Replacement Theology is not Supported by KJB, Grok and danwillie
 Replacement Theology is not Supported by KJB, Grok and danwillie.
Replacement Theology is not Supported by KJB, Grok and danwillie.  Replacement Theology is not Supported by KJB, Grok and danwillie.
Replacement Theology is not Supported by KJB, Grok and danwillie.  Great clip, and as a believer I must point out that the drama in the clip isn't hard to believe but does add to the account of what the bible says. One needs to read the accounts in Mathew, Mark. Luke and John. But for us Gentiles Paul's epistle provide much more enlightenment.
Great clip, and as a believer I must point out that the drama in the clip isn't hard to believe but does add to the account of what the bible says. One needs to read the accounts in Mathew, Mark. Luke and John. But for us Gentiles Paul's epistle provide much more enlightenment. 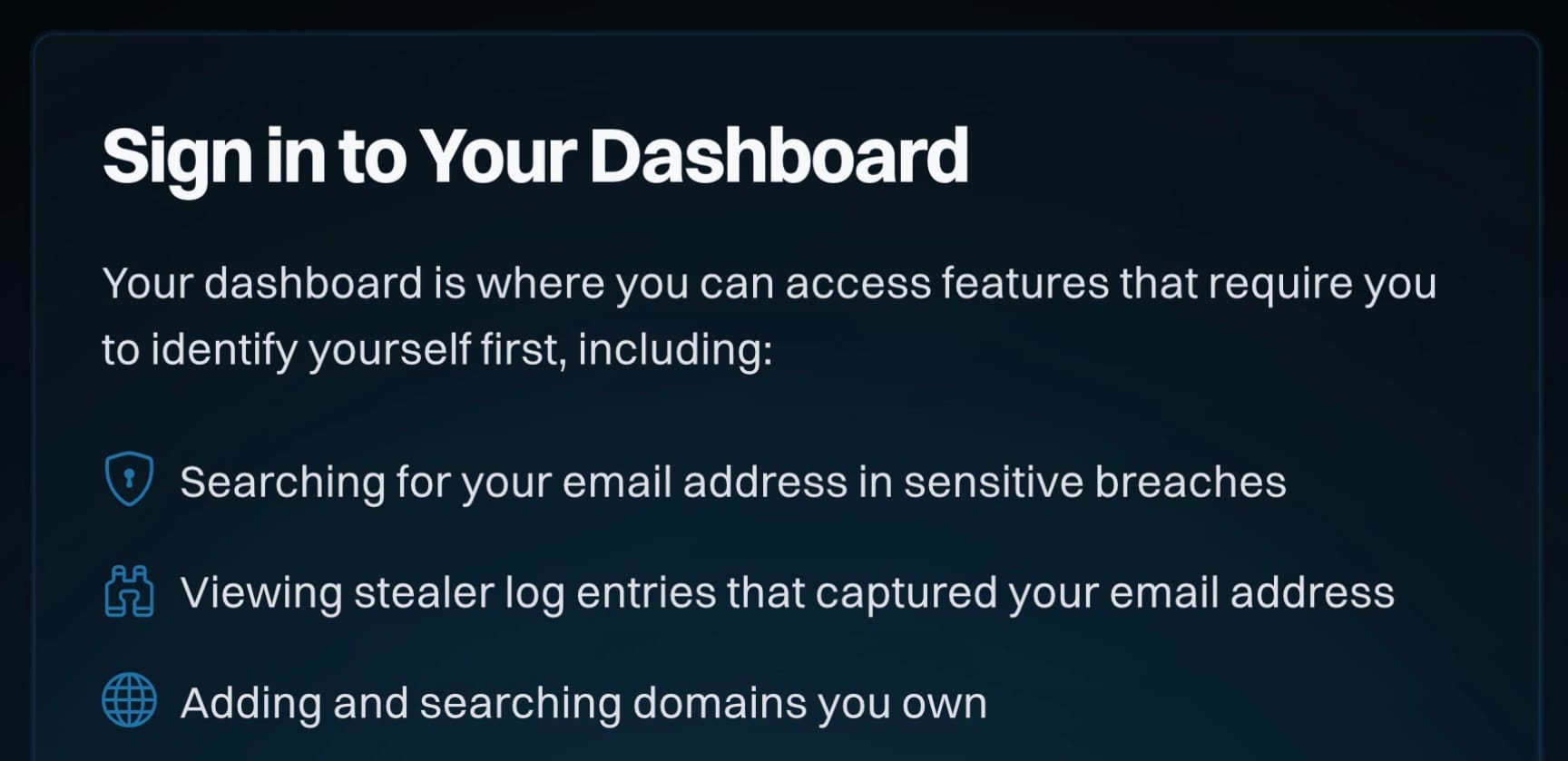
How do seemingly little things manage to consume so much time?! We had a suggestion this week that instead of being able to login to the new HIBP website, you should instead be able to log in. This initially confused me because I've been used to logging on to things for decades:
So, I went and signed in (yep, different again) to X and asked the masses what the correct term was:
When accessing your @haveibeenpwned dashboard, which of the following should you do? Preview screen for reference: https://t.co/9gqfr8hZrY
— Troy Hunt (@troyhunt) April 23, 2025
Which didn't result in a conclusive victor, so, I started browsing around.
