-urgents-to-patch-critical-security-vulnerabilities
https://thehackernews.com/2023/04/iranian-hackers-using-simplehelp-remote.html
The post FOCUS FRIDAY: Third-Party Risks From Critical Juniper Junos, Rsync, and SimpleHelp Vulnerabilities appeared first on Black Kite.