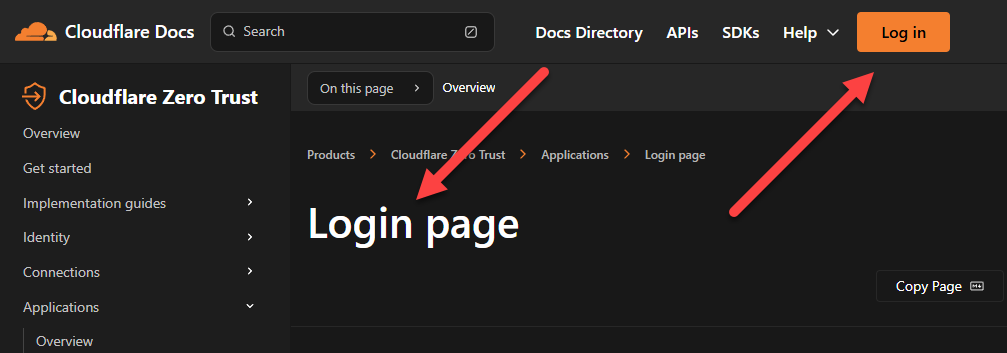
Cloudflare's Zero Trust docs contain information about customising the login page, which I assume you can do once you log in:
Another, uh, "popular" site prompts you to log in:
After which you're invited to sign in:
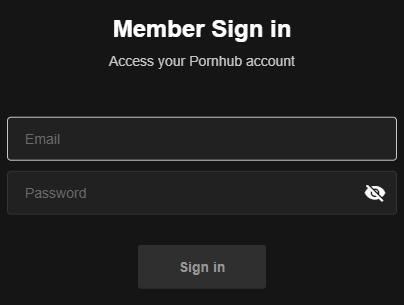
You can log in to Canva, which is clearly indicated by the HTML title, which suggests you're on the login page:
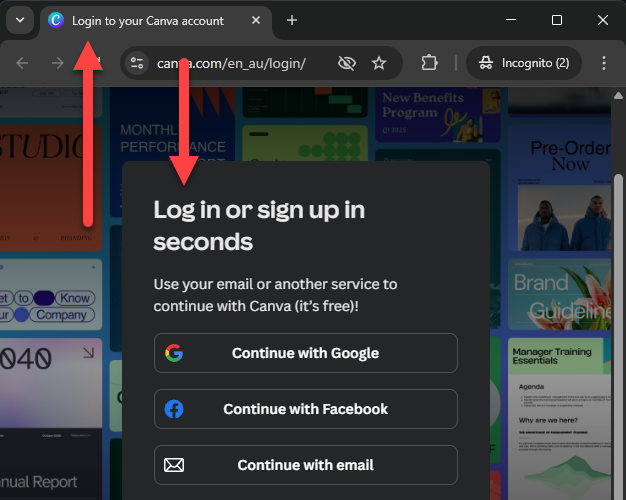
You can log on to the Commonwealth Bank down here in Australia:

But the login page for ANZ bank requires to log in, unless you've forgotten your login details:
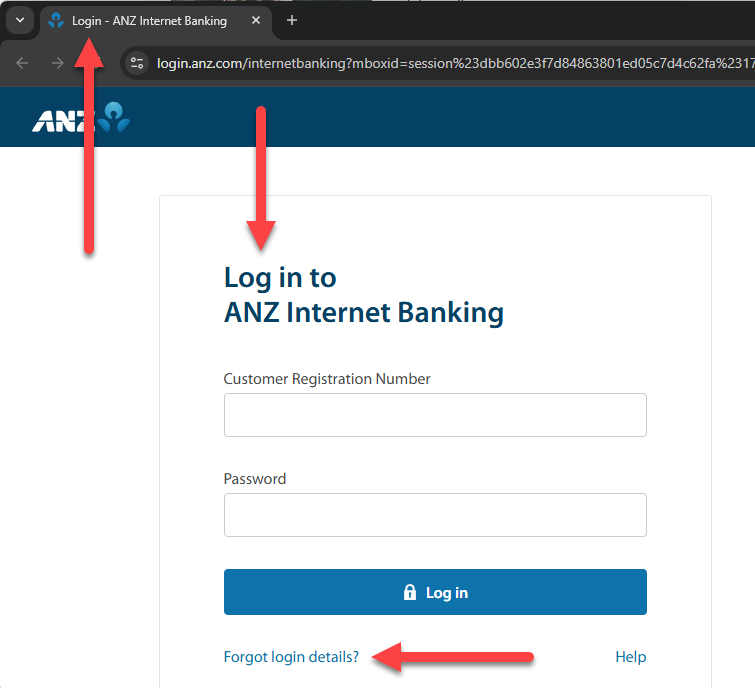
Ah, but many of these are just the difference between the noun "login" (the page is a thing) and the verb "log in" (when you perform an action), right? Well... depends who you bank with 🤷♂️
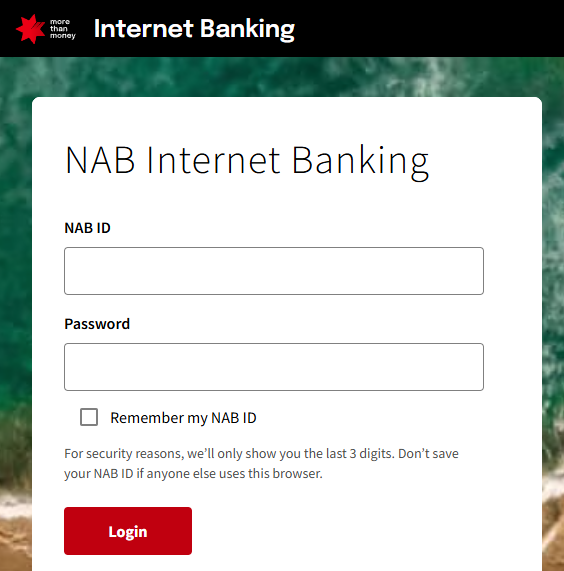
And maybe you don't log in or login at all:
Finally, from the darkness of seemingly interchangeable terms that may or may not violate principles of English language, emerged a pattern. You also sign in to Google:
And Microsoft:

And Amazon:
And Yahoo:

And, as I mentioned earlier, X:
And now, Have I Been Pwned:

There are some notable exceptions (Facebook and ChatGPT, for example), but "sign in" did emerge as the frontrunner among the world's most popular sites. If I really start to overthink it, I do feel that "log[whatever]" implies something different to why we authenticate to systems today and is more a remnant of a bygone era. But frankly, that argument is probably no more valid than whether you're doing a verb thing or a noun thing.

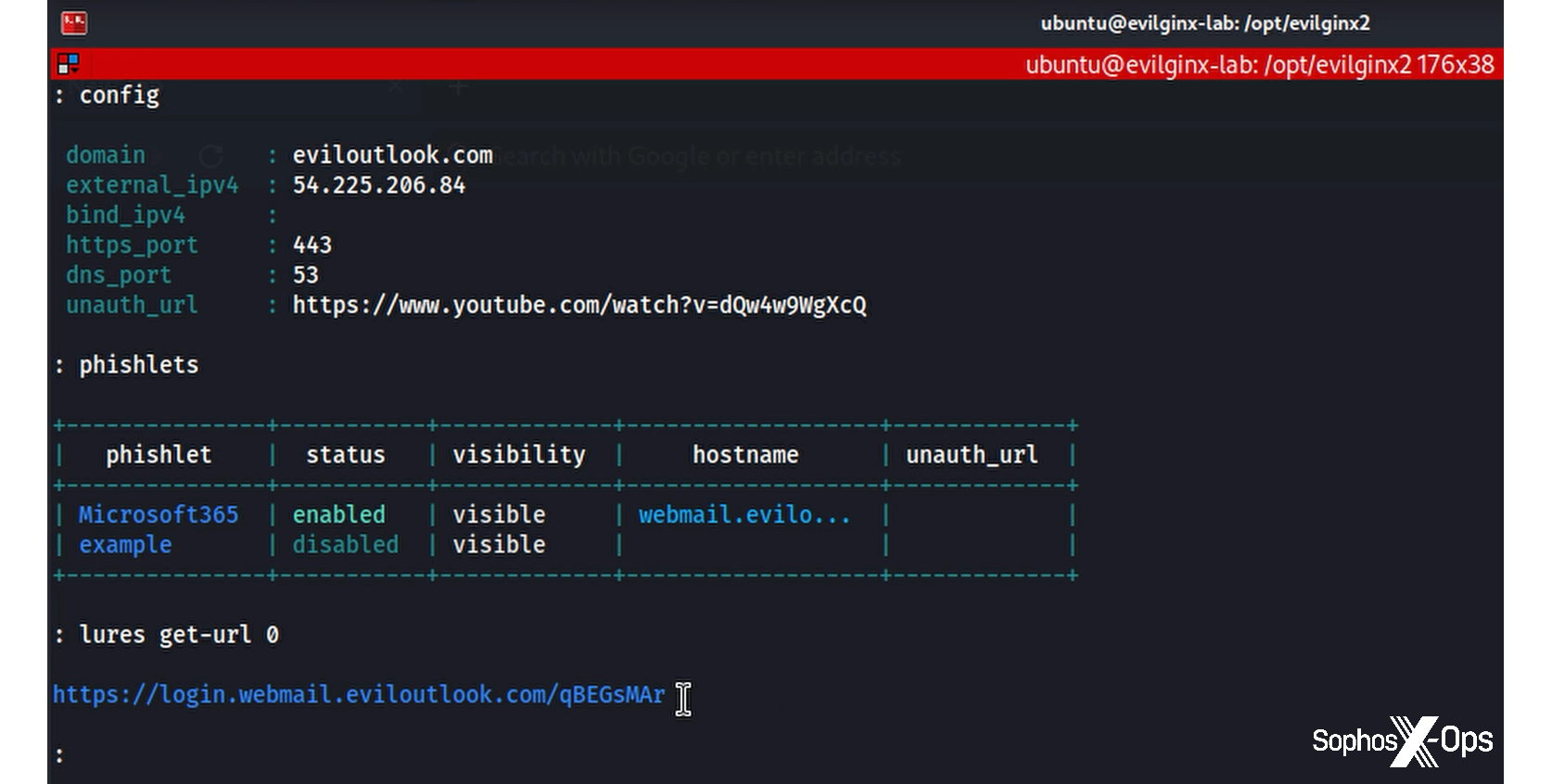
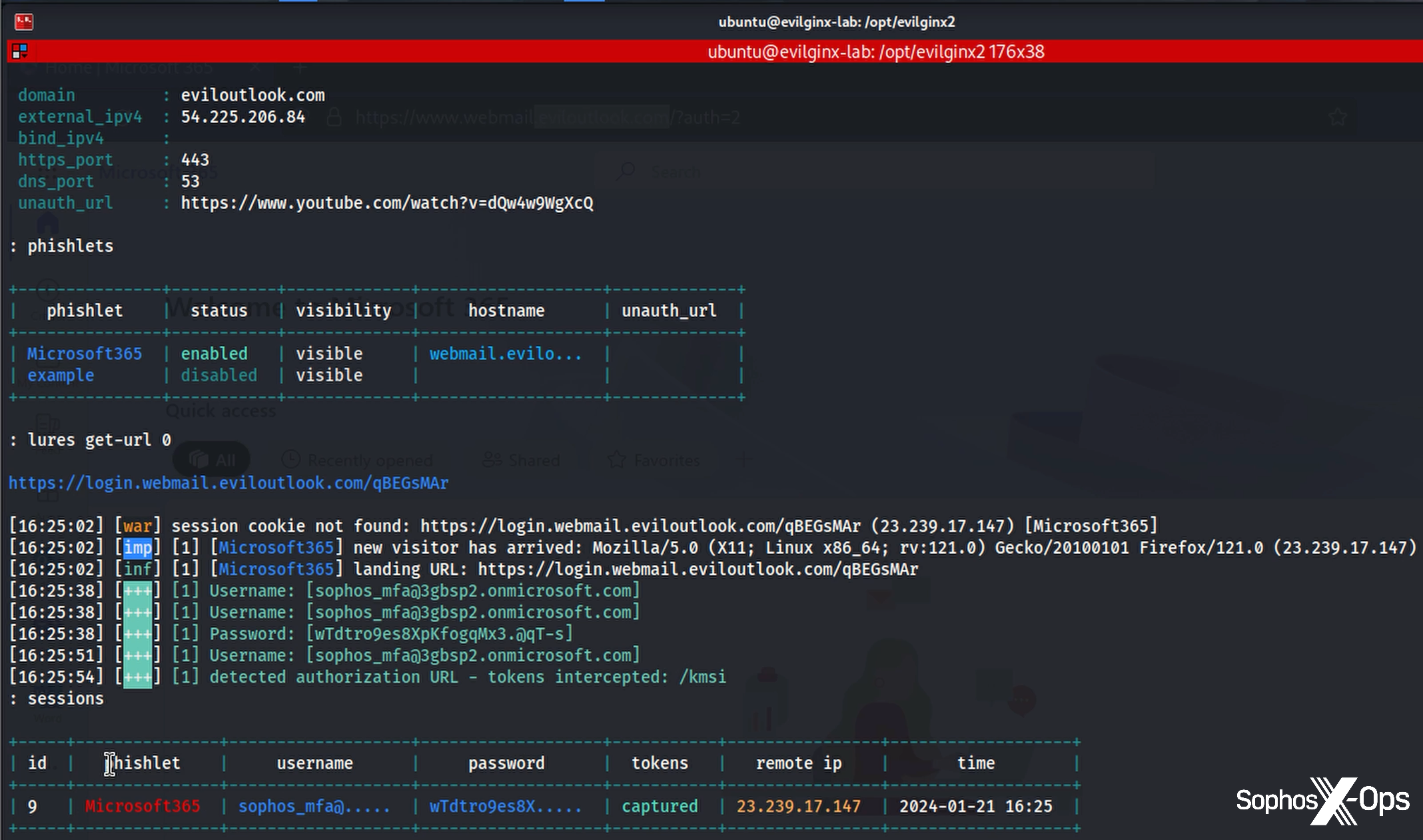


The U.S. government today unsealed criminal charges against 16 individuals accused of operating and selling DanaBot, a prolific strain of information-stealing malware that has been sold on Russian cybercrime forums since 2018. The FBI says a newer version of DanaBot was used for espionage, and that many of the defendants exposed their real-life identities after accidentally infecting their own systems with the malware.

DanaBot’s features, as promoted on its support site. Image: welivesecurity.com.
Initially spotted in May 2018 by researchers at the email security firm Proofpoint, DanaBot is a malware-as-a-service platform that specializes in credential theft and banking fraud.
Today, the U.S. Department of Justice unsealed a criminal complaint and indictment from 2022, which said the FBI identified at least 40 affiliates who were paying between $3,000 and $4,000 a month for access to the information stealer platform.
The government says the malware infected more than 300,000 systems globally, causing estimated losses of more than $50 million. The ringleaders of the DanaBot conspiracy are named as Aleksandr Stepanov, 39, a.k.a. “JimmBee,” and Artem Aleksandrovich Kalinkin, 34, a.k.a. “Onix”, both of Novosibirsk, Russia. Kalinkin is an IT engineer for the Russian state-owned energy giant Gazprom. His Facebook profile name is “Maffiozi.”
According to the FBI, there were at least two major versions of DanaBot; the first was sold between 2018 and June 2020, when the malware stopped being offered on Russian cybercrime forums. The government alleges that the second version of DanaBot — emerging in January 2021 — was provided to co-conspirators for use in targeting military, diplomatic and non-governmental organization computers in several countries, including the United States, Belarus, the United Kingdom, Germany, and Russia.
“Unindicted co-conspirators would use the Espionage Variant to compromise computers around the world and steal sensitive diplomatic communications, credentials, and other data from these targeted victims,” reads a grand jury indictment dated Sept. 20, 2022. “This stolen data included financial transactions by diplomatic staff, correspondence concerning day-to-day diplomatic activity, as well as summaries of a particular country’s interactions with the United States.”
The indictment says the FBI in 2022 seized servers used by the DanaBot authors to control their malware, as well as the servers that stored stolen victim data. The government said the server data also show numerous instances in which the DanaBot defendants infected their own PCs, resulting in their credential data being uploaded to stolen data repositories that were seized by the feds.
“In some cases, such self-infections appeared to be deliberately done in order to test, analyze, or improve the malware,” the criminal complaint reads. “In other cases, the infections seemed to be inadvertent – one of the hazards of committing cybercrime is that criminals will sometimes infect themselves with their own malware by mistake.”
Image: welivesecurity.com
A statement from the DOJ says that as part of today’s operation, agents with the Defense Criminal Investigative Service (DCIS) seized the DanaBot control servers, including dozens of virtual servers hosted in the United States. The government says it is now working with industry partners to notify DanaBot victims and help remediate infections. The statement credits a number of security firms with providing assistance to the government, including ESET, Flashpoint, Google, Intel 471, Lumen, PayPal, Proofpoint, Team CYMRU, and ZScaler.
It’s not unheard of for financially-oriented malicious software to be repurposed for espionage. A variant of the ZeuS Trojan, which was used in countless online banking attacks against companies in the United States and Europe between 2007 and at least 2015, was for a time diverted to espionage tasks by its author.
As detailed in this 2015 story, the author of the ZeuS trojan created a custom version of the malware to serve purely as a spying machine, which scoured infected systems in Ukraine for specific keywords in emails and documents that would likely only be found in classified documents.
The public charging of the 16 DanaBot defendants comes a day after Microsoft joined a slew of tech companies in disrupting the IT infrastructure for another malware-as-a-service offering — Lumma Stealer, which is likewise offered to affiliates under tiered subscription prices ranging from $250 to $1,000 per month. Separately, Microsoft filed a civil lawsuit to seize control over 2,300 domain names used by Lumma Stealer and its affiliates.
Further reading:
Danabot: Analyzing a Fallen Empire
ZScaler blog: DanaBot Launches DDoS Attack Against the Ukrainian Ministry of Defense
Flashpoint: Operation Endgame DanaBot Malware
Team CYMRU: Inside DanaBot’s Infrastructure: In Support of Operation Endgame II
March 2022 criminal complaint v. Artem Aleksandrovich Kalinkin
September 2022 grand jury indictment naming the 16 defendants
An employee at Elon Musk’s artificial intelligence company xAI leaked a private key on GitHub that for the past two months could have allowed anyone to query private xAI large language models (LLMs) which appear to have been custom made for working with internal data from Musk’s companies, including SpaceX, Tesla and Twitter/X, KrebsOnSecurity has learned.

Image: Shutterstock, @sdx15.
Philippe Caturegli, “chief hacking officer” at the security consultancy Seralys, was the first to publicize the leak of credentials for an x.ai application programming interface (API) exposed in the GitHub code repository of a technical staff member at xAI.
Caturegli’s post on LinkedIn caught the attention of researchers at GitGuardian, a company that specializes in detecting and remediating exposed secrets in public and proprietary environments. GitGuardian’s systems constantly scan GitHub and other code repositories for exposed API keys, and fire off automated alerts to affected users.
GitGuardian’s Eric Fourrier told KrebsOnSecurity the exposed API key had access to several unreleased models of Grok, the AI chatbot developed by xAI. In total, GitGuardian found the key had access to at least 60 fine-tuned and private LLMs.
“The credentials can be used to access the X.ai API with the identity of the user,” GitGuardian wrote in an email explaining their findings to xAI. “The associated account not only has access to public Grok models (grok-2-1212, etc) but also to what appears to be unreleased (grok-2.5V), development (research-grok-2p5v-1018), and private models (tweet-rejector, grok-spacex-2024-11-04).”
Fourrier found GitGuardian had alerted the xAI employee about the exposed API key nearly two months ago — on March 2. But as of April 30, when GitGuardian directly alerted xAI’s security team to the exposure, the key was still valid and usable. xAI told GitGuardian to report the matter through its bug bounty program at HackerOne, but just a few hours later the repository containing the API key was removed from GitHub.
“It looks like some of these internal LLMs were fine-tuned on SpaceX data, and some were fine-tuned with Tesla data,” Fourrier said. “I definitely don’t think a Grok model that’s fine-tuned on SpaceX data is intended to be exposed publicly.”
xAI did not respond to a request for comment. Nor did the 28-year-old xAI technical staff member whose key was exposed.
Carole Winqwist, chief marketing officer at GitGuardian, said giving potentially hostile users free access to private LLMs is a recipe for disaster.
“If you’re an attacker and you have direct access to the model and the back end interface for things like Grok, it’s definitely something you can use for further attacking,” she said. “An attacker could it use for prompt injection, to tweak the (LLM) model to serve their purposes, or try to implant code into the supply chain.”
The inadvertent exposure of internal LLMs for xAI comes as Musk’s so-called Department of Government Efficiency (DOGE) has been feeding sensitive government records into artificial intelligence tools. In February, The Washington Post reported DOGE officials were feeding data from across the Education Department into AI tools to probe the agency’s programs and spending.
The Post said DOGE plans to replicate this process across many departments and agencies, accessing the back-end software at different parts of the government and then using AI technology to extract and sift through information about spending on employees and programs.
“Feeding sensitive data into AI software puts it into the possession of a system’s operator, increasing the chances it will be leaked or swept up in cyberattacks,” Post reporters wrote.
Wired reported in March that DOGE has deployed a proprietary chatbot called GSAi to 1,500 federal workers at the General Services Administration, part of an effort to automate tasks previously done by humans as DOGE continues its purge of the federal workforce.
A Reuters report last month said Trump administration officials told some U.S. government employees that DOGE is using AI to surveil at least one federal agency’s communications for hostility to President Trump and his agenda. Reuters wrote that the DOGE team has heavily deployed Musk’s Grok AI chatbot as part of their work slashing the federal government, although Reuters said it could not establish exactly how Grok was being used.
Caturegli said while there is no indication that federal government or user data could be accessed through the exposed x.ai API key, these private models are likely trained on proprietary data and may unintentionally expose details related to internal development efforts at xAI, Twitter, or SpaceX.
“The fact that this key was publicly exposed for two months and granted access to internal models is concerning,” Caturegli said. “This kind of long-lived credential exposure highlights weak key management and insufficient internal monitoring, raising questions about safeguards around developer access and broader operational security.”
Apple has resumed advertising on X for the first time since pausing ads more than a year ago, following the trend of major advertising "pausing" their spending on Elon Musk's platform due supposedly to concerns about "brand safety."
The post Apple Resumes Advertising on Elon Musk’s X After Year-Long Absence appeared first on Breitbart.
Elon Musk's X has agreed to pay approximately $10 million to settle a lawsuit filed by former President Donald Trump.
The post Elon Musk’s X to Pay Donald Trump $10 Million Settling Censorship Lawsuit appeared first on Breitbart.
In mid-March 2024, KrebsOnSecurity revealed that the founder of the personal data removal service Onerep also founded dozens of people-search companies. Shortly after that investigation was published, Mozilla said it would stop bundling Onerep with the Firefox browser and wind down its partnership with the company. But nearly a year later, Mozilla is still promoting it to Firefox users.
Mozilla offers Onerep to Firefox users on a subscription basis as part of Mozilla Monitor Plus. Launched in 2018 under the name Firefox Monitor, Mozilla Monitor also checks data from the website Have I Been Pwned? to let users know when their email addresses or password are leaked in data breaches.
The ink on that partnership agreement had barely dried before KrebsOnSecurity published a story showing that Onerep’s Belarusian CEO and founder Dimitiri Shelest launched dozens of people-search services since 2010, including a still-active data broker called Nuwber that sells background reports on people. This seemed to contradict Onerep’s stated motto, “We believe that no one should compromise personal online security and get a profit from it.”
Shelest released a lengthy statement (PDF) wherein he acknowledged maintaining an ownership stake in Nuwber, a consumer data broker he founded in 2015 — around the same time he started Onerep.
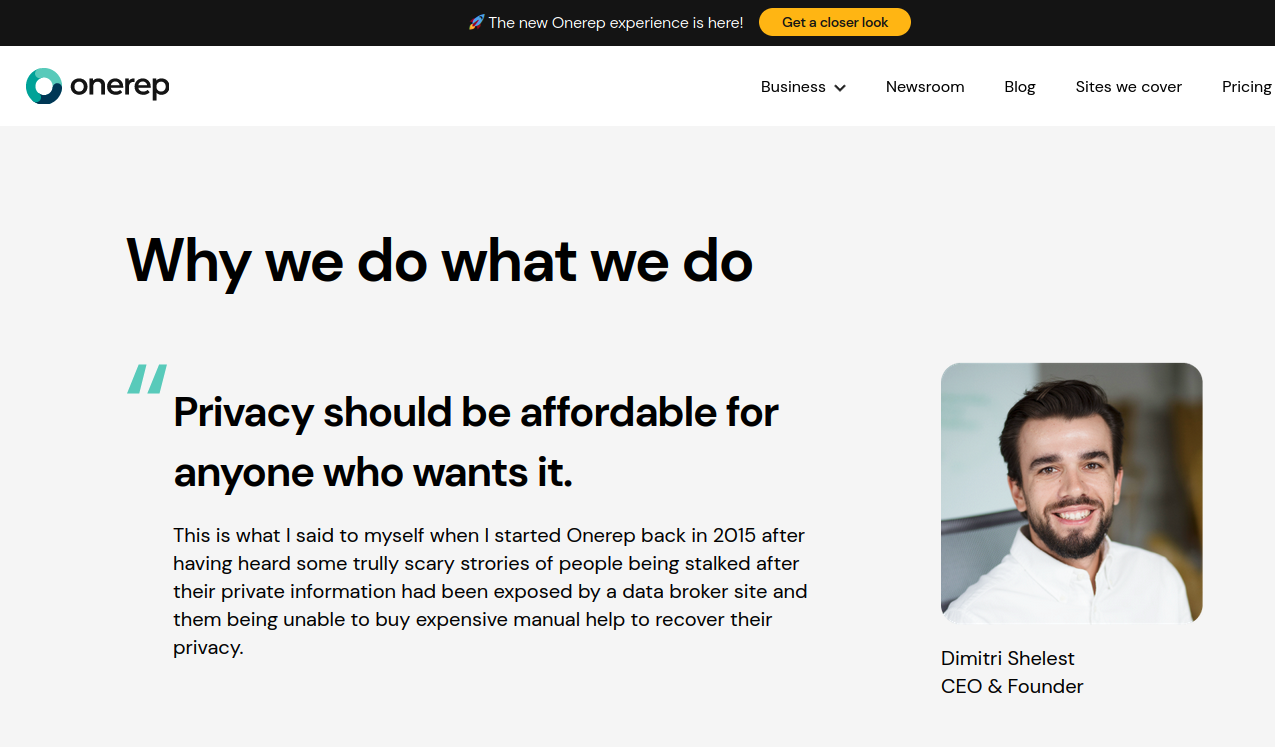
Onerep.com CEO and founder Dimitri Shelest, as pictured on the “about” page of onerep.com.
Shelest maintained that Nuwber has “zero cross-over or information-sharing with Onerep,” and said any other old domains that may be found and associated with his name are no longer being operated by him.
“I get it,” Shelest wrote. “My affiliation with a people search business may look odd from the outside. In truth, if I hadn’t taken that initial path with a deep dive into how people search sites work, Onerep wouldn’t have the best tech and team in the space. Still, I now appreciate that we did not make this more clear in the past and I’m aiming to do better in the future.”
When asked to comment on the findings, Mozilla said then that although customer data was never at risk, the outside financial interests and activities of Onerep’s CEO did not align with their values.
“We’re working now to solidify a transition plan that will provide customers with a seamless experience and will continue to put their interests first,” Mozilla said.
In October 2024, Mozilla published a statement saying the search for a different provider was taking longer than anticipated.
“While we continue to evaluate vendors, finding a technically excellent and values-aligned partner takes time,” Mozilla wrote. “While we continue this search, Onerep will remain the backend provider, ensuring that we can maintain uninterrupted services while we continue evaluating new potential partners that align more closely with Mozilla’s values and user expectations. We are conducting thorough diligence to find the right vendor.”
Asked for an update, Mozilla said the search for a replacement partner continues.
“The work’s ongoing but we haven’t found the right alternative yet,” Mozilla said in an emailed statement. “Our customers’ data remains safe, and since the product provides a lot of value to our subscribers, we’ll continue to offer it during this process.”
It’s a win-win for Mozilla that they’ve received accolades for their principled response while continuing to partner with Onerep almost a year later. But if it takes so long to find a suitable replacement, what does that say about the personal data removal industry itself?
Onerep appears to be working in partnership with another problematic people-search service: Radaris, which has a history of ignoring opt-out requests or failing to honor them. A week before breaking the story about Onerep, KrebsOnSecurity published research showing the co-founders of Radaris were two native Russian brothers who’d built a vast network of affiliate marketing programs and consumer data broker services.
Lawyers for the Radaris co-founders threatened to sue KrebsOnSecurity unless that story was retracted in full, claiming the founders were in fact Ukrainian and that our reporting had defamed the brothers by associating them with the actions of Radaris. Instead, we published a follow-up investigation which showed that not only did the brothers from Russia create Radaris, for many years they issued press releases quoting a fictitious CEO seeking money from investors.
Several readers have shared emails they received from Radaris after attempting to remove their personal data, and those messages show Radaris has been promoting Onerep.
The New York State Department of Health issued a health advisory Wednesday about the emergence of a new strain of mpox (formerly monkeypox).
The first case of mpox clade Ib in New York State was confirmed in a symptomatic individual who had recently traveled from Africa.
The present risk to the public remains low, the department noted, and there are no additional known community cases of this strain in New York State currently.
IS MPOX THE NEXT COVID? INFECTIOUS DISEASE EXPERTS ADDRESS PANDEMIC POTENTIAL
State Health Commissioner Dr. James McDonald shared that the infected individual is under the care of a physician and isolated "until the full resolution of symptoms."
"There is no known local transmission of mpox clade Ib in the community where the individual lives or anywhere within New York State," he said in a statement.
McDonald added that the JYNNEOS vaccine, which is a two-dose preventative vaccine series for mpox, is "expected to be effective" against this new strain.
"[It is] available for individuals at risk with the standing order I signed last year," he noted. "There is no immediate risk to the general public."
For more Health articles, visit www.foxnews.com/health
The health department added in its advisory that individuals should inquire with their local pharmacy or healthcare provider about vaccine availability as they continue to "monitor and maintain the situation."
Mpox is "rarely fatal," according to the department, but can be dangerous for people with immunocompromising conditions, as well as older adults, young children and pregnant women.
Symptoms can include rashes that progress to "painful skin lesions," in addition to swollen lymph nodes, fever, sore throat, headaches, back pain, low energy and muscle aches, the department listed.
There is a "high likelihood of transmission" until these lesions scab over, which means infected individuals are encouraged to isolate until new skin forms at the lesion site.
Mpox can spread through close, intimate contact with sores, scabs or rashes, the department stated, as well as through the respiratory droplets, saliva or mucus of an infected person.
Those who plan to travel to areas with reported cases of mpox should consider being vaccinated with the two doses of JYNNEOS, experts recommend.
CLICK HERE TO SIGN UP FOR OUR HEALTH NEWSLETTER
Dr. Myles Druckman, global medical director at International SOS in California, told Fox News Digital that there have been reports of this strain in several countries in Central and Eastern Africa.
"We’re finding that other countries have also reported travel-associated cases of clade I, including Belgium, Canada, China, France, Germany, India, Ireland, Oman, Pakistan, South Sudan, Sweden, Thailand, the United Kingdom and Zimbabwe," he noted.
"It's important to recognize that cases of this strain are expected due to the ongoing outbreak in multiple countries and the risks associated with global travel."
Mpox can be infectious for up to four days before symptoms occur, but it is most contagious from the time symptoms appear until about two to four weeks later, according to Druckman.
The expert emphasized that vaccination is recommended for high-risk individuals, such as healthcare workers with high exposure or people with weakened immune systems.
"Prevention of mpox is mainly through vaccination and avoiding skin-to-skin contact with others – especially those with symptoms or visible outbreaks – and observing good personal hygiene and washing hands well and frequently," he added.
Red Seat Ventures, which hosts the likes of former Fox News stars Tucker Carlson and Megyn Kelly and popular true crime podcasts, has been acquired by Rupert Murdoch's Fox.
The post Rupert Murdoch’s Fox Acquires Podcast Network of Former Fox News Stars Tucker Carlson, Megyn Kelly appeared first on Breitbart.
Rapper and fashion mogul Kanye West deactivated his X account on Sunday following a three-day long posting spree.
The post Kanye West Deactivates X Account Following Wild Posting Frenzy, Thanks the Public for ‘Participating In This Social Experiment’ appeared first on Breitbart.
Actress Hannah Einbinder -- who stars in the HBO Max series "Hacks" -- delivered a climate change lecture during her acceptance speech at the Critics Choice Awards in Santa Monica on Friday, pointing the finger of blame directly at oil and gas companies.
The post HBO’s ‘Hacks’ Star Hannah Einbinder Delivers Climate Alarmism Lecture: ‘Really Dark Era of Climate Denial’ appeared first on Breitbart.
Laverne Cox, a transgender actor and star of Amazon Prime Video’s newest comedy "Clean Slate," claims America is "going backwards in so many ways" and says it's going to take people rising up to fight President's Donald Trump's agenda, including an executive order protecting minors from sex change drugs and surgeries.
The post Amazon’s ‘Clean Slate’ Star Laverne Cox: ‘Trans Identity Is Being Criminalized in This Country’ appeared first on Breitbart.